prowler: Distributed Network Vulnerability Scanner
Prowler
Prowler is a Network Vulnerability Scanner implemented on a Raspberry Pi Cluster, first developed during Singapore Infosec Community Hackathon – HackSmith v1.0.

Capabilities
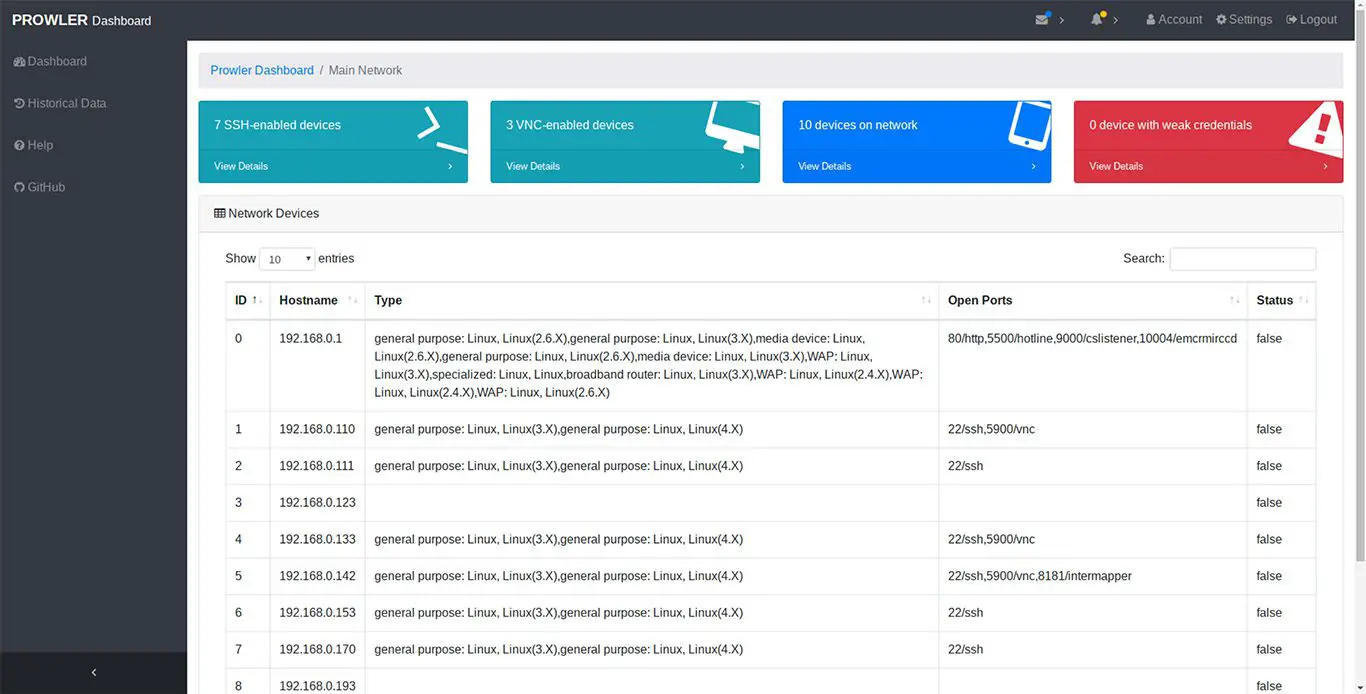
- Scan a network (a particular subnet or a list of IP addresses) for all IP addresses associated with active network devices
- Determine the type of devices using fingerprinting
- Determine if there are any open ports on the device
- Associate the ports with common services
- Test devices against a dictionary of factory default and common credentials
- Notify users of security vulnerabilities through a dashboard. Dashboard tour
Hardware
- Raspberry Pi Cluster HAT (with 4 * Pi Zero W)
- Raspberry Pi 3
- Networking device
Software Stack
- Raspbian Stretch (Controller Pi)
- Raspbian Stretch Lite (Worker Pi Zero)
- Note: For ease of setup, use the images provided by Cluster Hat! Instructions
- Python 3 (not tested on Python 2)
- Python packages see
requirements.txt - Ansible for managing the cluster as a whole (
/playbooks)
Installation
- Clone the git repository:
git clone https://github.com/tlkh/prowler.git - Install dependencies by running
sudo pip3 install -r requirements.txton the controller Pi - Run
ansible-playbook playbooks/setup_node.ymlto install the required packages on worker nodes. - Clone the prowler and dispy repositories to the worker nodes using
ansible-playbook playbooks/clone_repos.yml - Run
clusterhat onon the controller Pi to ensure that all Pi Zeros are powered up. - Run
python3 cluster.pyon the controller Pi to start Prowler
To edit the range of IP addresses being scanned, edit the following lines in cluster.py:

Copyright (c) 2017 Timothy Liu
Source: https://github.com/tlkh/





