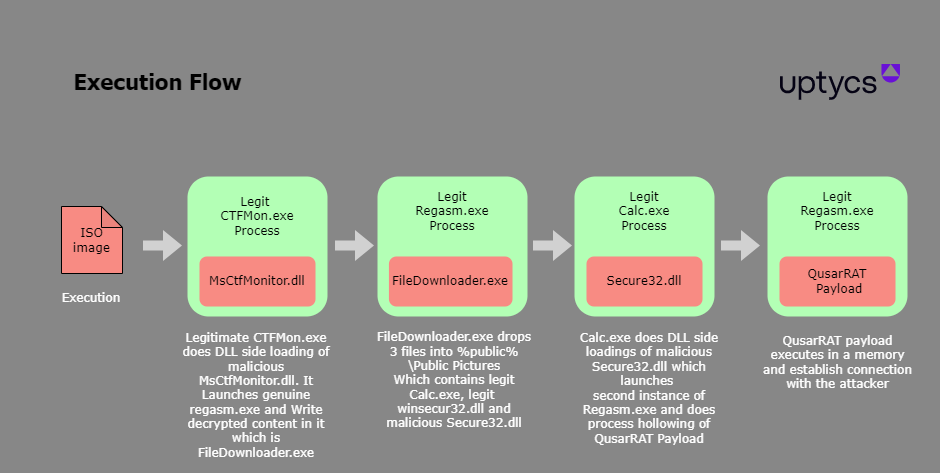
QuasarRAT execution flow | Image: Uptycs
The open-source Remote Access Trojan, Quasar RAT, employs the DLL Sideloading technique to discreetly extract data from infected Windows-based devices.
According to Uptycs researchers, this method capitalizes on the inherent trust these files enjoy within the Windows environment. Their report meticulously details how the malware exploits “ctfmon.exe” and “calc.exe” during its assault.
Quasar RAT, also known as CinaRAT or Yggdrasil, is a legitimate C#-based remote administration tool. It is adept at gathering system information, listing active applications, retrieving files, capturing keystrokes, taking screenshots, and executing arbitrary shell commands.

Cybercriminals frequently employ the DLL Sideloading technique, allowing them to launch their own payloads by substituting the DLL files of trusted programs with malicious ones.
Uptycs identifies an ISO image as the attack’s point of origin, which encompasses three files. When the executable within the image is activated, it triggers the loading of the “MsCtfMonitor.dll” library, wherein the malevolent code is concealed.
This concealed code is an alternate executable that integrates into “Regasm.exe,” a Windows assembly registration tool, to initiate the subsequent attack phase. It then executes the genuine “calc.exe” file, essentially the system calculator, albeit with a malicious DLL library. Ultimately, it is this calculator that introduces the Quasar RAT Trojan into the victim’s computer.
The Trojan establishes a connection with a remote server, consistently transmitting information about the compromised system. Furthermore, it configures a reverse proxy server, ensuring swift access to the endpoint.
The exact entities behind this attack remain unclear, as does the specific vector employed for its initiation. However, researchers speculate that its dissemination likely occurred via phishing emails. Experts also reiterated the importance of caution when dealing with dubious emails, links, or attachments, as these often lead to systems becoming infected with malicious software.