project-memoria-detector
The project-memoria-detector tool aims to determine whether a target network device runs a vulnerable TCP/IP stack.
Currently, the tool supports fingerprints for four embedded TCP/IP stacks (and their variations) that were found vulnerable during the AMNESIA:33 research:
- uIP, Contiki or Contiki-NG
- picoTCP or picoTCP-NG
- Nut/Net
- FNET
How does it work?
The script identifies the use of four TCP/IP stacks (uIP/Contiki, picoTCP, FNET, and Nut/Net) on a target device via three active fingerprinting methods:
- ICMP probing: the script performs a malformed ICMP echo request and checks for characteristics of the reply, including changes in the Time-to-live (TTL) value and specific payload content, which varies per stack.
- TCP options signatures: the script sends a TCP SYN packet and monitors the TCP SYN-ACK response for the format of the TCP options field. Each stack replies with different values for the options, such as a Maximum Segment Size (MSS) and window scale.
- TCP Urgent flag handling: the script sends a TCP packet with the Urgent flag set and monitors the response. Each stack replies with a different set of TCP flags and a different TCP Window size value.
Although the script has been tested with the four stacks affected by AMNESIA:33 in a lab environment, we cannot guarantee its use to be safe against every possible device. Malformed ICMP packets, for instance, could crash a device that is running a different stack. Therefore, we do not recommend its use directly in live environments with mission-critical devices (such as hospitals with patient-connected devices or safety-critical industrial control systems). An ideal approach is to test devices in a lab setting or during a maintenance window.
Download
git clone https://github.com/Forescout/project-memoria-detector.git
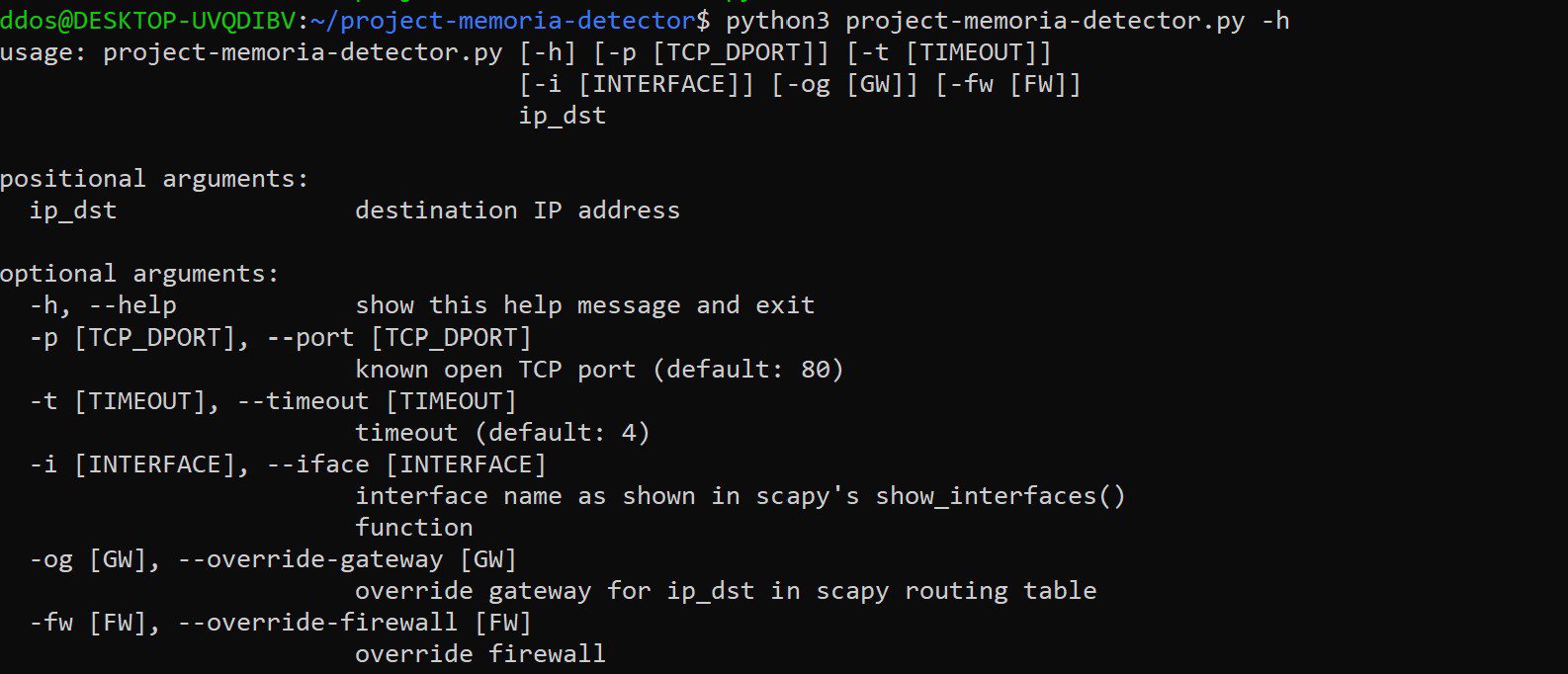
Use
Copyright (C) 2020 Forescout Technologies, Inc.
Source: https://github.com/Forescout/