North Korean APT Group Kimsuky Targets Japanese Organizations with Stealthy Malware Campaign

Japanese organizations are being targeted by the notorious North Korean advanced persistent threat (APT) group, Kimsuky, in a sophisticated cyberespionage campaign. The Japan Computer Emergency Response Team Coordination Center (JPCERT/CC) confirmed attacks in March 2024, revealing the group’s tactics of impersonating security and diplomatic entities to deliver malicious payloads.
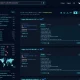
Kimsuky employs carefully crafted phishing emails containing zip files with hidden executable files disguised as harmless documents. Upon execution, these files initiate a multi-stage infection process, involving the download and execution of VBScript and PowerShell scripts from external sources.

Flow after the EXE file is executed | Image: JPCERT/CC
The malware then proceeds to collect sensitive information from the infected device, including system details, process lists, network information, file listings, and user account credentials. This data is then exfiltrated to a remote server controlled by the attackers.
JPCERT/CC’s analysis suggests that these actions are designed to assess the compromised environment, potentially determining if the target is a high-value entity or a sandboxed security research environment. If deemed valuable, the attackers deploy a keylogger to capture keystrokes and clipboard data, providing them with a continuous stream of confidential information.
This latest campaign against Japanese organizations aligns with Kimsuky‘s known tactics, techniques, and procedures (TTPs) observed in similar attacks targeting South Korea. The use of VBScript and PowerShell for malware delivery and the focus on intelligence gathering underscore the group’s persistent efforts to compromise sensitive targets and steal valuable information.
Japanese organizations are urged to exercise caution when dealing with emails from unknown or suspicious sources. Implementing robust email security measures, such as advanced threat protection and user awareness training, can significantly mitigate the risk of falling victim to these targeted attacks. Additionally, maintaining up-to-date security patches and conducting regular system audits are essential for identifying and remediating any potential compromises.