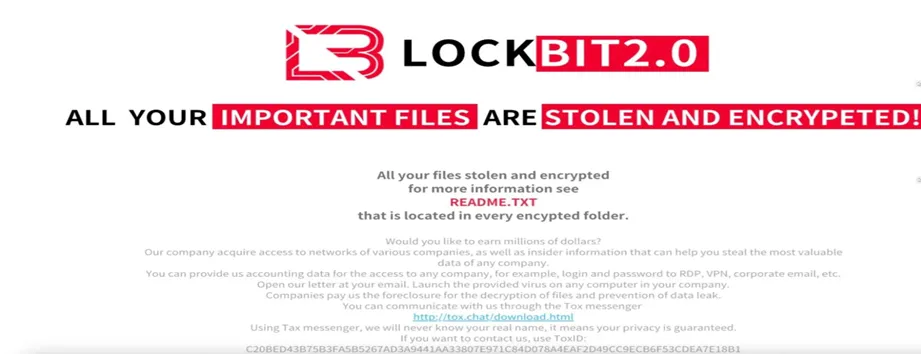
NotLockBit ransom note | Source: Qualys
Pranita Pradeep Kulkarni, Senior Engineer in Threat Research at Qualys, has detailed a new ransomware strain dubbed NotLockBit, which mimics the notorious LockBit ransomware while introducing unique cross-platform capabilities. This malware targets both Windows and macOS systems, marking a significant evolution in ransomware tactics.
NotLockBit is written in the Go programming language, leveraging its cross-platform compatibility and rapid development cycle. “This new strain demonstrates advanced capabilities, including targeted file encryption, data exfiltration, and self-deletion mechanisms,” Kulkarni explained. These features, combined with the mimicry of LockBit’s branding and behavior, make NotLockBit a formidable threat.
How NotLockBit Works
- Initialization and Reconnaissance: Upon execution on macOS, NotLockBit gathers critical system information using the
go-sysinfomodule. It collects details such as hardware specifications, network configurations, and operating system versions, allowing it to tailor its attack. - Encryption Process: NotLockBit employs a dual-layer encryption strategy. A randomly generated AES key encrypts files, while RSA secures the encryption key. Files are renamed with a
.abcdextension, ensuring their recovery is impossible without the private decryption key. The ransomware targets valuable file types, including documents, images, and virtual machine files, while deliberately skipping directories like/proc/and/sys/. - Data Exfiltration: Beyond encrypting files, NotLockBit exfiltrates data to attacker-controlled storage, often using Amazon S3 buckets. This enables a double extortion tactic, threatening to release stolen data if the ransom is unpaid.
- Defacement and Self-Deletion: The ransomware alters the victim’s desktop wallpaper to display a LockBit-inspired ransom note, enhancing its psychological impact. It then deletes shadow copies and self-erases, leaving no trace.
NotLockBit’s targeting of macOS is particularly notable, as it represents one of the first fully functional ransomware strains to impact this platform. By executing commands like osascript to manipulate system settings, the malware demonstrates a deep understanding of macOS internals.
Kulkarni’s analysis highlights the variation in obfuscation across different samples. “Some samples retained visible function names, while others used obfuscated names, and a few were fully stripped,” she noted. This suggests that the threat actors are experimenting with multiple strategies to evade detection.
Kulkarn summarized, “NotLockBit showcases a high degree of sophistication while maintaining compatibility with both operating systems, highlighting its cross-platform capabilities.”
Related Posts:
- SpyMax – A New Android RAT Targeting Telegram Users
- LockBit Imposter: New Ransomware Leverages AWS for Attacks
- Leaked LockBit Tools: Novice Hackers Target Vulnerabilities
- LockBit Ransomware: The Hidden Threat in Resume Word Files
