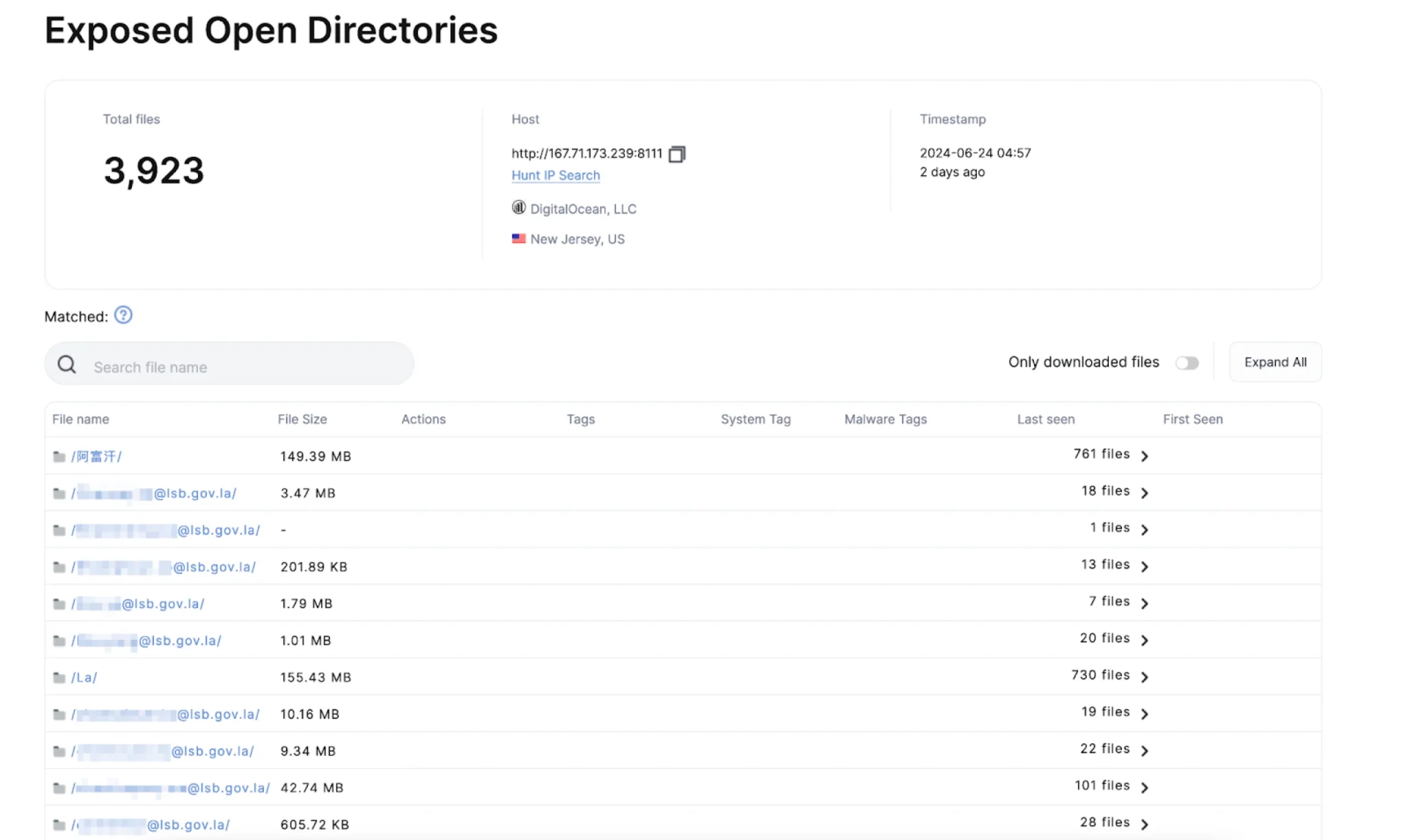
Screenshot of the suspicious open directory in Hunt
Nearly three years after the notorious ProxyLogon and ProxyShell vulnerabilities caused widespread havoc on Microsoft Exchange servers, these vulnerabilities have resurfaced with new targets. The Hunt Research Team recently identified a server likely exploiting these vulnerabilities to gain initial access and steal sensitive communications. This renewed activity has affected government entities across multiple regions, including Asia, Europe, and South America.
First disclosed in 2021, ProxyLogon and ProxyShell vulnerabilities have continued to pose significant risks. ProxyLogon exploits a server-side request forgery (SSRF) flaw, allowing attackers to send a specific web request with an XML payload to the Exchange Web Services (EWS) API endpoint. This enables the attacker to execute operations on the victim’s mailbox without needing to authenticate.
ProxyShell, comprising three vulnerabilities (CVE-2021-34473, CVE-2021-34523, and CVE-2021-31207), allows unauthenticated attackers to execute commands on the server via port 443. By leveraging legitimate services such as Autodiscover and the Messaging Application Programming Interface (MAPI), attackers can obtain a user’s distinguished name (DN) and security identifier (SID). With the SID, the attacker can forge an access token to communicate with EWS, impersonating the target user.
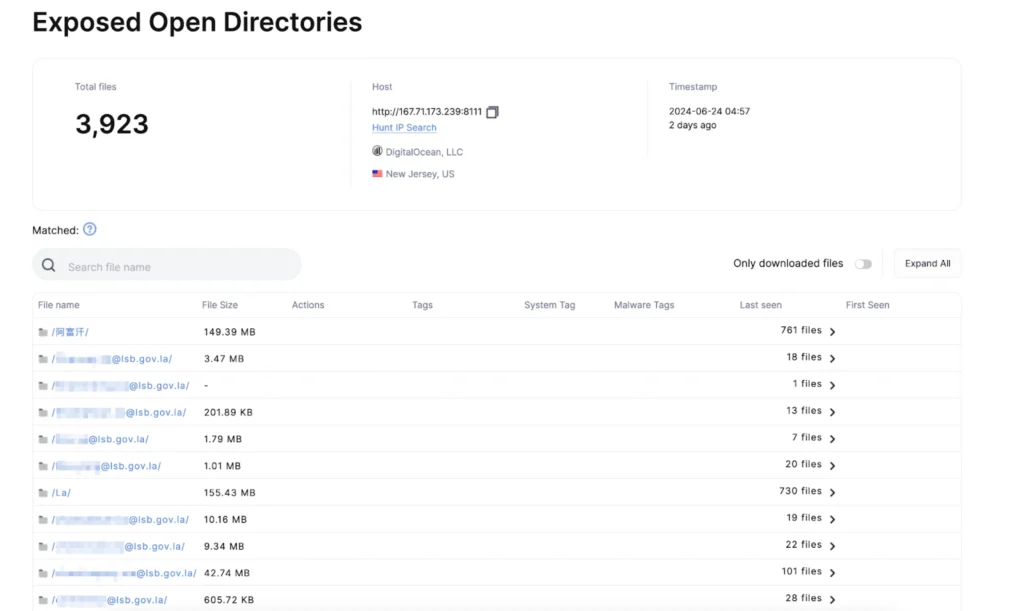
Hunt.io’s research began with the discovery of a server hosted on DigitalOcean at IP address 167.71.173_239, exposing an open directory on port 8111. What initially caught the team’s attention was the sheer volume of files—3,923 in total. To safeguard those targeted, the team obscured the email addresses in their report. The first folder in the directory, titled “阿富汗” (Afghanistan in Simplified Chinese), contained 761 files and was 149 MB in size. Other folders were similarly labeled by country names, such as “La” for Laos.
The server administrators quickly noticed the misconfiguration, and within less than 12 hours of the initial discovery, port 8111 stopped responding to requests. However, Hunt.io managed to download most of the hosted files before access was restricted. The server exposed an open directory revealing thousands of sensitive communications from ministries of defense, interior, and presidential offices in Afghanistan, Georgia, Argentina, and Laos.
The attackers appear to have carefully selected their targets, focusing on government entities involved in sensitive areas like defense, intelligence, and international relations. The stolen emails offer a glimpse into internal government communications and could potentially compromise national security.
While the exact motive behind these attacks remains unclear, the targeting of government entities suggests a potential espionage operation. Attribution remains challenging, but the use of advanced techniques and the targeted nature of the campaign point to a well-resourced and sophisticated threat actor.