PKINIT tools
This repository contains some utilities for playing with PKINIT and certificates. The tools are built on minikerberos and impacket. Accompanying blog post with more context.
Tools
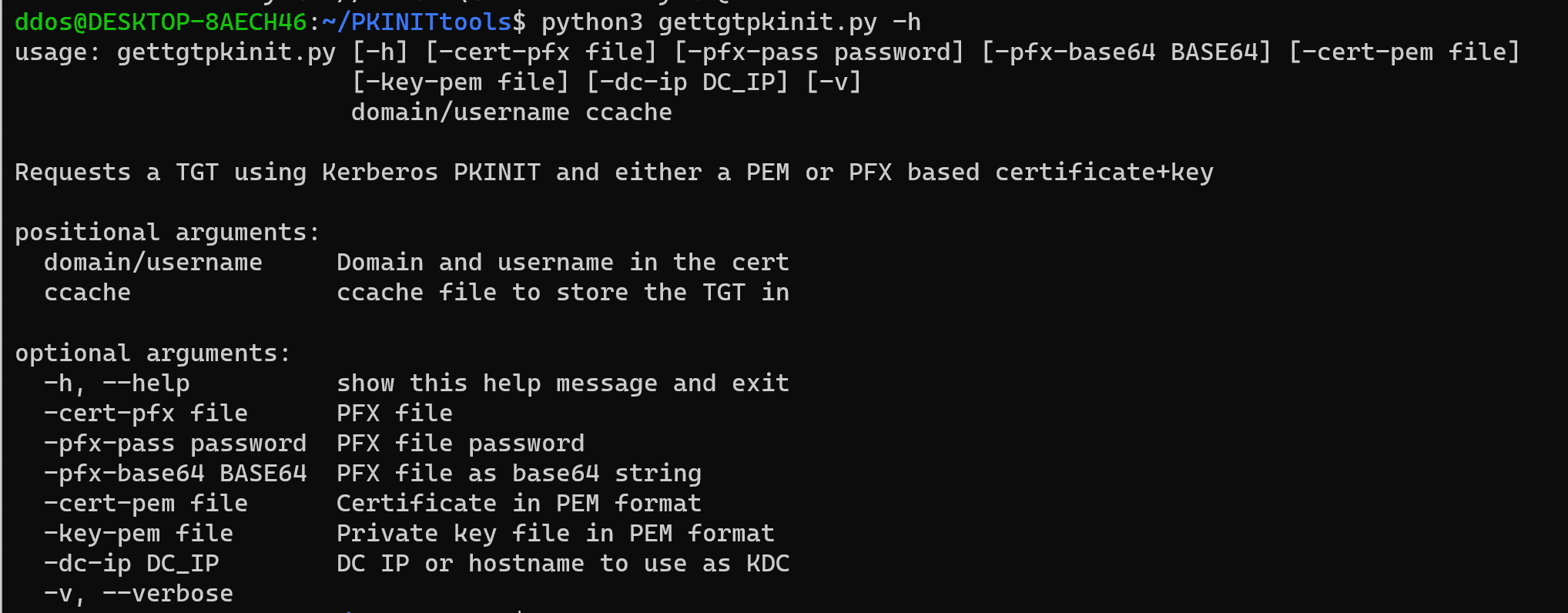
gettgtpkinit.py
Request a TGT using a PFX file, either as a file or as base64 encoded blob, or PEM files for cert+key. This uses Kerberos PKINIT and will output a TGT into the specified ccache. It will also print the AS-REP encryption key which you may need for the getnthash.py tool.
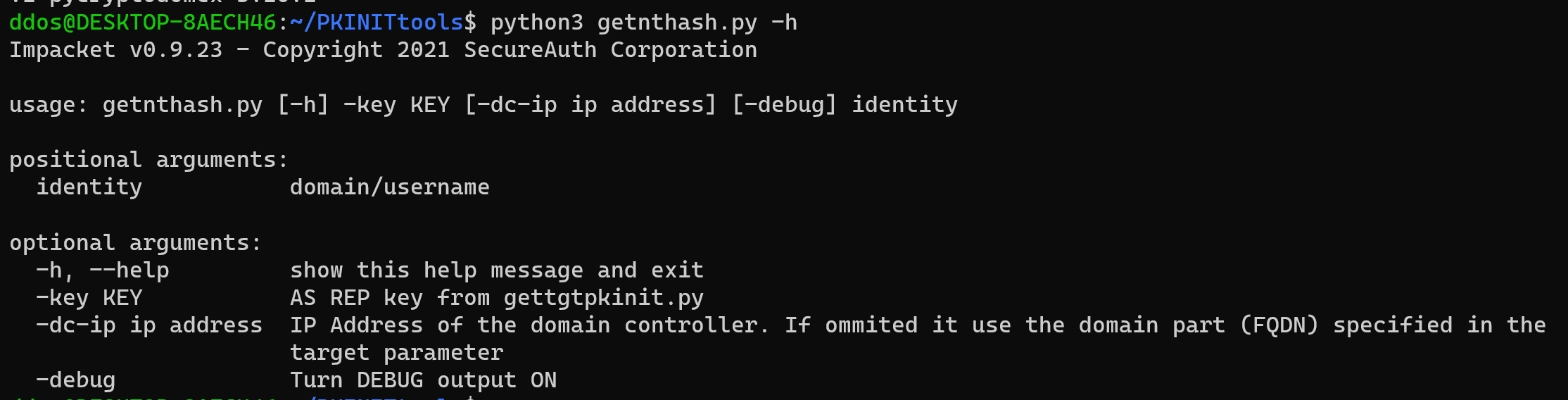
getnthash.py
Use Kerberos U2U to submit a TGS request for yourself. This will include the PAC which in turn contains the NT hash that you can decrypt with the AS-REP key that was used for your specific TGT. It’s magic really. This tool requires a TGT resulting from PKINIT to be in your KRB5CCNAME env variable.
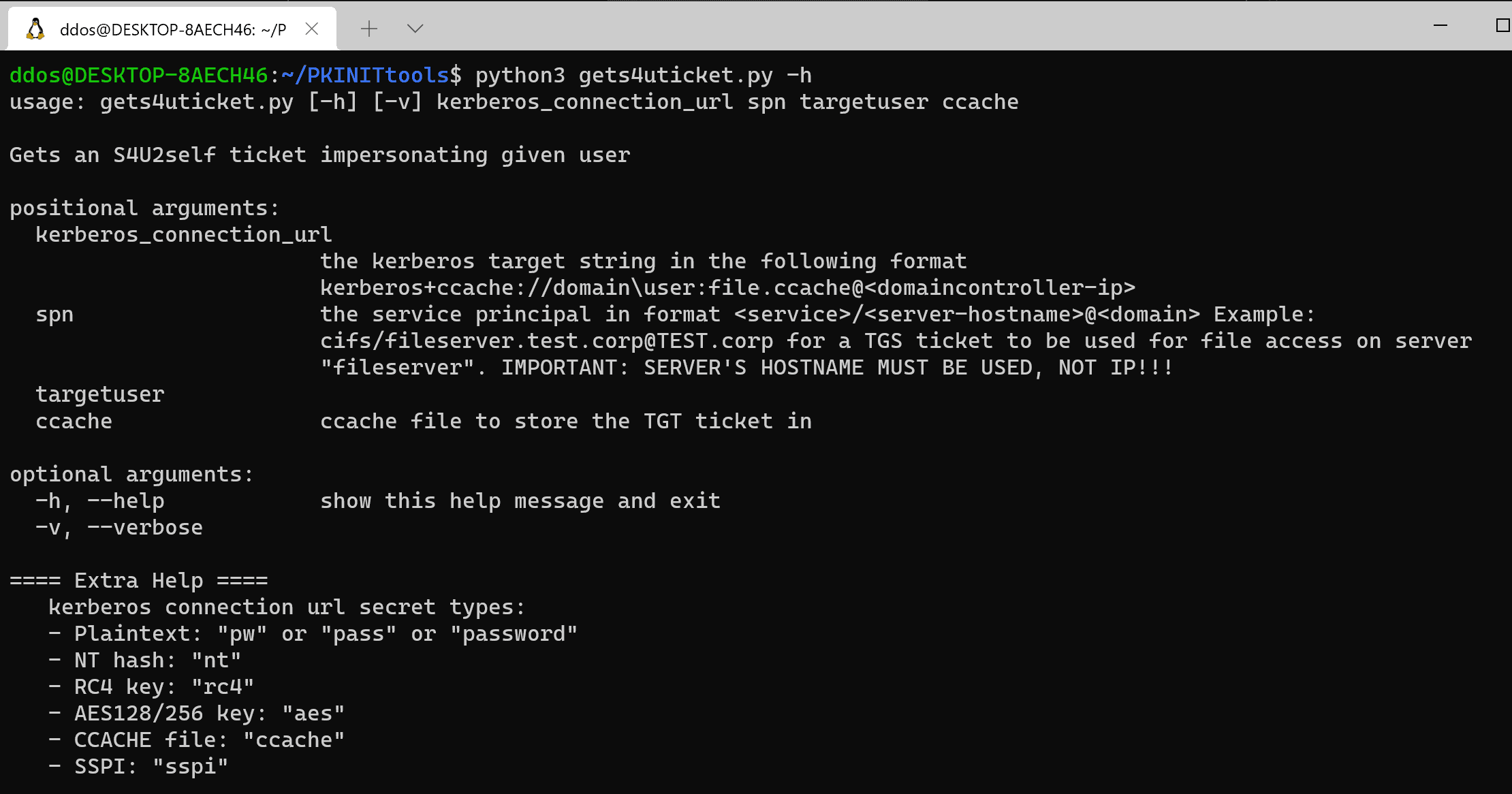
gets4uticket.py
Uses Kerberos S4U2Self to request a service ticket that is valid on the host for which you’ve obtained a certificate. This ticket can then be used to interact with the original host. This only requires a TGT for the machine account of this host. This TGT should be in a ccache file that you specify in the kerberos_connection_url. The only accepted kerberos_connection_url for this example is one containing a ccache file, so for example kerberos+ccache://domain.local\\victimhostname\$:victimhostname.ccache@kdchostname.domain.local. The SPN should be a service name on the host you are impersonating, you can’t use this for delegation attacks (since it does not implement S4U2Proxy, there are plenty of tools already for that).
Installation
git clone https://github.com/dirkjanm/PKINITtools
pip3 install impacket minikerberos
Copyright (c) 2021 Dirk-jan Mollema (@_dirkjan)