pspy v1.2.1 releases: Monitor linux processes without root permissions
pspy – unprivileged Linux process snooping
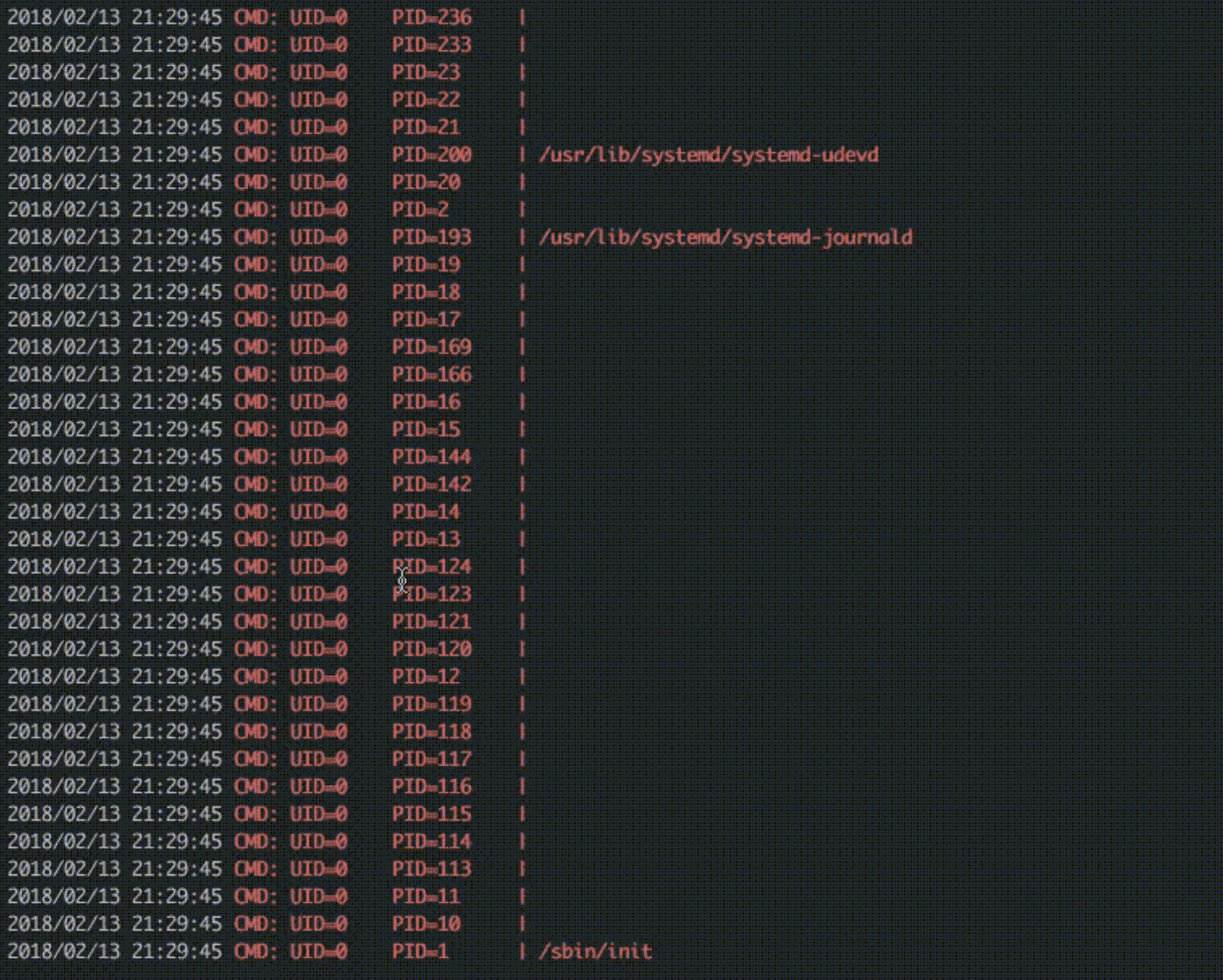
pspy is a command-line tool designed to snoop on processes without the need for root permissions. It allows you to see commands run by other users, cron jobs, etc. as they execute. Great for enumeration of Linux systems in CTFs. Also great to demonstrate to your colleagues why passing secrets as arguments on the command line is a bad idea.
The tool gathers it’s info from procfs scans. Inotify watchers placed on selected parts of the file system trigger these scans to catch short-lived processes.
How it works
Tools exist to list all processes executed on Linux systems, including those that have finished. For instance, there is forkstat. It receives notifications from the kernel on process-related events such as fork and exec.
These tools require root privileges, but that should not give you a false sense of security. Nothing stops you from snooping on the processes running on a Linux system. A lot of information is visible in procfs as long as a process is running. The only problem is you have to catch short-lived processes in the very short time span in which they are alive. Scanning the /procdirectory for new PIDs in an infinite loop does the trick but consumes a lot of CPU.
A stealthier way is to use the following trick. The process tends to access files such as libraries in /usr, temporary files in /tmp, log files in /var, … Using the inotify API, you can get notifications whenever these files are created, modified, deleted, accessed, etc. Linux does not require privileged users for this API since it is needed for many innocent applications (such as text editors showing you an up-to-date file explorer). Thus, while non-root users cannot monitor processes directly, they can monitor the effects of processes on the file system.
We can use the file system events as a trigger to scan /proc, hoping that we can do it fast enough to catch the processes. This is what pspy does. There is no guarantee you won’t miss one, but chances seem to be good in my experiments. In general, the longer the processes run, the bigger the chance of catching them is.
Changelog v1.2.1
- On startup, pspy ignores inotify events for 1 sec since it creates lot of them itself (
Draining file system events due to startup...). Many people experienced much longer waits though on some systems. This release should fix that.
Use

You can run pspy –help to learn about the flags and their meaning. The summary is as follows:
- -p: enables printing commands to stdout (enabled by default)
- -f: enables printing file system events to stdout (disabled by default)
- -r: list of directories to watch with Inotify. pspy will watch all subdirectories recursively (by default, watches /usr, /tmp, /etc, /home, /var, and /opt).
- -d: list of directories to watch with Inotify. pspy will watch these directories only, not the subdirectories (empty by default).
- -i: interval in milliseconds between procfs scans. pspy scans regularly for new processes regardless of Inotify events, just in case some events are not received.
- -c: print events in different colours. Red for new processes, green for new Inotify events.
The default settings should be fine for most applications. Watching files inside /usr is most important since many tools will access libraries inside it.
Copyright (C) 2018 DominicBreuker