Pinjectra
Pinjectra is a C/C++ library that implements Process Injection techniques (with focus on Windows 10 64-bit) in a “mix and match” style. Here’s an example:
It’s also currently the only implementation of the “Stack Bomber” technique. A new process injection technique that is working on Windows 10 64-bit with both CFG and CIG enabled.
Pinjectra, and “Stack Bomber” technique released as part of the Process Injection Techniques – Gotta Catch Them All talks given at BlackHat USA 2019 conference and DEF CON 27 by Itzik Kotler and Amit Klein from SafeBreach Labs.
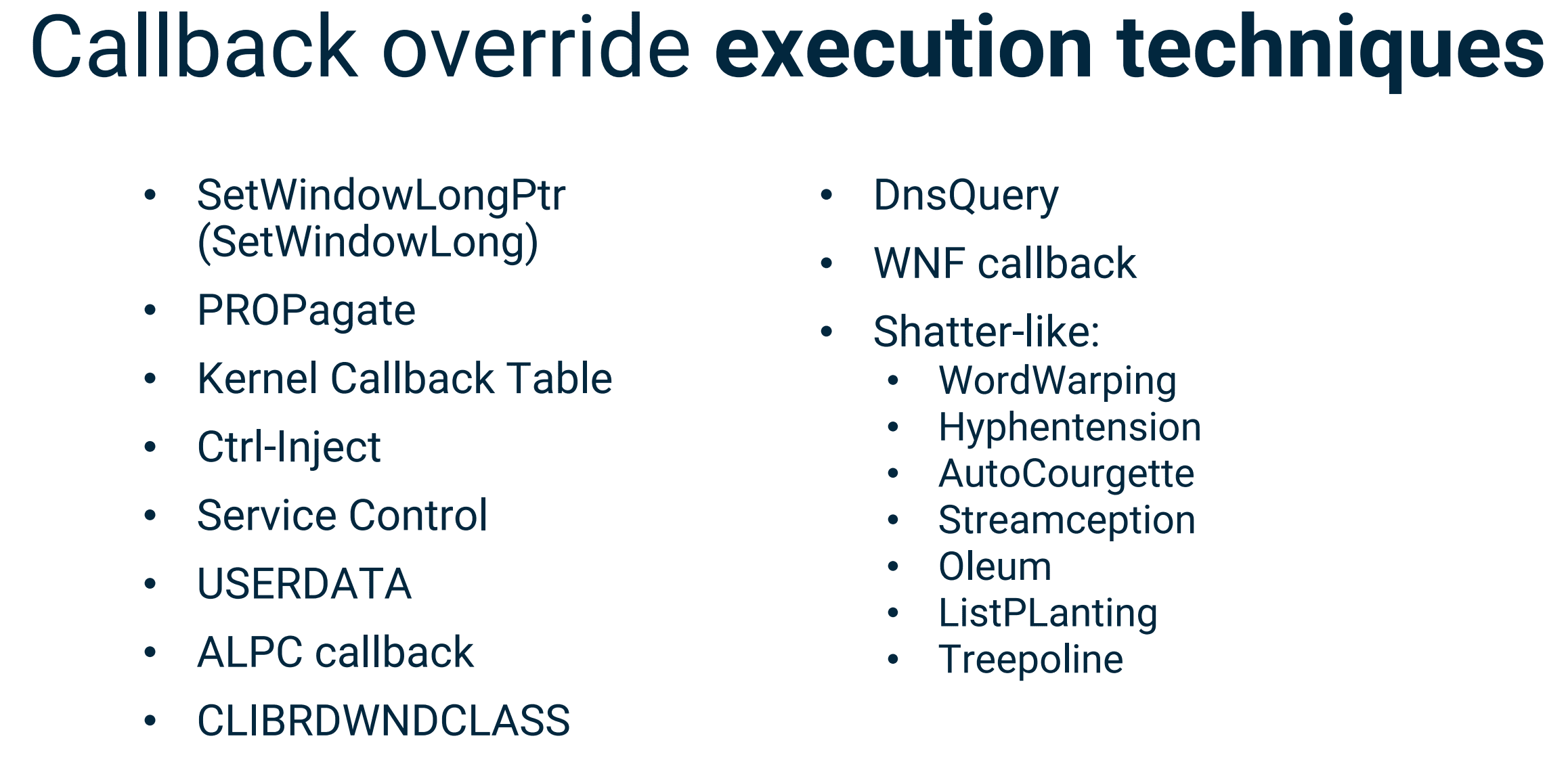
Why this research?
- No comprehensive collection/catalog of process injection techniques
- No separation of true injections from process hollowing/spawning
- No categorization (allocation vs. memory write vs. execution), analysis, comparison
- Update for Windows 10 (latest versions), x64
True process injection
- True process injection – from live userspace process (malware) to live userspace process (target, benign)
- In contrast to (out of scope):
- Process spawning and hollowing – spawning the “target” process and injecting into it (especially before execution)
- Pre-execution – e.g. DLL hijacking, AppCert, AppInit, LSP providers, Image File Execution Options, etc.
Windows 10, x64
- Windows 10
- CFG (Control Flow Guard) – prevent indirect calls to non-approved
addresses - CIG (Code Integrity Guard) – only allow modules signed by Microsoft/Microsoft Store/WHQL to be loaded into the process memory
- x64 (vs. x86)
- Calling convention – first 4 arguments in (volatile) registers: RCX, RDX, R8,
R9. Invoking functions (from ROP) necessitates control over some/all these registers. - No POPA – writing ROP is more difficult (bootstrapping registers)
- Calling convention – first 4 arguments in (volatile) registers: RCX, RDX, R8,
Copyright (c) 2019, SafeBreach Labs
All rights reserved.