
Raspberry Robin, also known as Roshtyak, stands out as a highly advanced malicious downloader. Discovered in 2021, it has gained notoriety for its use of infected USB drives and sophisticated techniques, posing a significant challenge to researchers and organizations alike. Zscaler ThreatLabz recently published an in-depth analysis revealing the malware’s multi-layered execution, advanced obfuscation, and anti-analysis methods.
Raspberry Robin uses an intricate eight-layer execution process, each layer serving distinct purposes such as emulation detection, decompression, and anti-analysis. Notably, the sixth layer incorporates most of the anti-analysis techniques and deploys a decoy payload when such methods fail. As Zscaler notes, “The core functionality of Raspberry Robin is unwrapped after executing a series of different layers.”
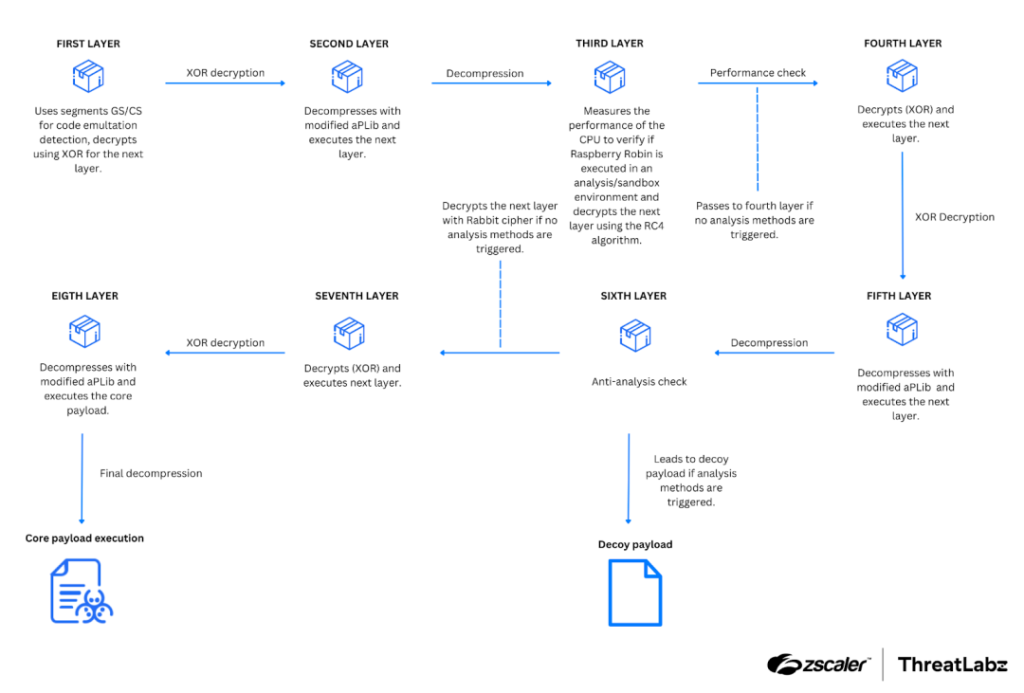
The malware employs sophisticated anti-analysis methods, including checks for debugging tools, system configurations, and sandbox environments. It even modifies process environment block (PEB) fields to thwart detection. According to Zscaler, Raspberry Robin’s ability to “deploy a decoy payload to mislead researchers and security tools” makes it particularly challenging to analyze.
Raspberry Robin leverages control flow flattening, Mixed Boolean-Arithmetic (MBA) operations, and custom encryption algorithms. Each obfuscated function includes an encrypted array table used for decrypting strings and mapping variables. Zscaler highlights that “the implemented control flow flattening method […] makes the analysis more tedious and time-consuming.”
The malware integrates a TOR client for encrypted communication with its command-and-control (C2) servers. It verifies TOR connectivity through onion domains and uses custom encryption layers to secure data exchanges. This ensures anonymity and complicates detection efforts.
Raspberry Robin employs exploits such as CVE-2024-26229 and CVE-2021-31969 for local privilege escalation. These exploits are dynamically decrypted and injected into target processes using advanced techniques like KernelCallbackTable injection. Zscaler reports that “the choice of exploit depends on the Windows version of the compromised host.”
Additionally, the malware bypasses User Account Control (UAC) through several methods, including modifying registry values and using legitimate Windows utilities.
Raspberry Robin demonstrates self-propagation capabilities through RDP and SMB. It uses tools like PsExec and PAExec to replicate itself across a network. Its persistence is achieved by modifying registry keys, leveraging Windows Defender exclusions, and utilizing randomly generated filenames for its binaries.
Raspberry Robin downloader represents a significant advancement in malware design, combining obfuscation, evasion, and exploitation to ensure its longevity and impact. Zscaler ThreatLabz’s meticulous analysis highlights the malware’s complexity and the need for robust defenses. As researchers noted, “Raspberry Robin proves its uniqueness by combining its capabilities with several applied obfuscation techniques.”
Related Posts:
- One-Day Exploits, Stealthy Tactics: Why Raspberry Robin Worm is a Cybersecurity Nightmare
- Zscaler found 150 Android apps infected with Windows malware
- Zscaler Report: 300% increase in phishing attacks delivered over SSL
- All Raspberry Pi Devices were not affected by the Meltdown and Spectre Vulnerabilities