recon.sh: toolset to track & organize output of reconnaissance tools
recon.sh
This tool is for the computer hacking community and gives a framework for storing reconnaissance (recon) information. Recon is a tedious and continuous process that involves mentally processing and parsing command output. Conclusions drawn from this output can lead to new insights about an asset or may even identify security vulnerabilities. In proper recon, assets are scanned on regular bases and the output of the commands are compared. The wrappers in this tool allow you to collect recon information from multiple nodes in a single git repository and gives an easy interface to search it.
Installation
git clone git clone git@github.com:jobertabma/recon.sh
To make it easier to execute this script helper from the command line, add the following line to your profile:
alias recon.sh=~/location/of/recon.sh
It’s recommended to have recon.sh commit to a private repository. Create one for yourself, clone it locally, and run:
recon.sh init ~/location/of/recon-data
Tracking
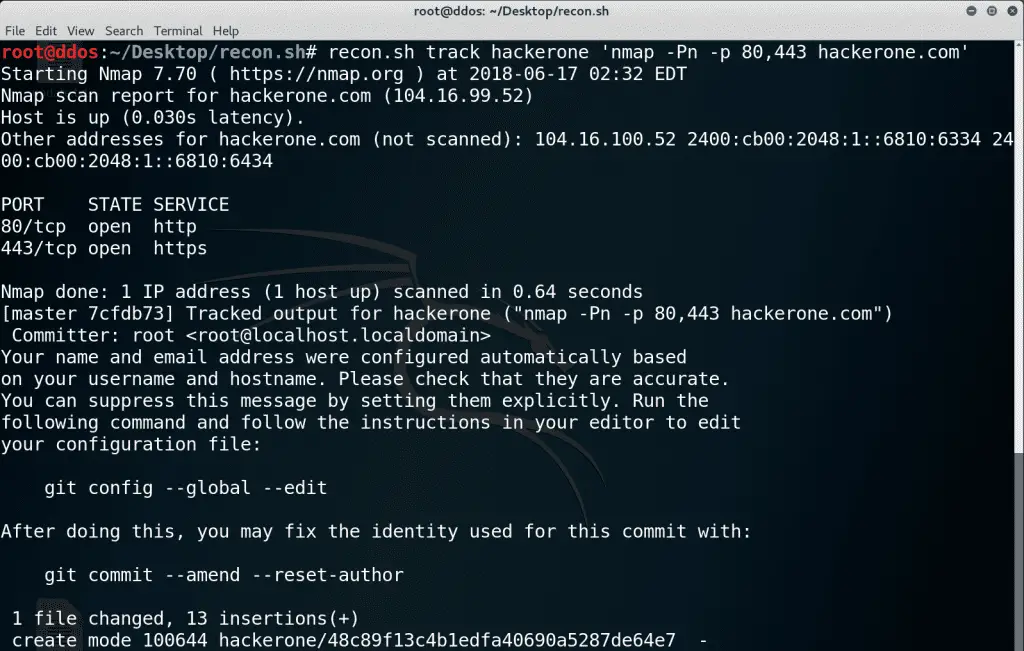
When the tool is properly installed, an output of commands can be captured globally and can be stored in the designated git repository. Consider the following nmap command:
recon.sh track hackerone ‘nmap -Pn -p 80,443 hackerone.com’
In the example above, the output of the command is shown in the terminal as it normally would. However, when it is finished, it commits it to the directory with a special name. When you’d run the same command, it’d overwrite the file. This is especially useful when comparing the output of the same command with git diff.
Search
There’s a lot of different reasons why you’d want to come back and search for output. The recon.sh search tool does exactly that. It allows a regular expression (ERE) to be passed to it to search through command output. It’ll search through commands as well as the output.
recon.sh search '(80|443)'
Source: https://github.com/jobertabma





