Win Platform Mail Client 0day Vulnerability | Image: QiAnXin
The QiAnXin Threat Intelligence Center has disclosed the technical details of a sophisticated cyber espionage campaign dubbed “Operation DevilTiger,” orchestrated by the elusive APT-Q-12 group, also known as “Pseudo Hunter.” This advanced persistent threat (APT) group, with deep roots in Northeast Asia, has been actively targeting entities across China, North Korea, Japan, South Korea, and other East Asian countries. The newly released report sheds light on APT-Q-12’s use of zero-day vulnerabilities, advanced techniques, and covert tactics to infiltrate and compromise high-value targets.
QiAnXin traces the origins of APT-Q-12 back to the notorious Darkhotel group, first documented by cybersecurity firms in 2017 under the “Baijiu Action.” Over the years, APT-Q-12, alongside other subsets like APT-Q-11 (ShadowTiger) and APT-Q-14 (ClickOnce), has evolved its methods and objectives, becoming a formidable force in the cyber espionage landscape. These groups have been linked through their overlapping techniques and shared infrastructure, indicating a common lineage from Darkhotel’s earlier operations.
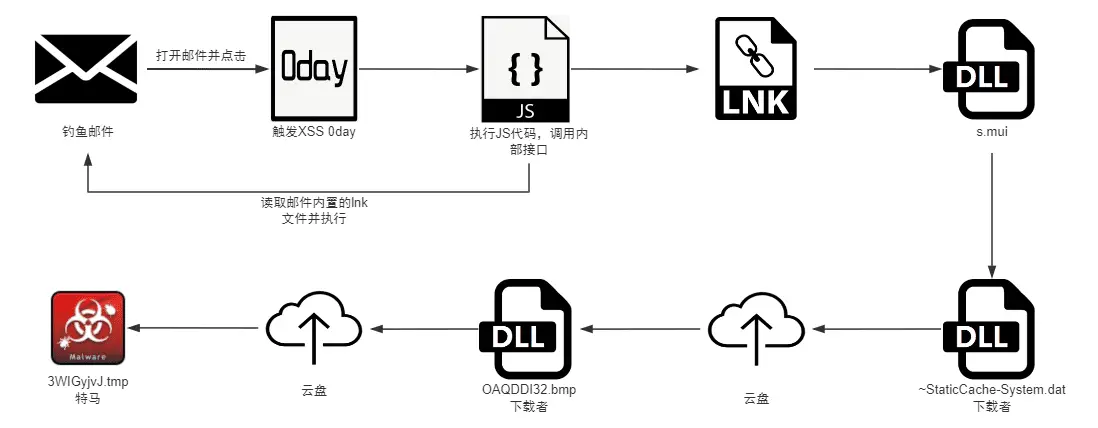
Operation DevilTiger is marked by APT-Q-12’s adept use of zero-day vulnerabilities to penetrate deeply into targeted systems. The group’s modus operandi involves a meticulous information-gathering phase, where they deploy complex probes to detect and exploit vulnerabilities in widely used software and platforms.
One of the key vulnerabilities exploited by Pseudo Hunter involves the use of zero-day flaws in email clients and office software. The group has developed sophisticated methods to determine whether their targets use specific email platforms such as Foxmail, Coremail, or 163, and whether they access these platforms via desktop clients, web versions, or mobile apps. This granular level of detection allows APT-Q-12 to tailor their attacks precisely, ensuring that the zero-day exploit is executed flawlessly.
APT-Q-12’s attacks are further characterized by their use of Command and Control (C2) probes. The group embeds C2 probe links within seemingly legitimate emails and documents, often disguised as advertisements or subscription messages, to gather intelligence on the victim’s software environment. These probes help the attackers identify the victim’s email client and office software, facilitating the delivery of tailored zero-day exploits.
Once inside the target system, APT-Q-12 employs a range of plugins to exfiltrate data. Notably, the group uses a browser steganography plugin to harvest credentials from intranet web platforms and a keylogger plugin to capture sensitive information. The stolen data is then encrypted and stored within the system, waiting for exfiltration through a reverse tunneling tool activated after a period of dormancy.
APT-Q-12’s activities are not limited to espionage; they are part of a broader geopolitical strategy. The group’s focus is on intelligence related to semiconductor competition and political dynamics in Northeast Asia.
The QiAnXin Threat Intelligence Center urges governments and enterprises to bolster their defenses. Deploying advanced endpoint detection and response (EDR) solutions, such as Skyrocket EDR, and enabling cloud-based threat intelligence services are critical steps in mitigating the risks posed by APT-Q-12 and similar threat actors.
Related Posts:
- Mozilla releases emergency update to fix two exploited zero-day vulnerabilities in Firefox
- Hackers use three malware simultaneously in cyber espionage against Ukraine