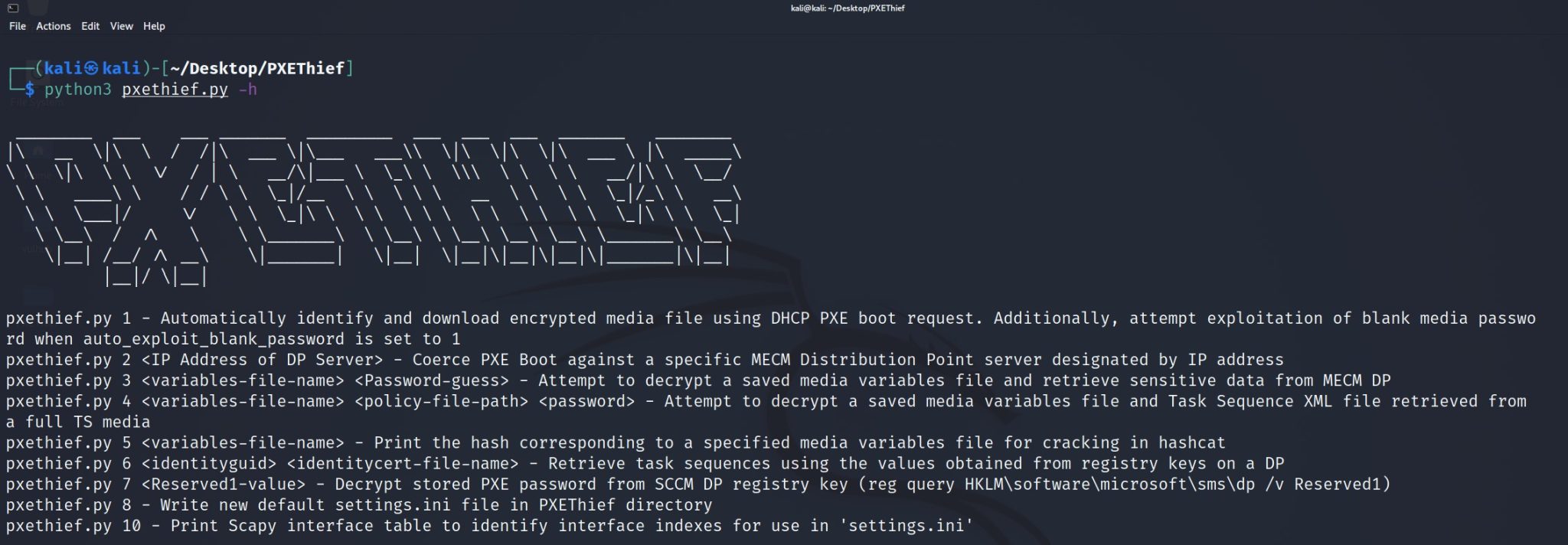
PXEThief
PXEThief is a set of tooling that implements attack paths discussed at the DEF CON 30 talk Pulling Passwords out of Configuration Manager against the Operating System Deployment functionality in Microsoft Endpoint Configuration Manager (or ConfigMgr, still commonly known as SCCM). It allows for credential gathering from configured Network Access Accounts and any Task Sequence Accounts or credentials stored within ConfigMgr Collection Variables that have been configured for the “All Unknown Computers” collection. These Active Directory accounts are commonly over-permissioned and allow for privilege escalation to administrative access somewhere in the domain, at least in my personal experience.
Likely, the most serious attack that can be executed with this tooling would involve PXE-initiated deployment being supported for “All unknown computers” on a distribution point without a password, or with a weak password. The overpermissioning of ConfigMgr accounts exposed to OSD mentioned earlier can then allow for a full Active Directory attack chain to be executed with only network access to the target environment.

Limitations
- Proxy support for HTTP requests – Currently only configurable in code. Proxy support can be enabled on line 35 of
pxethief.pyand the address of the proxy can be set on line 693. I am planning to move this feature to be configurable in ‘settings.ini’ in the next update to the code base - HTTPS and mutual TLS support – Not implemented at the moment. Can use an intercepting proxy to handle this though, which works well in my experience; to do this, you will need to configure a proxy as mentioned above
- Linux support – PXEThief currently makes use of pywin32 in order to utilise some built-in Windows cryptography functions. This is not available on Linux, since the Windows cryptography APIs are not available on Linux 😛 The Scapy code in pxethief.py, however, is fully functional on Linux, but you will need to patch out (at least) the include of win32crypt to get it to run under Linux