Python Developers Beware: Attackers Sneak Malware into Popular Package Manager
Open-source code is the backbone of modern software, but it’s becoming a prime target for cybercriminals. ReversingLabs researchers recently unmasked a sneaky new attack on PyPI, Python’s package manager. The attackers hid malicious code in packages designed to mimic legitimate ones, using a technique called DLL sideloading to slip past security defenses. This attack highlights the dangers lurking in software supply chains and the urgent need for vigilance.
Finding reliable open-source code is a constant challenge for developers. The vastness of the open-source world makes it easy for bad actors to plant malicious packages. In the case of this recent attack, ReversingLabs uncovered two suspicious PyPI packages: NP6HelperHttptest and NP6HelperHttper. These packages employed typosquatting – the deliberate use of names deceptively similar to legitimate ones (in this case, NP6HelperHttp) – to lure unsuspecting developers into downloading them.
However, typosquatting was only the first step in the attackers’ plan. The real danger lay in their use of DLL sideloading, a technique that allows malicious actors to disguise their code within seemingly legitimate software components.

Malware infection stages | Image: ReversingLabs
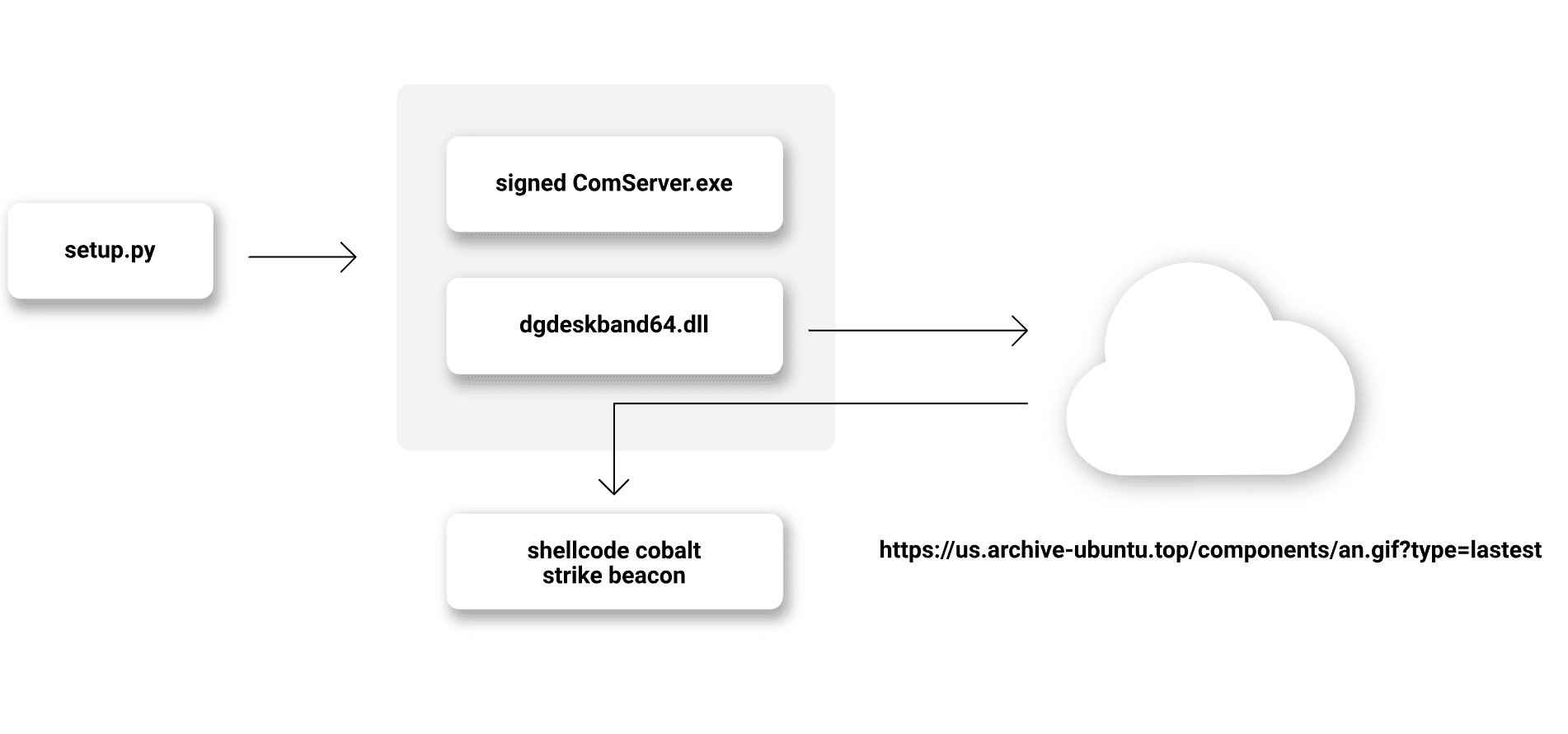
Delving deeper into the mechanics of these packages, ReversingLabs discovered that both contained a setup.py script with custom code designed to download and execute two files: a legitimate application, ComServer.exe, from Kingsoft Corp, and a nefarious file, dgdeskband64.dll, intended to fetch and run a second-stage payload.
This method of concealing malicious code within a setup.py script is not novel but remains a potent strategy for cybercriminals to deploy malware discreetly, exploiting the trust placed in signed legitimate applications to sidestep security defenses.
The PyPI attack serves as a grim reminder of the increasingly sophisticated tactics employed by cybercriminals to exploit the open-source ecosystem. Typosquatting, DLL sideloading, and other techniques threaten the integrity of software supply chains. This places an onus on everyone involved with software development to be aware of these risks.





