A recently discovered flaw, CVE-2023-0386, with a CVSS score of 7.8, has been identified in the Linux kernel’s OverlayFS subsystem. The vulnerability enables unauthorized access to the execution of setuid files with capabilities, and results from the improper handling of user copies of a capable file from a nosuid mount to another mount. This uid mapping bug allows a local user to escalate their privileges on the system, posing a significant security threat.
The Linux kernel privilege escalation bug, CVE-2023-0386, enables an attacker with low-privileged user access on a Linux machine with an overlay mount containing a file capability in one of its layers to escalate their privileges up to root. The attacker can achieve this by copying a capable file from a nosuid mount into another mount. This vulnerability is similar to CVE-2021-3847 but requires fewer permissions to run, making it a higher-priority concern.

The steps to reproduce:
1. Mount a FUSE filesystem that exposes a root-owned setuid/setgid binary that is world writable.
2. Unshare user/mount namespaces.
3. Mount an overlay with the FUSE filesystem as the lower directory and a user-writable upper directory. Ensure that the upper directory is on a filesystem not mounted with `nosuid`.
4. Touch the file at the merged path to update its mtime, triggering a copy-up of the file.
5. The kernel does not clear the setuid/gid bits, so the upper directory will contain a copy of the binary with the setuid bits.
6. Run the binary from the upper directory, and it will execute as root.
Notably, CVE-2023-0386 differs from CVE-2021-3847 in that it exploits setgid/setuid bits, which are not user-namespace-specific, whereas CVE-2021-3847 involves file capabilities (xattrs) that have special rules within user namespaces. Moreover, CVE-2021-3847 pertains to USB mounts that require physical access and are often disabled in production environments, while FUSE does not necessitate physical access and is installed in many production environments.
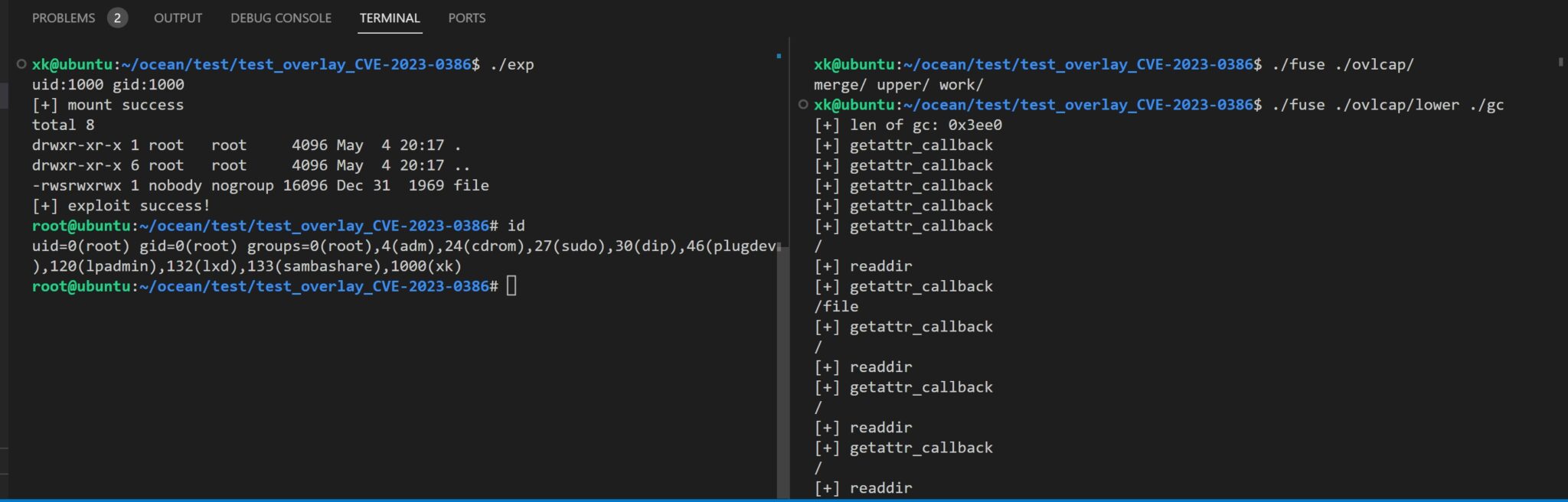
Researcher Xkaneiki developed a proof-of-concept (PoC) exploit for this vulnerability, demonstrating the potential risks posed by CVE-2023-0386. The PoC exploit was tested on Ubuntu 22.04 and successfully gained root privileges. The existence of the PoC exploit code for CVE-2023-0386 highlights the urgency for developers and system administrators to address this Linux kernel privilege escalation bug and prioritize security updates to mitigate potential attacks.