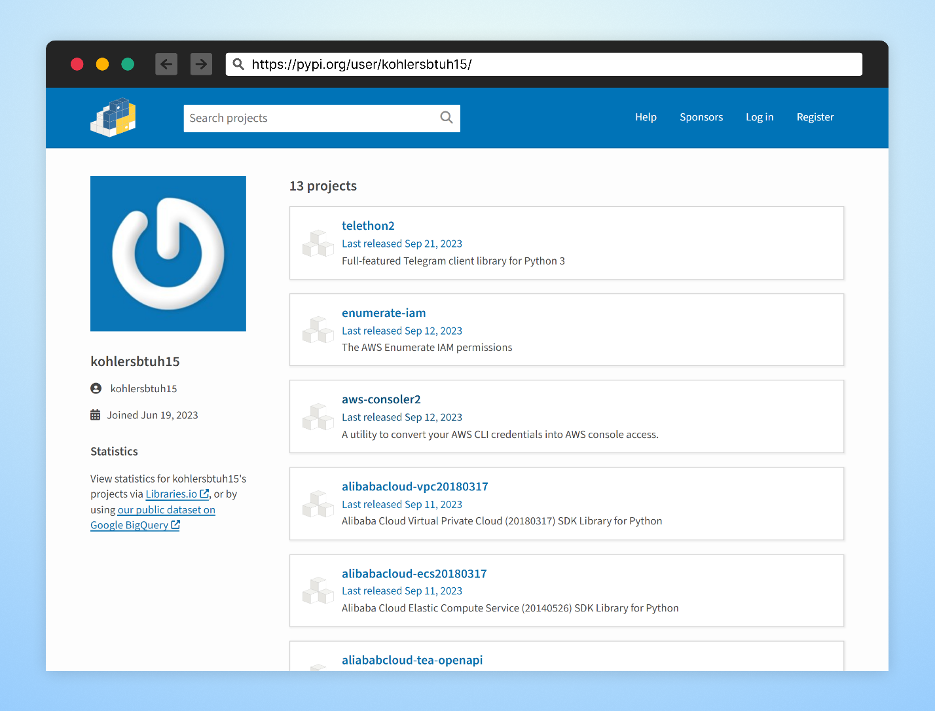
The kohlersbtuh15 user account
In recent developments, a new digital adversary is lurking in the open-source realm, targeting unsuspecting developers and platforms such as Telegram, AWS, and Alibaba Cloud. This threat, uncovered by Checkmarx researchers, is a concealed malware introduced by an attacker under the pseudonym “kohlersbtuh15” via the PyPi package manager.

What sets apart this malevolent player’s strategy from conventional attacks is the deceptive method of hiding malicious code deep within Python packages. Typically, attackers plant malicious code in setup files that auto-execute upon installation. Instead, kohlersbtuh15 embeds these scripts within specific functions. This ensures the code only runs when a particular function is triggered during regular operations. By doing so, the malware can elude many security tools and target specified functionalities.
The attacker banked on two primary techniques: Typosquatting and Starjacking.
- Typosquatting: This method exploits human errors, especially typos made by developers when installing packages. By creating malicious packages closely named after popular ones, developers can inadvertently install these deceptive packages. Such packages not only replicate legitimate ones but also introduce hidden malicious dependencies or scripts.
- Starjacking: In the open-source world, package popularity often serves as a gauge of its reliability. Developers tend to trust packages with high GitHub statistics, a metric showcased by package managers. However, with no verification for these statistics, it’s a piece of cake for attackers to manipulate them. Starjacking involves linking a malicious package to an unrelated but popular GitHub repository, creating an illusion of its trustworthiness.
In a bid to amplify the deception, the attacker combined these techniques in several packages, the notable one being “Telethon2”.
“Telethon2” stands out for its deceptiveness. A twist on the acclaimed “Telethon” package with a staggering 69 million downloads, this counterfeit package tricks users by using the original “telethon” GitHub repository. The attacker meticulously copied the authentic “telethon” source code, except for two insidious lines of code within the “telethon/client/messages.py” file. This code remains dormant until the “send message” function is triggered, fetching external content and executing OS commands.
Similarly, another package, “enumerate-iam”, was crafted leveraging a popular GitHub repository. This malware aims to pilfer sensitive credentials, exemplifying the importance for GitHub maintainers to have placeholder packages to thwart such deceptive tactics.
The attacker’s intention was clear: to compromise and exploit users of major platforms like Telegram, AWS, and Alibaba Cloud. The stakes are high as the repercussions extend beyond mere system compromises. It can lead to potential leaks of critical data, including AWS cloud information, business intelligence from Alibaba Cloud, and even personal communications on Telegram.
The malicious packages list:
- enumerate-iam
- aliababcloud-tea-openapi
- alibabacloud-vpc20180317
- python-cos-sdk-v5
- alibabacloud-ecs20180317
- aliyun-oss2
- python-aliyun-sdk-kms
- python-aliyun-sdk-ecs
- python-aliyun-sdk-rds
- python-aliyun-sdk-core
- telethon2
- tencentcloud-python-sdk
- arangodba
- aws-consoler2
In a nutshell, these findings are a stark reminder of the evolving nature of cyber threats. As attackers devise innovative strategies, the onus is on the developer community and platforms to stay vigilant and prioritize cybersecurity.