P4wnP1: highly customizable USB attack platform for Raspberry Pi Zero or Raspberry Pi Zero W

P4wnP1 by MaMe82
P4wnP1 is a highly customizable USB attack platform, based on a low cost Raspberry Pi Zero or Raspberry Pi Zero W (required for HID backdoor).
Introduction
Since the initial release in February 2017, P4wnP1 has come along way. Today advanced features are merged back into the master branch, among others:
- the Windows LockPicker (unlock Windows boxes with weak passwords, fully automated by attaching P4wnP1)
- the HID covert channel backdoor (Get remote shell access on air gapped Windows targets tunneled only through HID devices, relayed to a WiFi hotspot with SSH access with a Pi Zero W. The target doesn’t see a network adapter, serial or any other communication device.)
- the HID covert channel frontdoor (Get access to a python shell on P4wnP1 from a restricted Windows host, tunneled through a raw HID device with low footprint. The target doesn’t see a network adapter, serial or any other communication device.)
- refined USB, modular USB setup
External Resources using P4wnP1
- Black Hat Sessions XV, workshop material “Weaponizing the Raspberry Pi Zero” (Workshop material + slides): BHSXV
- ihacklabs[dot]com, tutorial “Red Team Arsenal – Hardware :: P4wnp1 Walkthrough” (Spanish): IHackLabs
P4wnP1 Features
- WiFi Hotspot for SSH access (Pi Zero W only)
- the USB device features work in every possible combination with Windows Plug and Play support (class drivers)
- Support for device types
- HID covert channel communication device (see sections ‘HID covert channel frontdoor’ and ‘HID covert channel backdoor’)
- HID Keyboard
- USB Mass storage (currently only in demo setup with 128 Megabyte drive)
- RNDIS (Windows Networking)
- CDC ECM (MacOS / Linux Networking)
- Raspberry Pi LED state feedback with a simple bash command (
led_blink) - customizeable bash based payload scripts (see
payloads/subfolder for examples example) - includes Responder and a precompiled John the Ripper Jumbo version
- Auto attack: P4wnP1 automatically boots to standard shell if an OTG adapter is attached, the current payload only runs if P4wnP1 is connected as USB device to a target (without USB OTG adapter)
Advanced HID Keyboard Features
- Keyboard payloads could be triggered by targets main keyboard LEDs (NUMLOCK, CAPSLOCK and SCROLLLOCK)
- dynamic payload branching based on LED triggers
- Supports DuckyScript (see hid_keyboard2.txt payload for an advanced example)
- Supports raw ASCII Output via HID Keyboard (could be used to print out character based files via keyboard, like
cat /var/log syslog | outhid) - Multi Keyboard language layout support (no need to worry about target language when using HID commands)
- Output starts when target keyboard driver is loaded (no need for manual delays,
onKeyboardUpcallback could be used in payloads)
Advanced Network Features
- Fake RNDIS network interface speed up to 20GB/s to get the lowest metric and win every fight for the dominating ‘default gateway’ entry in routing tables, while carrying out network attacks (patch could be found here and the README here)
- Automatic link detection and interface switching, if a payload enables both RNDIS and ECM network
- SSH server is running by default, so P4wnP1 could be connected on 172.16.0.1 (as long as the payload enables RNDIS, CDC ECM or both) or on 172.24.0.1 via WiFi
Advanced payload features
- bash payloads based on callbacks (see
template.txtpayload for details)- onNetworkUp (when target host gets network link active)
- onTargetGotIP (if the target received an IP, the IP could be accessed from the payload script)
- onKeyboardUp (when keyboard driver installation on target has finished and keyboard is usable)
- onLogin (when a user logs in to P4wnP1 via SSH)
- configuration can be done globally (
setup.cfg) or overwritten per payload (if the same parameter is defined in the payload script) - settings include:
- USB config (Vendor ID, Product ID, device types to enable …)
- WiFi config (SSID, password …)
- HID keyboard config (target keyboard language etc.)
- Network and DHCP config
- Payload Selection
Windows LockPicker
This payload extends the “Snagging creds from locked machine” approach, presented by Mubix (see credits), to its obvious successor:
P4wnP1 LockPicker cracks grabbed hashes and unlocks the target on success, using its keyboard capabilities. This happens fully automated, without further user interaction.
Video demo
I’m still no video producer, so maybe somebody feels called upon to do a demo. Here’s my (sh**ty) attempt:
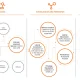
Attack chain (short summary):
- The USB network interface of P4wnP1 is used to bring up a DHCP which provides its configuration to the target client.
- Among other options, a WPAD entry is placed and static routes for the whole IPv4 address space are deployed to the target.
- P4wnP1 redirects traffic dedicated to remote hosts to itself using different techniques.
- Requests for various protocols originating from the target, are fetched by “Responder.py”, which forces authentication and tries to steal the hashes used for authentication.
- If a hash gets grabbed, P4wnP1 LED is blinking three times in sequence, to signal that you could unplug and walk away with the hashes for offline cracking. Or…
- … you leave P4wnP1 plugged and the hashes are handed over to John the Ripper, which tries to bruteforce the captured hash.
- If the ´password of the user who locked the box is weakly choosen, chances are high that John the Ripper is able to crack it, which leads to…
- … P4wnP1 ultimately enters the password, in order to unlock the box and you’re able to access the box (the cracked password is stored in
collectedfolder, along with the hashes).
The payload Win10_LockPicker.txt has to be choosen in setup.cfg to carry out the attack. It is important to modify the payloads “lang” parameter to your target’s language. If you attach a HDMI monitor to P4wnP1, you could watch the status output of the attack (including captured hash and plain creds, if you made it this far).
HID covert channel frontdoor
Video demo
HID frontdoor features
- Plug and Play install of HID device on Windows (tested on Windows 7 and Windows 10)
- Covert channel based on a raw HID device
- Pure in memory PowerShell payload – nothing is written to disk
- Synchronous data transfer with about 32KBytes/s (fast enough for shells and small file transfers)
- Custom protocol stack to handle HID communication and deal with HID data fragmentation
- HID based file transfer from P4wnP1 to target memory
- Stage 0: P4wnP1 sits and waits, till the attacker triggers the payload stage 1 (frequently pressing NUMLOCK)
- Stage 1: payload with “user space driver” for HID covert channel communication protocols is typed out to the target via USB keyboard
- Stage 2: Communications switches to HID channel and gives access to a custom shell on P4wnP1. This could be used to upload and run PowerShell scripts, which are hosted on P4wnP1, directly into memory of the PowerShell process running on the target. This happens without touching disc or using network communications, at any time.