PurpleSpray
Password spraying is an effective technique available to adversaries that allows them to gain access or escalate privileges on Windows environments. This technique can be executed in different variations like using Kerberos or NTLM, targeting a domain host or several, using domain or local accounts, etc.
Different scenarios will leave different forensic artifacts behind which may require different detection analytics.
By automating the simulation of password spray attacks using different scenarios in properly monitored environments, PurpleSpray will generate relevant telemetry that can be used by detection teams to test the resilience of detection analytics.
PurpleSpray is an adversary simulation tool that executes password spray behavior under different scenarios and conditions with the purpose of generating attack telemetry in properly monitored Windows enterprise environments. Blue teams can leverage PurpleSpray to identify gaps in visibility as well as test the resilience, improve existing and build new detection analytics for password spraying attacks.
PurpleSpray currently supports two modules that leverage the SMB protocol for the spray scenarios.
PurpleSpray currently supports 2 modules. They both simulate an adversary performing spray attacks against Windows domain endpoints using the SMB protocol. To identify which users to spray and which endpoints to target, PurpleSpray will perform ldap queries and randomly select users/computers. By randomly choosing the spray targets, purple teams can identify areas of the network with log collection/indexing issues.
impacket_spray
This module simulates an adversary leveraging a rogue device to perform password spray attacks. This scenario can occur if an adversary has direct access to the network through physical access or an unauthorized VPN connection and uses a non domain joined device to execute the attacks.
impacket_spray leverages the impacket library to perform the spray attacks.
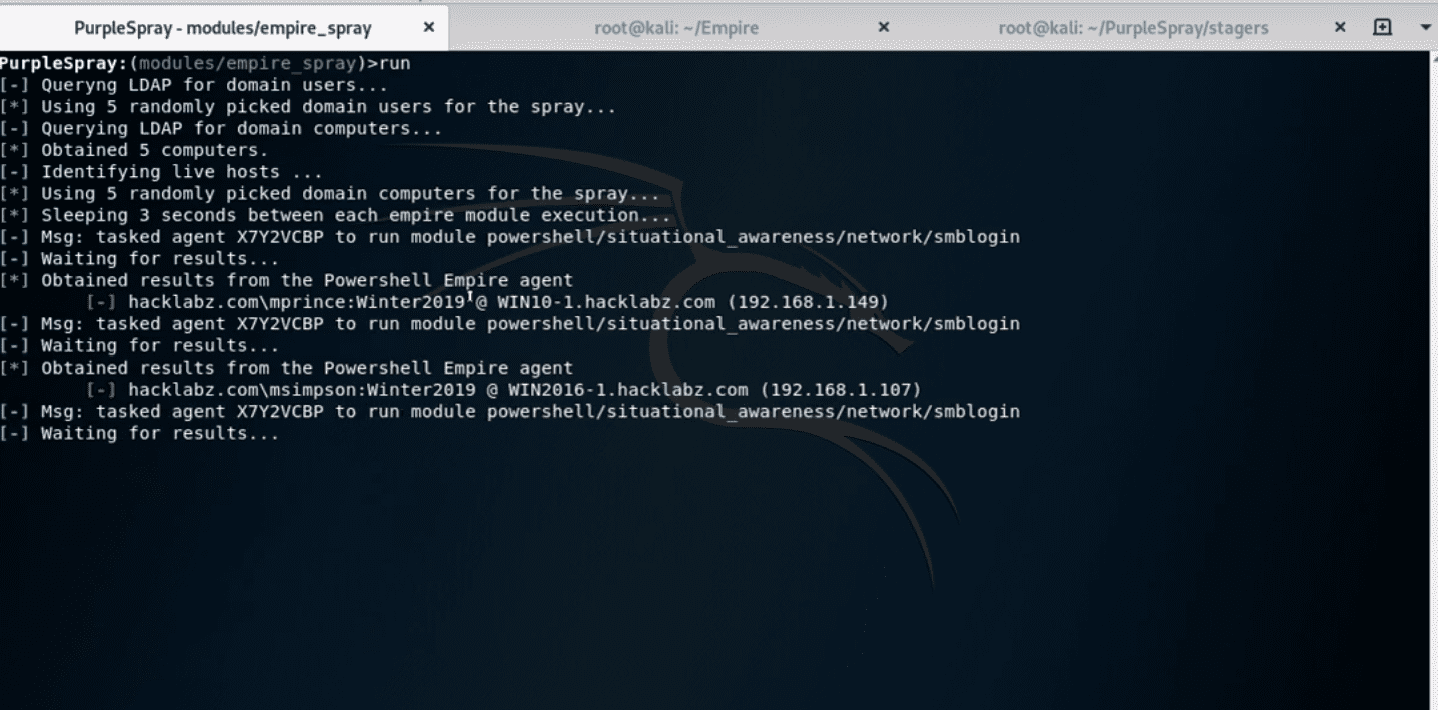
empire_spray
This module simulates an adversary leveraging a compromised host to perform password spray attacks. This scenario can occur if an adversary has obtained control of a domain joined computer through a spear phishing attack or any other kind of client side attack.
empire_spray leverages the Powershell Empire frameworks and its API to instruct Empire agents to perform password spray attacks by using the Invoke-SMBLogin module. A pull request to incorporate the module in the master branch is pending merge on the Empire’s repository. Until then, the module will have to be manually installed on Empire.
initialize
The initialize command is used to obtain the Empire agent that will be used for the spray simulations. When called, it will connect to the Empire server defined on the settings and leverage any existing agents already checking in. If no agents are found, it will use a modified version of impacket’s wmiexec to execute an Empire stager on a remote simulation host defined on the settings.
stagers
The stagers command will generate 5 Powershell Empire payloads and write them to the ‘stagers’ folder. These can be used to manually obtain an Empire agent if the initialize command failed to get one. After manually executing one of the stagers on a simulation host to obtain an agent, the ‘initialize’ needs to be run to leverage the new agent.
Install
git clone https://github.com/mvelazc0/PurpleSpray.git
pip install -r PurpleSpray/requirements.txt
Use
Copyright (c) 2019, mvelazc0
All rights reserved.