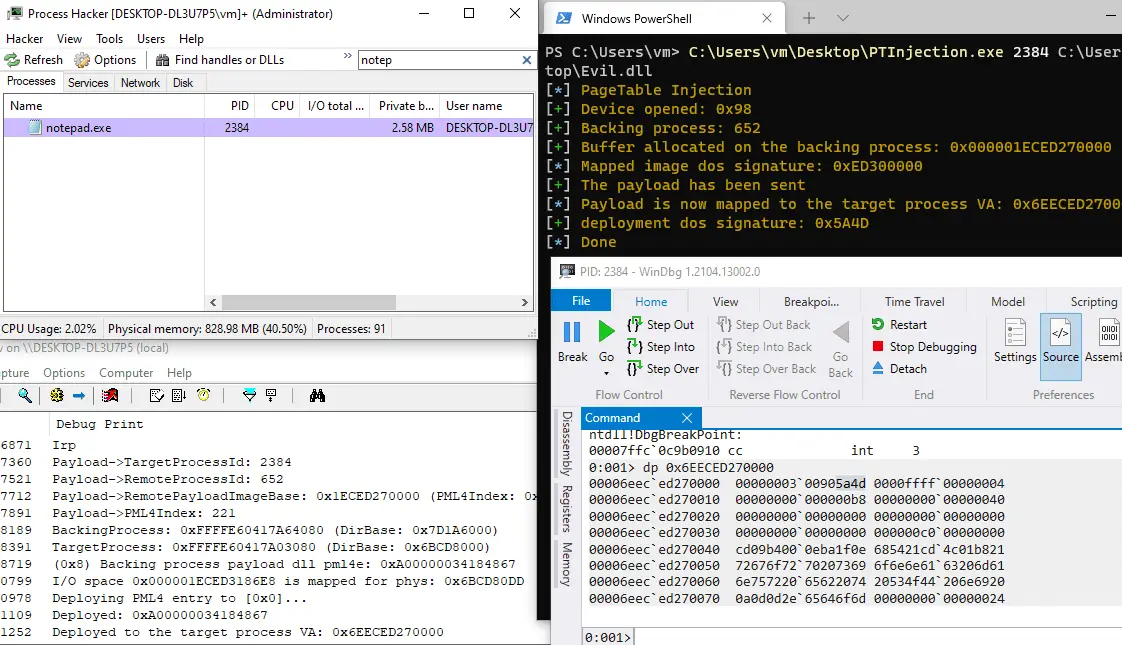
PageTableInjection
Code Injection, Inject malicious payload via pagetables pml4.
Introduction
This is just a proof-of-concept of the page table injection technique to inject malicious code into the arbitrary user processes.
On Windows(and some modern OSes), every process has a its PML4 a.k.a Directory Table Base. Thus the process A cannot access process B without APIs. but how about if we can inject arbitrary PML4 entry? of course, the PML4 entry will point to the corresponding physical address of entries, PDP, PD, and PT as exactly the same as the backing process.
In order to inject malicious PML4 entry to the target process, we need to have an actual resident page (physical memory) that backing the malicious PML4 entry. Thus literally the resident page must be a resident, otherwise, the system will crash or would become unstable, because, during the MMU translating to the physical address, there is nothing that MMU expects, as well as there is nothing the windows memory manager has nothing expects.
Let’s look at the both backing process and target process buffers. In this case, the buffers are:
- Backing Process VA: 0x1A45F810000
- Deployment Process Injected VA: 0x6EA45F810000
Before step to the next, some of you may think that the 2nd address(0x6EA45F810000) looks weird like usually, we allocated buffer via malloc or VirtualAlloc, the virtual address should look like 0x17C7CAC0000 0x23BE9D80000 0x19FE76F0000 or some sort of these. it’s because the malicious PML4 entry is not involved to the memory manager of windows, and is not managed as well. of course every virtual address on Windows 64-bit process could possibly have any value within a range of user memory range.
So if we look into both addresses…
Both addresses are corresponding to the exact same page table entries, PDP, PD, PT, and a physical address. Therefore if we modified the backing process’s buffer, the change also on the target process. This is very similar to the shared memory on Windows, but the difference is that the memory region on the target process will never be shown in any VAD entries of its process. but in another hand, if the backing process’s buffer is freed, it means also the target process but without cleaning the target process’s page table entries, which means that the memory manager will cause a bugcheck MEMORY_MANAGEMENT, or will trigger a worse triple fault on the CPU.
Download
Copyright (c) 2021 Kento Oki