PurplePanda: AUTOMATED Privilege Escalation IN THE CLOUD
PurplePanda
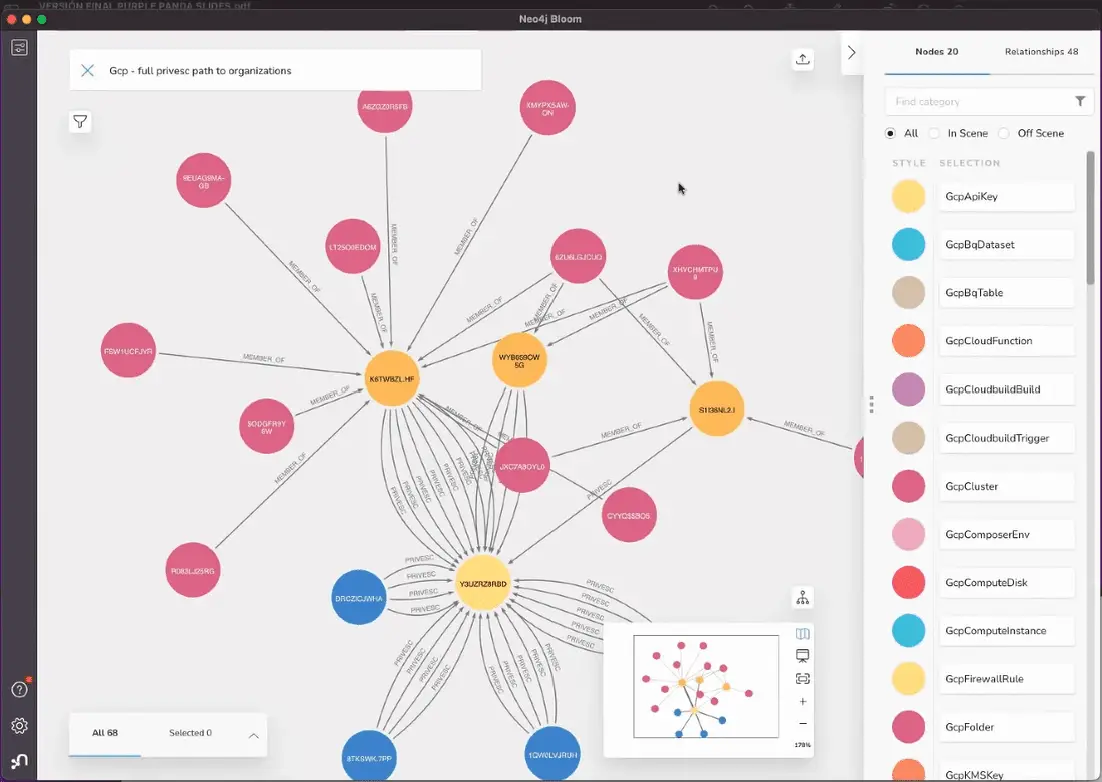
This tool fetches resources from different cloud/saas applications focusing on permissions in order to identify privilege escalation paths and dangerous permissions in the cloud/saas configurations. Note that PurplePanda searches both privileges escalation paths within a platform and across platforms.
The name comes from the animal Red Panda. This panda eats peas, just like Purple Panda, which can ingest API keys/tokens found by this PEASS. The color was changed to purple because this tool is meant mainly for Purple Teams (because it can be highly useful for both Blue and Red Teams).

For Blue/Purple Teams
Use credentials for each platform with at least admin read access to all the resources of the platform. This will help you to see exactly the privesc paths that can be abused within your configurations in each platform and across
For Red Teams
PurplePanda is also designed to be used by Red Teams. In general, cloud/saas platforms won’t give everyone access to read the configuration of the platform, that’s why PurplePanda supports the use of several keys for the same platform, in order to try to enumerate everything with all the keys you compromised and have the most accurate view of the configuration of the platform.
Supported platforms
- Google Cloud Platform (GCP): To understand how GCP security works and how to abuse roles and permissions read https://book.hacktricks.xyz/cloud-security/gcp-security
- Github: To understand how Github security works and how to bypass branch protections, steal secrets, privesc… read https://book.hacktricks.xyz/cloud-security/github-security
- Kubernetes (K8s): To understand how Kubernetes RBAC security works and how to abuse roles, privesc to other clouds… read https://book.hacktricks.xyz/cloud-security/pentesting-kubernetes
Install & Use
PurplePanda is (C) 2022-2022 Carlos Polop Martin.




