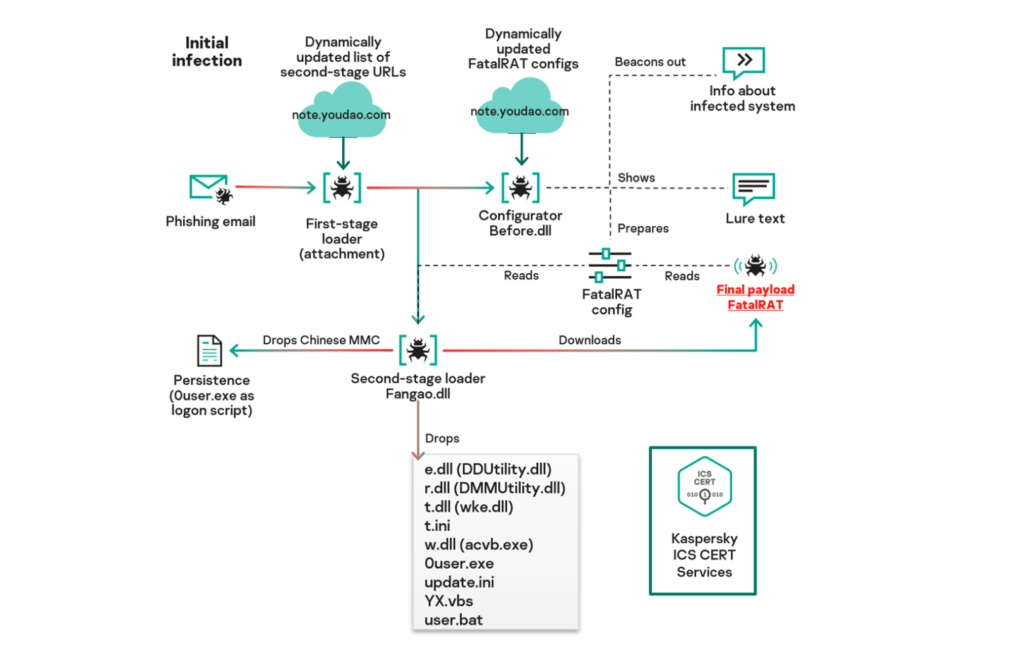
Infection chain | Image: Kaspersky
Kaspersky ICS CERT has uncovered a new malware campaign, dubbed “Operation SalmonSlalom,” specifically targeting industrial organizations across the Asia-Pacific region. The attackers behind this campaign have employed a sophisticated, multi-stage payload delivery framework designed to evade detection and compromise systems within critical infrastructure sectors.
The attackers have leveraged legitimate Chinese cloud services, including the myqcloud CDN and Youdao Cloud Notes, as part of their attack infrastructure. This tactic allows them to blend in with normal network traffic and avoid raising suspicion.
The malware itself is a multi-stage payload, ultimately delivering the FatalRAT remote access trojan (RAT). The infection chain begins with phishing emails, WeChat messages, or Telegram messages containing malicious zip archives disguised as invoices or tax filing applications. These archives contain the first-stage loader, often packed with tools like AsProtect, UPX, or NSPack to hinder analysis.
Once executed, the first-stage loader retrieves a list of URLs from Youdao Cloud Notes, leading to the next stages of the malware. This dynamic approach allows the attackers to change their infrastructure and evade detection.
The malware also employs DLL sideloading and exploits a legitimate software, PureCodec, to achieve persistence and execute its final payload.
Kaspersky’s analysis suggests that the attackers are specifically targeting organizations in industries like manufacturing, construction, IT, telecommunications, healthcare, energy, and logistics. The campaign primarily focuses on countries such as Taiwan, Malaysia, China, Japan, Thailand, South Korea, Singapore, the Philippines, Vietnam, and Hong Kong.
While the exact identity of the attackers remains unknown, Kaspersky notes similarities to previous campaigns using open-source RATs like Ghost RAT, SimayRAT, and Zegost. The use of Chinese-language tools and services, along with specific targeting of Chinese-speaking individuals, suggests a Chinese-speaking threat actor may be involved.
The use of legitimate cloud services, dynamic infrastructure, and multi-stage payloads makes detection and analysis more challenging. Organizations are urged to remain vigilant, educate employees about phishing threats, and implement robust security measures to protect their critical systems.
Related Posts:
- ToddyCat: Unveiling the Stealthy APT Group Targeting Asia-Pacific Governments
- Kaspersky Report: Energy Industry becomes the largest area affected by vulnerabilities in industrial automation systems
- Hacker can use Smartphone Apps to control industrial processes
- Positive Technologies: “73 percent of industrial organizations’ networks are vulnerable to hackers”
