radiocarbon: Leak File Analyzer
What is RadioCarbon?
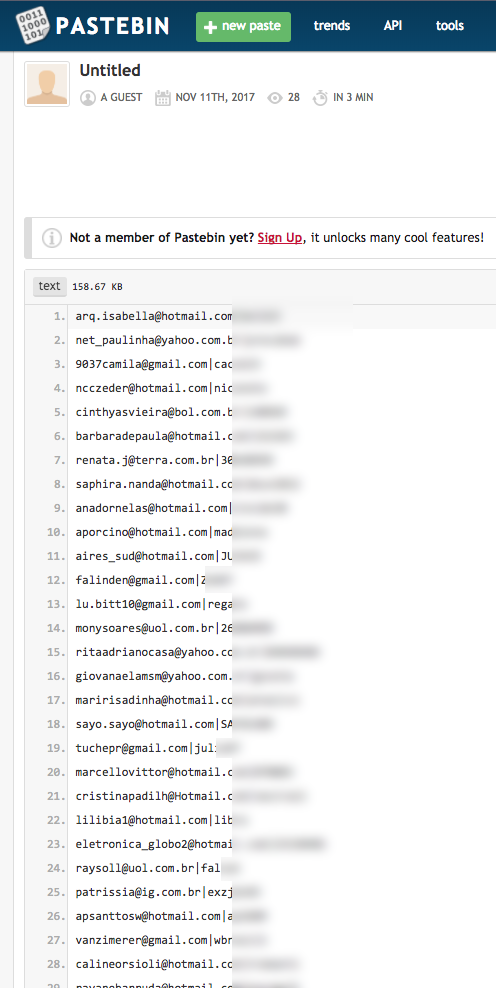
Typically you get leaked credentials that look like the list in the following screenshot. They consist of email addresses or usernames, cleartext passwords or password hashes.
The problem with those leaked files is, that you have no idea how relevant they are and who to inform about the leak.
- They could be 15 years old and obsolete
- They typically don’t indicate the origin of the leaked credentials
The Idea
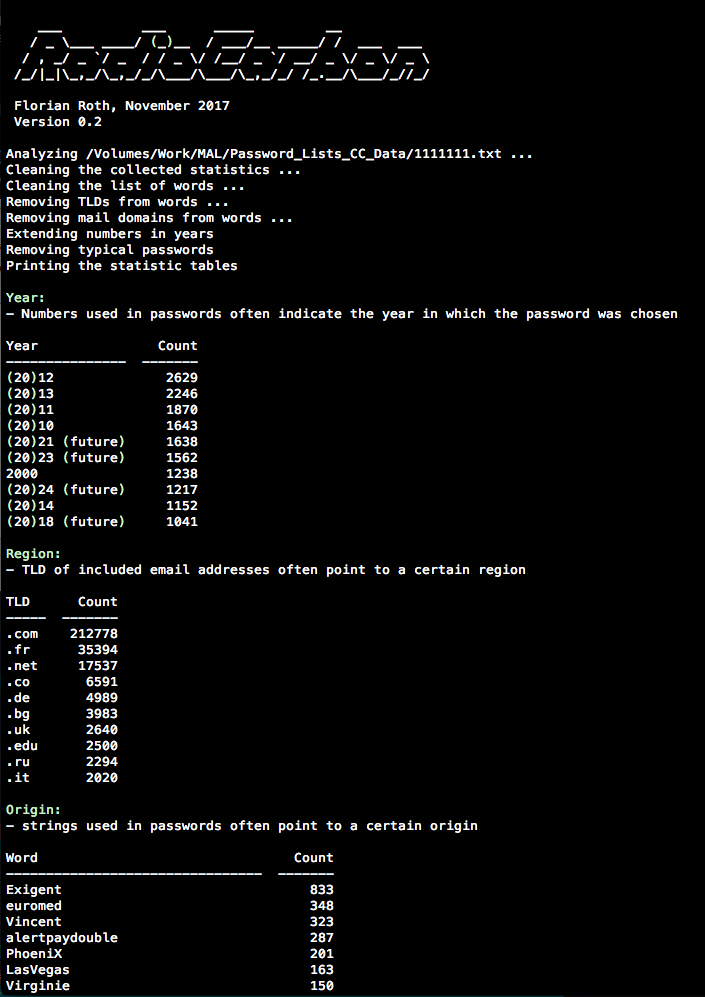
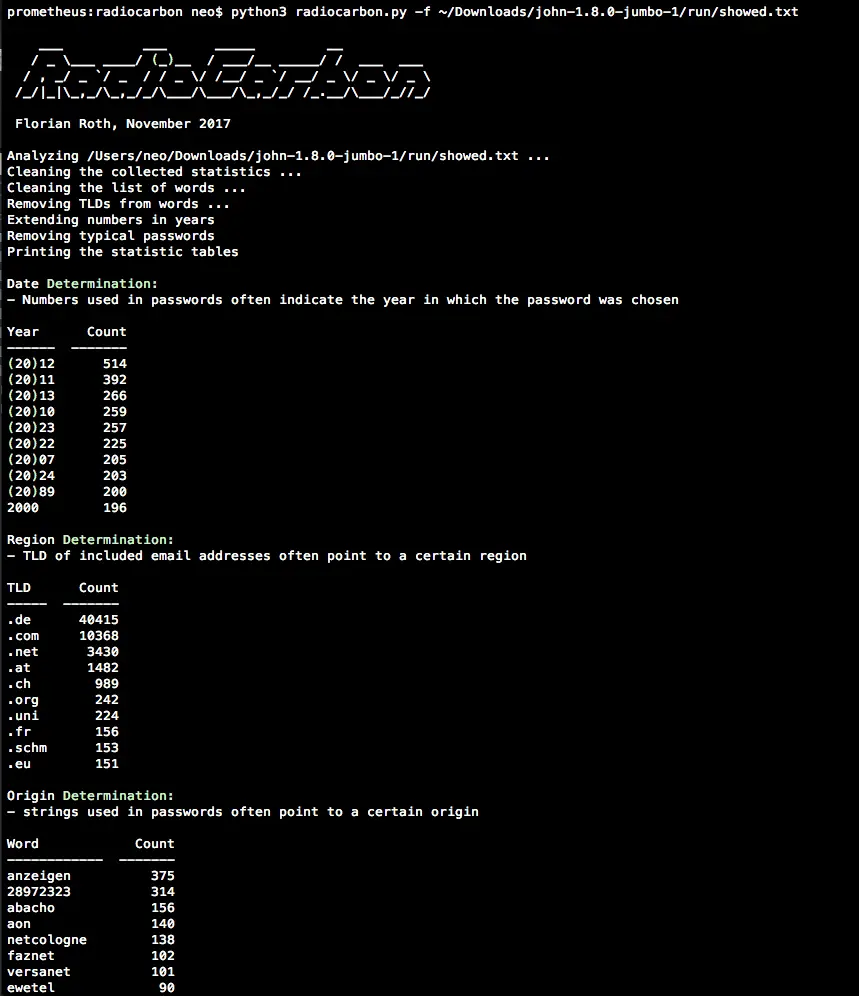
The idea behind RadioCarbon uses the fact that the users of the service provide indicators for the origin and the age of the leak by choosing certain passwords or email addresses.
- Users include the current year in their passwords (e.g.
stephan2017,Mercedes17!,pass2016) - Users typically don’t include a year in the password that is in the future (e.g.
pass2022,website2045) - Users include the name of the website/service in their passwords (e.g.
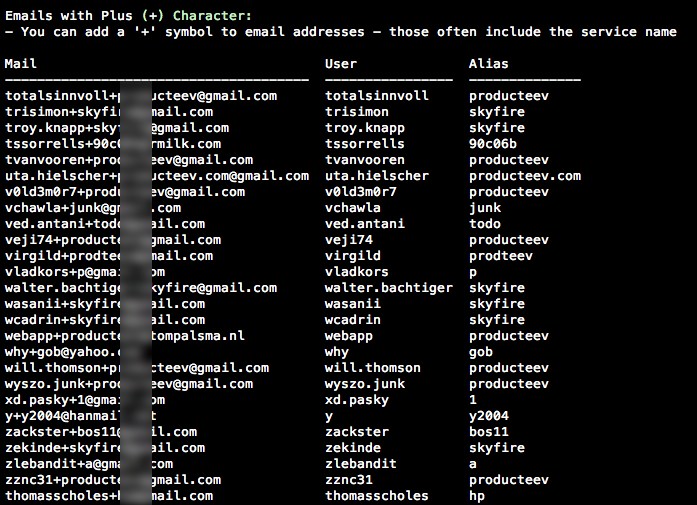
website1234,pass4website) - Users use one time email addresses for the registration (e.g.
website-12@mailinator.com,mail4website@maildrop.cc) - Users can use the “+” character to easily create new email aliases for certain purposes (e.g.
john.smith+onlineshop.com@gmail.com)
The Inner Workings
RadioCarbon uses extractions based on regular expressions, statistics, and filter mechanisms to generate the report panels.
- Reads password lists from the
./passlistssubfolder (used for filtering) - Reads the leaked file
- Extracts
words, 2 and 4 characternumbers, top-level domainstldsand one-time emailsonetimemailsfrom the leak - Processing the lists – removes standard passwords from
words, removing numbers that can’t be years, prepending(20)for better readability, removingtldsfromwords - Prints the result tables
Issues
- If the user field contains a nickname and no email address, the region analysis fails
- If the password field contains a password hash and not a clear text password, the analysis is strongly hindered
Prepare a Leak File for Analysis
If a leaked file doesn’t contain th clear text passwords, use john the cracker or another password cracker to pre-process the file before using it as input for RadioCarbon.
Download
git clone https://github.com/Neo23x0/radiocarbon.git
Usage