A security researcher has published a proof-of-concept (PoC) exploit code targeting a recent high-severity vulnerability (CVE-2024-30088) in Microsoft Windows. This critical flaw holds a risk severity score of 7.0 and impacts systems across the globe, potentially allowing attackers to execute arbitrary code with SYSTEM privileges.
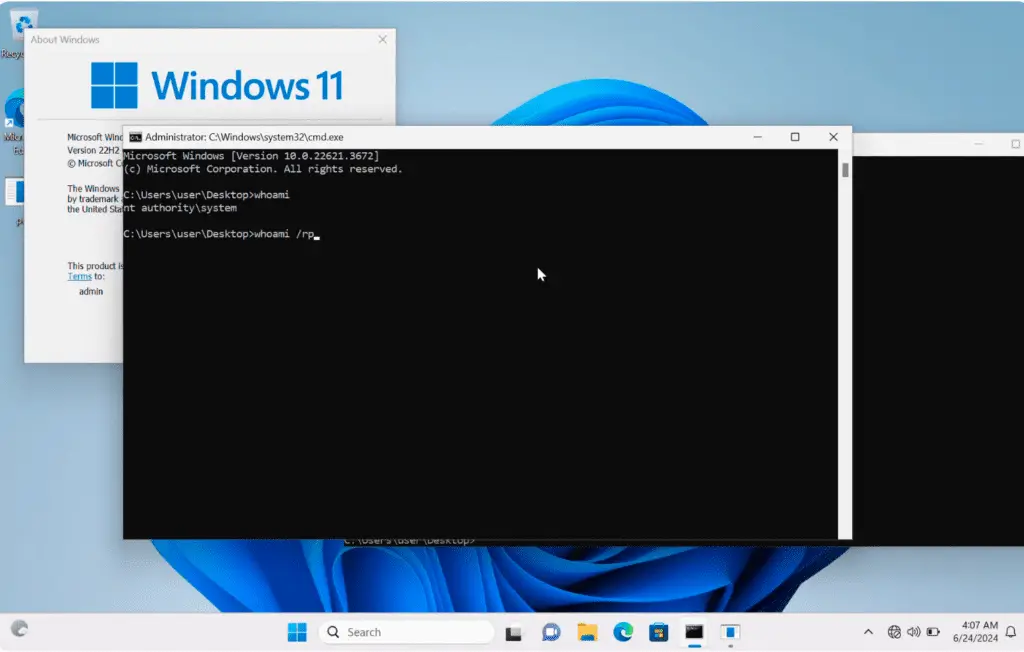
The vulnerability resides within the function NtQueryInformationToken, particularly in the handling of the AuthzBasepCopyoutInternalSecurityAttributes function. The flaw stems from the kernel’s improper management of locking mechanisms when operating on an object, a slip-up that could lead to unintended privilege escalation for malicious entities.
Detailed by Vietnamese security researcher Bùi Quang Hiếu, known in the cyber circles as @tykawaii98, the vulnerability allows for an attack vector where the SecurityAttributesList from the kernel could be manipulated directly to a user-supplied pointer. This precarious action leads to multiple Time-of-Check to Time-of-Use (TOCTOU) vulnerabilities, whereby a malicious thread could alter the buffer pointer of an attribute name before the RtlCopyUnicodeString function is called. Such manipulation enables the attacker to write to an arbitrary address with a controlled value and size.
Prompted by the discovery, which was initially credited to Emma Kirkpatrick (@carrot_c4k3) in collaboration with the Trend Micro Zero Day Initiative, Microsoft addressed the issue in its June 2024 round of security updates.
The revelation was further elucidated by researcher Hiếu, who not only published a comprehensive writeup but also provided a proof-of-concept (PoC) exploit for CVE-2024-30088 on GitHub. His demonstration video, showcasing the exploit in action, plays a crucial role in understanding the mechanics of the attack and the potential ramifications if left unpatched.
The exposure of such a vulnerability is particularly alarming due to the elevated privileges attackers can gain – effectively seizing complete control over the affected system. This privilege escalation can facilitate further malicious activities, including data theft, system sabotage, and the deployment of additional malware.
Those operating on Windows are urged to apply the latest security patches provided by Microsoft, thereby mitigating the risk posed by this and other disclosed vulnerabilities.