nray v2.0 alpha3 releases: distributed port scanner in Go
nray
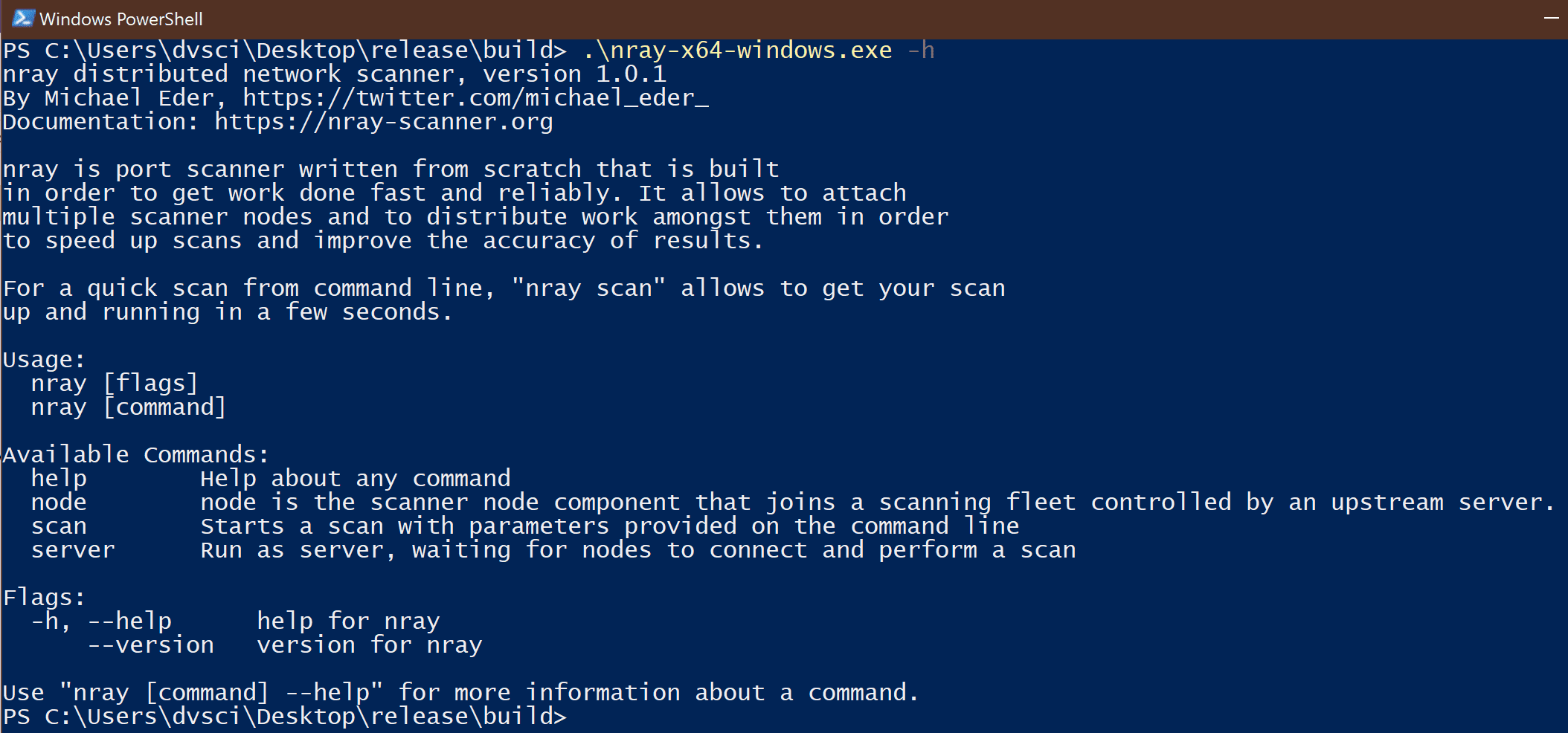
Nray is a free, platform and architecture-independent port and application layer scanner. Apart from regular targets (list of hosts/networks), it supports dynamic target selection, based on sources like certificate transparency logs or LDAP. Furthermore, nray allow running in a distributed manner to speed up scans and to perform scans from different vantage points. Event-based results allow to further process information during the scan, e.g. using tools like jq or full-blown data analysis platforms like elasticsearch or Splunk.
It doesn’t require administrative permissions and runs dependency-less on nearly any architecture and operating system. Nevertheless, its scan speed is superior to Nmap in most cases while delivering nearly the same result quality regarding discovered ports.
Apart from that, nray introduces fresh ideas when it comes to target selection and result processing:
- Target selection:
- IP, domain names and network lists – the usual stuff.
- Nray allows to observe the certificate transparency log and extract domain names from certificates issued nearly in real-time.
- Nray can connect to LDAP (e.g. Active Directory) and perform arbitrary queries, e.g. obtain all registered computer objects and extract their FQDNs.
- DNS zone transfer planned.
- Output
- An event stream encoded as JSON data allows to search and use the results while the scan is still running.
- Native elasticsearch integration: Scan results are stored in your elasticsearch cluster as they arrive. Easily search and analyze the results of your network scans to gain valuable high-level insights.
- Splunk and Metasploit planned.
- Modularity: Want to integrate your CMDB or network inventory to nray? You prefer .csv output because it opens in Excel? Target selection and event processing are built in a modular way, therefore it should not be too hard for you to adapt nray to your requirements.
Nray allows performing application layer scans for selected protocols, e.g. SSH or HTTP, using the ZGrab2 framework. The results are, of course, fully integrated into the event-based JSON result stream.
As mentioned, nray is designed as a distributed network scanner. The server-client model allows to spin up an arbitrary number of nodes that perform a scan orchestrated by a server. This allows scaling scan speed linearly by introducing more nodes or to create network views by scanning from different vantage points.
Changelog v2.0 alpha3
Download & Use
Copyright 2019 by Michael Eder