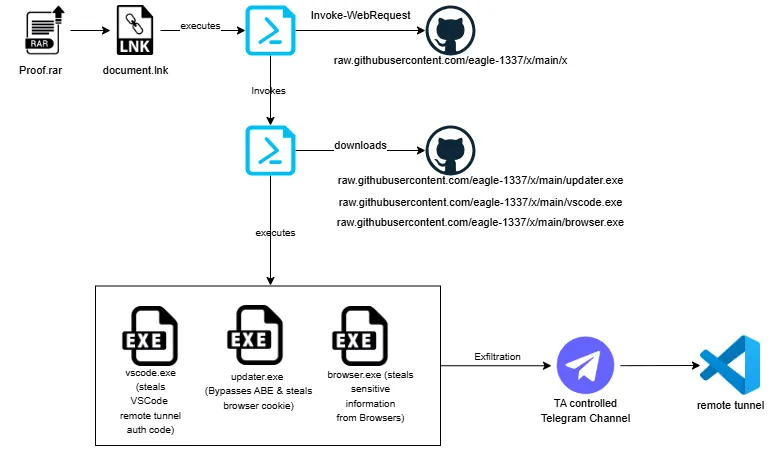
Infection chain | Image: Cyble
A newly identified stealthy malware campaign, dubbed Phantom Goblin, has been uncovered by Cyble Research and Intelligence Labs (CRIL). This sophisticated attack uses social engineering tactics to trick victims into executing a malicious LNK file, initiating a multi-stage attack aimed at stealing browser credentials and establishing unauthorized remote access via Visual Studio Code (VSCode) tunnels.
The attack begins with a RAR attachment—likely delivered via phishing emails—that contains a malicious shortcut file disguised as a legitimate document. CRIL researchers highlight that “the RAR archive file named ‘Proofs.rar’ contains an LNK file named ‘document.lnk’, which is designed to resemble a PDF document.” This deceptive tactic lures unsuspecting users into executing the malware.
Once executed, the LNK file triggers a PowerShell command, retrieving additional payloads from a GitHub repository. The malware ensures persistence by modifying Windows registry keys, enabling it to execute on system startup.
One of Phantom Goblin’s primary objectives is stealing sensitive browser data. The malware executes an Updater.exe file that systematically:
- Identifies and terminates browser processes using taskkill.exe to unlock stored credentials.
- Reopens browsers in headless mode with remote debugging enabled—a technique that bypasses Chrome’s App Bound Encryption (ABE).
- Extracts login credentials, session cookies, browsing history, and autofill data.
- Archives stolen data into ZIP files before sending them to the attacker’s Telegram bot for covert exfiltration.
Phantom Goblin deploys Vscode.exe, a component designed to establish an unauthorized VSCode tunnel. This allows attackers to maintain persistent, remote access without triggering traditional security alerts.
CRIL’s report notes: “The malware now initiates another PowerShell script to interact with the extracted VSCode binaries… The script navigates to the extracted VSCode directory and logs out any active tunnel sessions.” Once active, the malware steals VSCode connection details and sends them to a Telegram bot, granting attackers remote control over compromised systems.
The stealthy nature of Phantom-Goblin makes it particularly dangerous. By leveraging trusted tools like GitHub, PowerShell, and VSCode, the malware blends into normal system operations, avoiding detection by security solutions.
Phantom Goblin is an example of the evolving tactics cybercriminals use to infiltrate systems and steal sensitive data. As CRIL researchers warn, “This malware attack highlights the increasing sophistication of cyber threats that leverage social engineering and trusted tools for stealthy execution.”
Related Posts:
- FBI arrests CEO Phantom who sold customized BlackBerry to Sinaloa drug trafficking group
- Operation Phantom Circuit: North Korea’s Global Data Exfiltration Campaign Unveiled
- Beware of Malicious Extensions: Researcher Exposes VSCode Marketplace Threats