Image: zerodayinitiative
Two vulnerabilities in Microsoft SharePoint Server have recently come under the spotlight, thanks to the detailed work of STAR Labs researcher Nguyễn Tiến Giang (Jang).
In March, at the Pwn2Own contest in Vancouver, a dramatic demonstration took place. Jang unveiled an exploit chain linking two distinct vulnerabilities in Microsoft SharePoint Server: CVE-2023-29357 and CVE-2023-24955. This chain was not just a theoretical exercise; it enabled remote code execution (RCE) against the server, a feat that captured the attention of cybersecurity enthusiasts and professionals alike.

Fast forward to September 25 and 26, Jang published a blog post detailing this exploit chain, followed by the release of a proof-of-concept (PoC) on GitHub for CVE-2023-29357. The authors of the PoC took an ethical stance, ensuring that RCE wasn’t achievable with the current PoC. However, the cybersecurity world is well aware that malicious actors are often quick to adapt public PoC codes for nefarious purposes. This development underscored the urgency of patching these vulnerabilities.
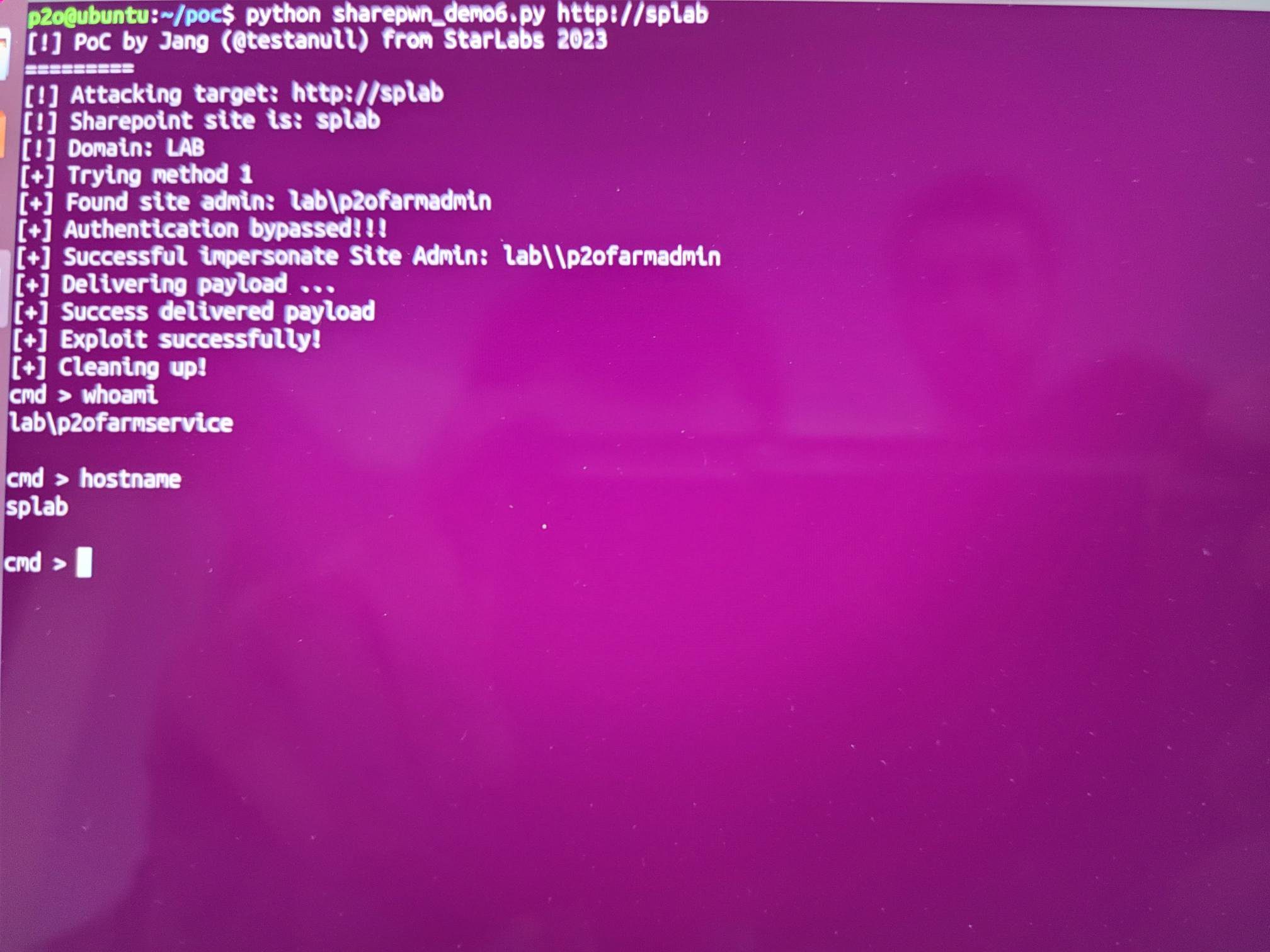
Yesterday, Jang published more details about the authentication bypass and code injection chain in SharePoint, which was used in Pwn2Own Vancouver 2023. Also, a proof-of-concept (PoC) exploit for SharePoint Pre-Auth Code Injection RCE chain has been released for two vulnerabilities (CVE-2023-29357 & CVE-2023-24955) in Microsoft SharePoint Server that can be exploited to achieve unauthenticated remote code execution.
MS finally replys to our email and allow us to public more details about the Auth bypass and Code Injection chain in SharePoint, which was used in Pwn2Own Vancouver 2023.
Here is the (not-so) fully working PoC for that:https://t.co/kj6decsL4S
Have a nice weekend! 😉— Janggggg (@testanull) December 15, 2023
CVE-2023-29357 emerged as an elevation of privilege vulnerability in Microsoft SharePoint Server with a staggering CVSSv3 score of 9.8. It allowed remote, unauthenticated attackers to gain the privileges of an authenticated user by sending a spoofed JSON Web Token (JWT) authentication token. No user interaction was required, making it a particularly insidious vulnerability.
On the other hand, CVE-2023-24955, with a CVSSv3 score of 7.2, was a remote code execution vulnerability. It required an authenticated Site Owner for exploitation, but the impact was significant, enabling code execution on the affected SharePoint Server.
Jang’s blog post revealed that nearly a year of research went into developing this exploit chain. By ingeniously combining an authentication bypass (CVE-2023-29357) with a code injection vulnerability (CVE-2023-24955), Jang achieved unauthenticated RCE. This accomplishment wasn’t just theoretical; a video demonstration available on YouTube showed the exploit chain in action.
Microsoft responded to these discoveries with patches released as part of their May and June 2023 Patch Tuesday releases. While the current PoC does not enable RCE directly, the possibility of threat actors modifying the exploit for malicious use remains a real and present danger. This scenario underscores the critical importance of applying these patches as a proactive defense against potential cyber-attacks.