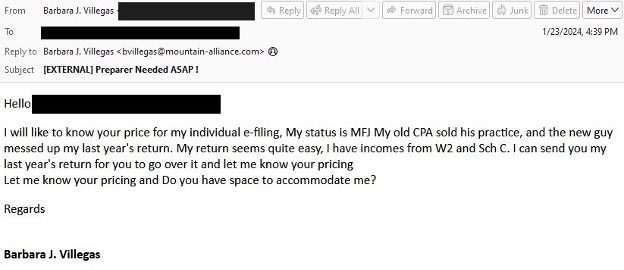
Tax-themed lure used by TA576
As the tax season rolls in, so does the threat of cybercrime, and leading the charge in 2024 is the infamous TA576 threat actor. Researchers at Proofpoint have unveiled the resurgence of this cybercriminal group, notorious for its tax-themed lures targeting the accounting and finance sectors. Active predominantly during the U.S. tax season, TA576 adopts a crafty modus operandi to ensnare organizations in North America through low-volume email campaigns.
Their strategy is straightforward yet devious: send emails under the guise of seeking tax preparation assistance, and when the target engages, hit them with a malicious link. This link, cleverly masked as a benign request, leads to a remote HTML page, baiting users into a trap that deploys remote access trojans (RATs).

In January 2024, TA576 refined its tactics, using compromised accounts to send emails that appeared innocuous but featured a reply-to address with a domain recently registered by the threat actors. The intriguing part of their campaign is the use of a zipped shortcut file, which when executed, unleashes a chain of malicious activities, exploiting encoded PowerShell, LOLBAS techniques, and the Mshta tool to run an HTML application payload. The payload then decrypts and executes a command that downloads and runs an executable, deploying the Parallax RAT using the Heaven’s Gate evasion technique.
TA576’s 2024 campaigns mark a significant evolution in their modus operandi, distinct from their previous approaches involving JavaScript payloads or macro-enabled Word documents. This adaptability not only highlights TA576’s cunning but also underscores the growing trend of creativity and experimentation in cybercriminal tactics.