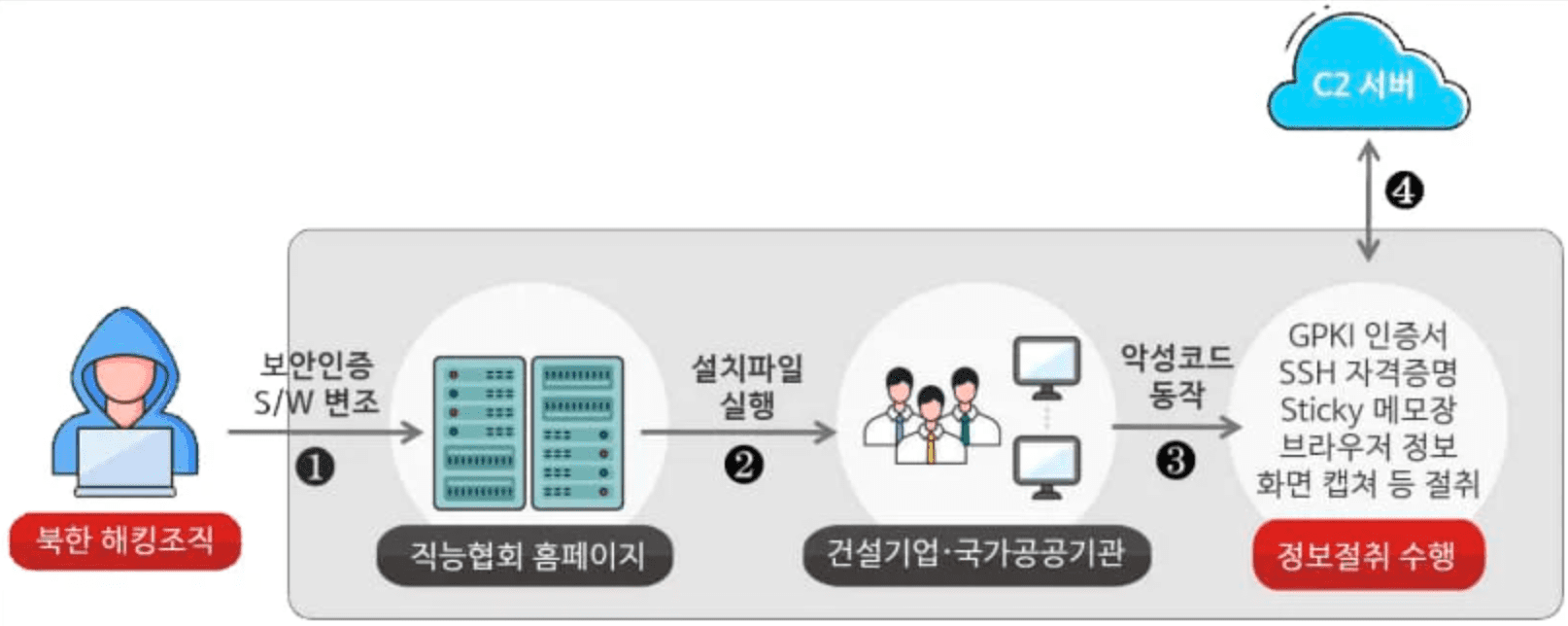
Kimsuky Supply Chain Attack Image Credit: NCSC
Cybercriminal groups supported by the North Korean government, such as Kimsuky (APT43) and Andariel (APT45), have recently escalated cyberattacks on South Korea’s construction and engineering sectors. This surge in attacks coincides with Kim Jong Un’s “20×10 Local Industry Development” policy, aimed at modernizing industrial facilities across North Korea.
The National Cybersecurity Center of South Korea (NCSC) and local intelligence agencies have issued a joint warning, noting that North Korean hackers are increasingly exploiting VPN update vulnerabilities to infiltrate target networks.
The warning also provides crucial details to help organizations prevent and minimize potential damage, as stolen data can be used to advance North Korea’s industrial and urban infrastructure.
In January 2024, the Kimsuky group executed a sophisticated supply chain attack through the website of a South Korean construction company. The hackers breached security authentication software and seized the NX_PRNMAN system.
Malware called “TrollAgent,” written in Go, infected the computers of government officials, public institution employees, and construction professionals who used the compromised site for authentication. Moreover, TrollAgent collected system information, took screenshots, and stole various sensitive data, including browser-stored passwords, GPKI certificates, SSH keys, and even FileZilla client data.
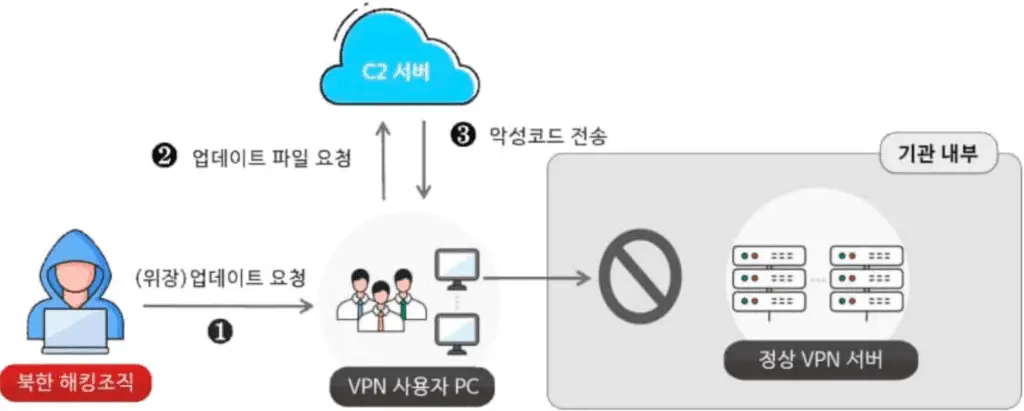
In the latest incident detected in April 2024, the Andariel group conducted a complex attack on South Korean construction and engineering companies by exploiting vulnerabilities in local VPNs and server security software. The attackers exploited gaps in client-server communication protocols, particularly focusing on updates insufficiently protected by authentication procedures.
Andariel’s method involved sending requests disguised as HTTP packets to users’ PCs, bypassing the verification process performed by the VPN client. They redirected requests to a malicious C2 server, masquerading it as a legitimate VPN server.
The dissemination of the DoraRAT malware, disguised as a software update, allowed Andariel hackers to gain remote control over infected machines, indicating a shift in North Korean cyberattack strategies and the need to fortify South Korea’s industrial infrastructure.
These incidents highlight the complexity and sophistication of North Korean cyber operations against South Korea’s infrastructure sectors. NCSC’s recommendations for protection include:
- Continuous security training for all members of vulnerable companies.
- Specialized training for IT personnel.
- Timely updates of operating systems, applications, and antivirus software.
- Implementation of strict approval policies for software deployment.
- Requirement of administrator authentication at the final deployment stage.
- Adherence to government cybersecurity guidelines and direct engagement with manufacturers for urgent actions.
- Utilization of supply chain security and software development guidelines from KISA.
The increase in cyberattacks from North Korea underscores the necessity of strengthening cybersecurity measures in South Korea. Protecting critical sectors requires not only technical preparedness but also continuous education and awareness among all employees.
Related Posts:
- Andariel: North Korea’s Cyber Threat Actor Steals Data, Launches Ransomware Attacks
- North Korean Hacker Indicted: Ransomware on Hospitals Funds Military Espionage
- North Korea’s APT45: From Espionage to Ransomware Extortion