Raccoon
Raccoon is a tool made for reconnaissance and information gathering with an emphasis on simplicity.
It will do everything from fetching DNS records, retrieving WHOIS information, obtaining TLS data, detecting WAF presence and up to threaded dir busting and subdomain enumeration. Every scan outputs to a corresponding file.
As most of Raccoon’s scans are independent and do not rely on each other’s results, it utilizes Python’s asyncio to run most scans asynchronously.
Raccoon supports Tor/proxy for anonymous routing. It uses default wordlists (for URL fuzzing and subdomain discovery) from the amazing SecLists repository but different lists can be passed as arguments.
Features
- DNS details
- DNS visual mapping using DNS dumpster
- WHOIS information
- TLS Data – supported ciphers, TLS versions, certificate details and SANs
- Port Scan
- Services and scripts scan
- URL fuzzing and dir/file detection
- Subdomain enumeration – uses Google dorking, DNS dumpster queries, SAN discovery and bruteforce
- Web application data retrieval:
- CMS detection
- Web server info and X-Powered-By
- robots.txt and sitemap extraction
- Cookie inspection
- Extracts all fuzzable URLs
- Discovers HTML forms
- Retrieves all Email addresses
- Scans target for vulnerable S3 buckets and enumerates them for sensitive files
- Detects known WAFs
- Supports anonymous routing through Tor/Proxies
- Uses asyncio for improved performance
- Saves output to files – separates targets by folders and modules by files
Installation
pip install raccoon-scanner
Usage
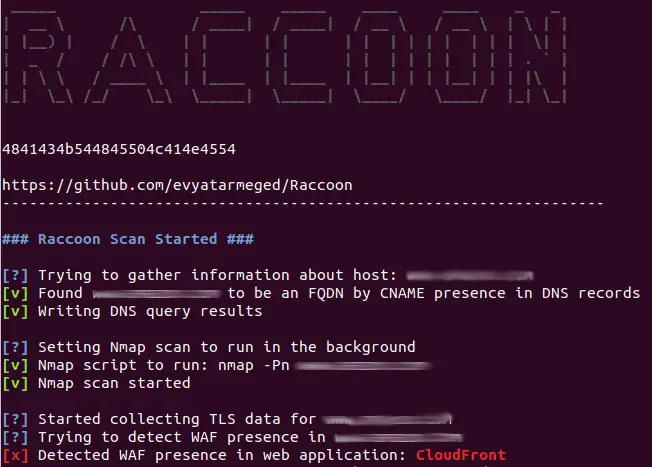

Web application data including vulnerable S3 bucket:
HTB challenge example scan:
Nmap vulners scan results:
Results folder tree after a scan:
Copyright (c) 2018 Evyatar Meged
Source: https://github.com/evyatarmeged/



