PoC Released for Linux Kernel Privilege Escalation (CVE-2023-32233) Vulnerability

Recently, a new security vulnerability has been discovered in the Linux kernel that could allow an attacker to gain elevated privileges on a system. This vulnerability tracked as CVE-2023-32233 with a CVSS score of 7.8, is a serious concern for all Linux users.

The Root Cause: Netfilter nf_tables
The vulnerability resides within the Netfilter nf_tables system, a component of the Linux kernel that manages network packet filtering and network address translation. The nf_tables system allows its configuration to be updated as an atomic operation. When this feature is used, user-mode clients send batch requests containing a list of basic operations. These operations are then processed as a single transaction.
The kernel checks the configuration state updates to ensure that each subsequent operation is valid. However, the implemented check in the nf_tables component has been found to be insufficient. In essence, it fails to account for the state updates from all the previous operations within the batch. This flaw could be exploited by an authenticated local attacker to escalate their privileges to root.
The exploitation requires the CAP_NET_ADMIN capability over the network namespace. It’s essential to note that this vulnerability could potentially allow the user to gain root access, the highest level of system control.
The Proof-of-Concept (PoC) Exploit Code for CVE-2023-32233
Security researchers Patryk Sondej and Piotr Krysiuk discovered this vulnerability and reported it to the Linux kernel team. They not only found the CVE-2023-32233 flaw but also developed a Proof-of-Concept (PoC) that allows unprivileged local users to start a root shell on impacted systems.
However, exploiting this vulnerability isn’t straightforward. It requires winning a race with a background worker thread from the Linux kernel. The PoC includes a built-in profile to maximize the chance of winning this race on a broad range of Intel microprocessors, from mobile Sandy Bridge to desktop Comet Lake.
Yet, microprocessors are not created equal. Some, like Alder Lake, may require additional tuning due to increased task-switching latency under certain setups. In these cases, appending “400 race_lead_sleep” to the “profile” may be necessary.
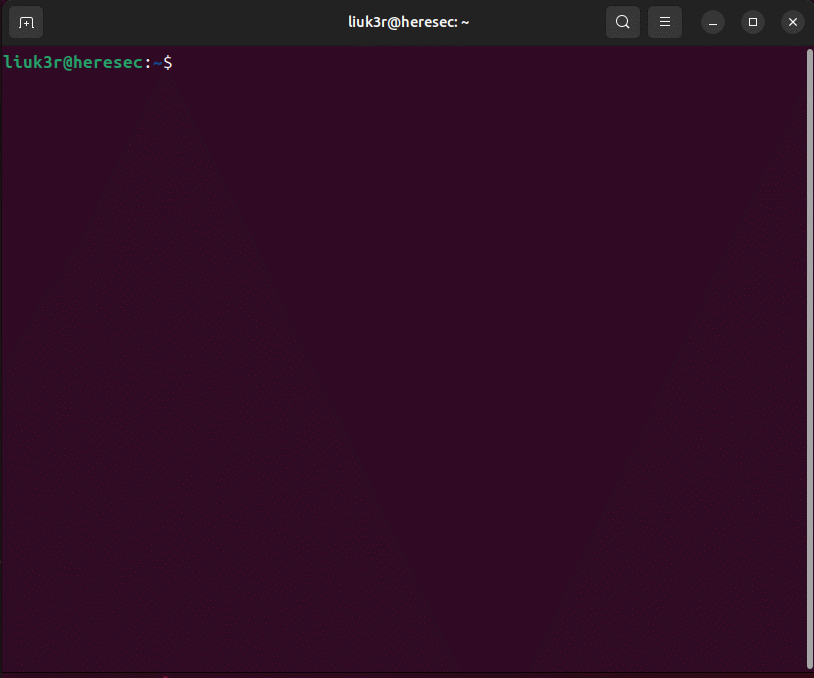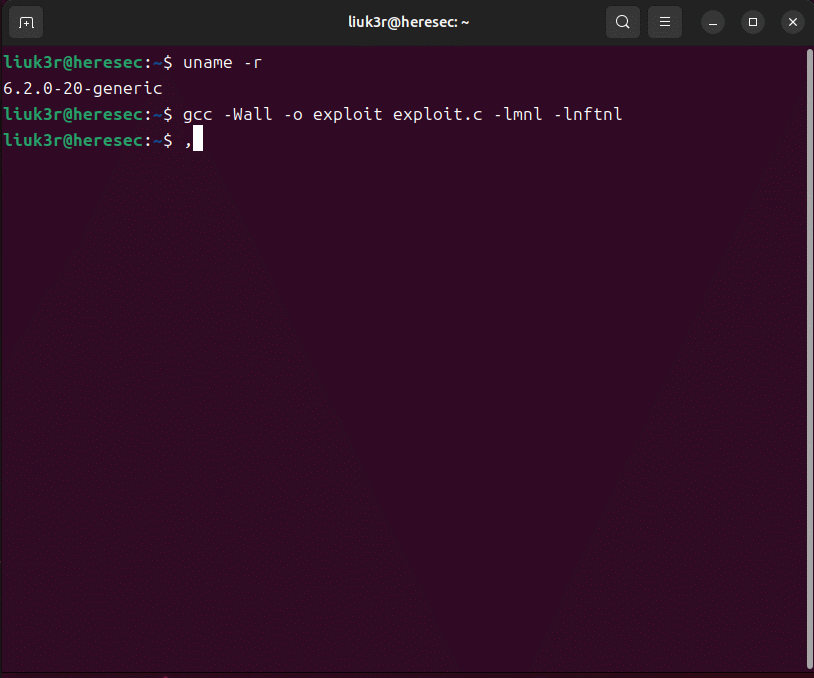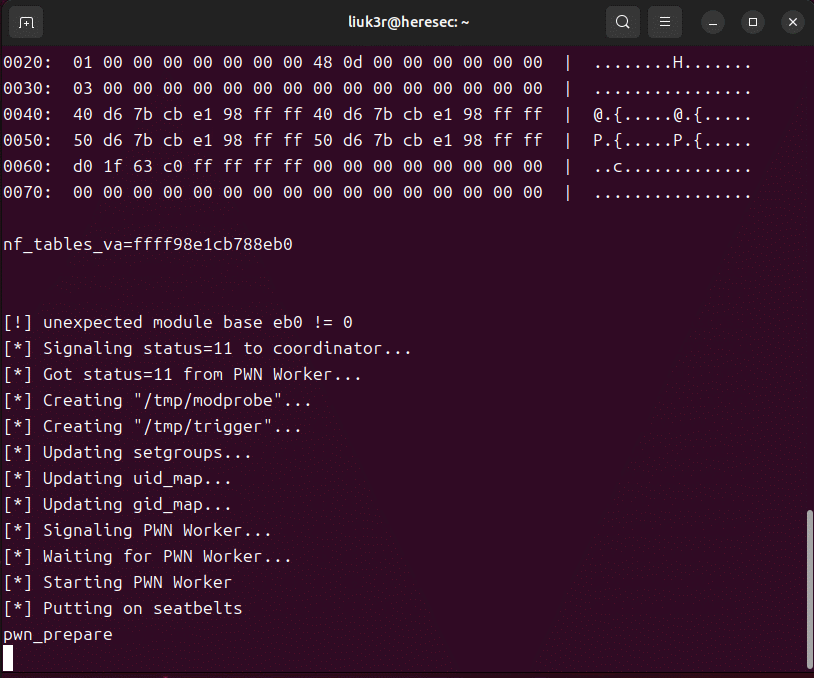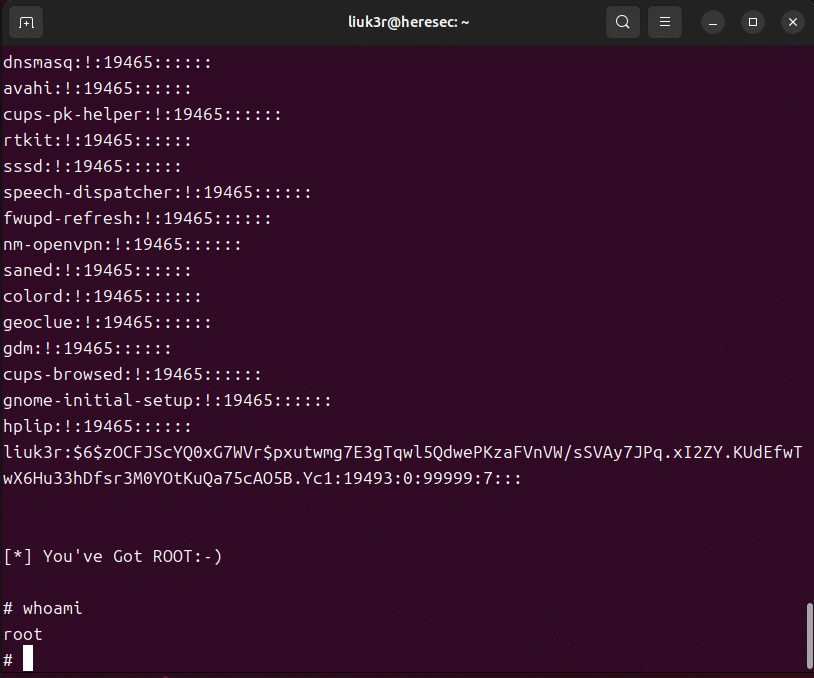
Image: Liuk3r
Impact and Mitigation
The PoC has been tested against Ubuntu 23.04 Desktop for amd64, but the vulnerability isn’t limited to Ubuntu. The affected code originates from the upstream Linux kernel, and the researchers confirmed that exploitation is possible against other popular distributions.
But, beware! Running the PoC on a vulnerable system may leave it in an unstable state due to kernel memory corruption. Therefore, it’s of utmost importance to apply any security patches provided by your Linux distribution as soon as possible to mitigate this vulnerability. Also, consider limiting the CAP_NET_ADMIN capability to only the most trusted users.





