rastrea2r: Collecting & Hunting for IOCs with gusto and style
Ever wanted to turn your AV console into an Incident Response & Threat Hunting machine? Rastrea2r (pronounced “rastreador” – hunter- in Spanish) is a multi-platform open source tool that allows incident responders and SOC analysts to triage suspect systems and hunt for Indicators of Compromise (IOCs) across thousands of endpoints in minutes. To parse and collect artifacts of interest from remote systems (including memory dumps), it can execute sysinternal, system commands and other 3rd party tools across multiples endpoints, saving the output to a centralized share for automated or manual analysis. By using a client/server RESTful API, rastrea2r can also hunt for IOCs on disk and memory across multiple systems using YARA rules. As a command line tool, it can be easily integrated within McAfee ePO, as well as other AV consoles and orchestration tools, allowing incident responders and SOC analysts to collect forensic evidence and hunt for IOCs without the need for an additional agent, with ‘gusto’ and style!
Install
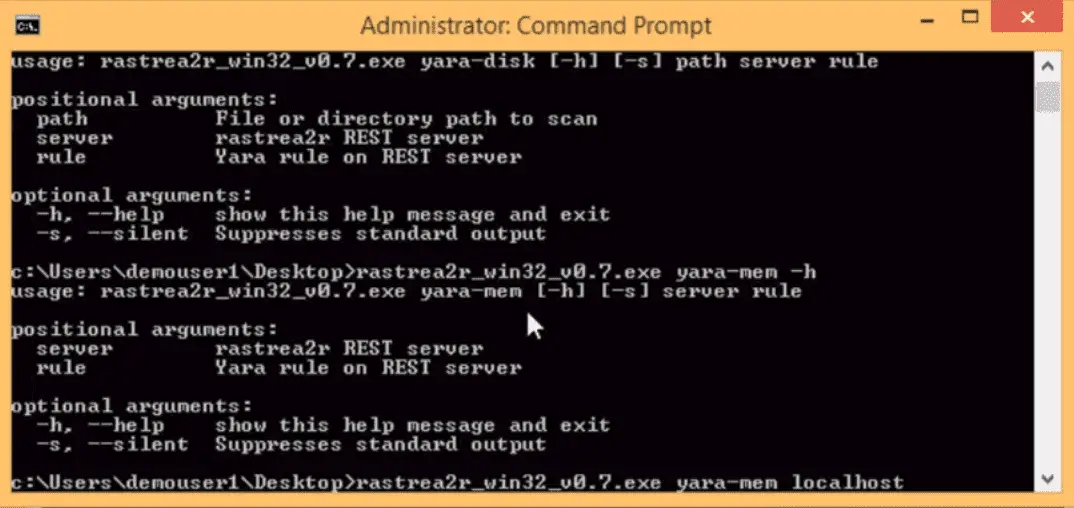
Executing rastrea2r on Windows
Use
Demo
Copyright (c) 2018 rastrea2r
Source: https://github.com/rastrea2r/