Red-Shadow
Lightspin AWS IAM Vulnerability Scanner
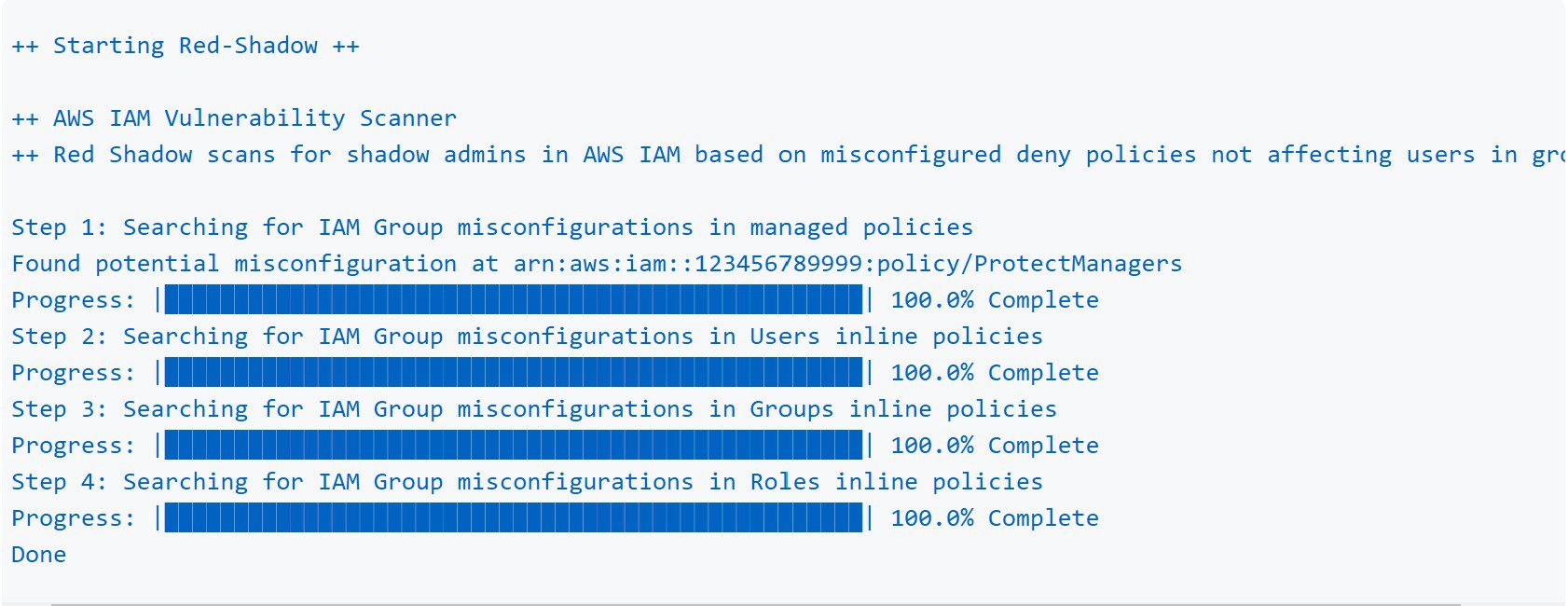
Scan your AWS IAM Configuration for shadow admins in AWS IAM based on misconfigured deny policies not affecting users in groups discovered by Lightspin’s Security Research Team.
The tool detects the misconfigurations in the following IAM Objects:
- Managed Policies
- Users Inline Policies
- Groups Inline Policies
- Roles Inline Policies
Research Summary
AWS IAM evaluation logic for deny policies applied to groups does not work the same way as most security engineers may be used to with other authorization mechanisms.
Suppose a policy with a group resource has an explicit deny. In that case, this will only impact group actions and not user actions, opening organizations up to misconfiguration and vulnerabilities if they assume the process to be the same as with Active Directory, for example.
Example for vulnerable json policy:
In this example, the policy should deny any iam action done by users, groups, or roles with that policy attached to, towards the group called managers.
The fact is that simple IAM actions like iam:ChangePassword would work as the deny policy is ineffective.
Link to the full security research blog
Detection
AWS IAM has a clear separation between user object actions and group object actions.
The following list includes the user object actions the tool is scanning over deny policies affecting groups (besides wildcard):
Many of the user object actions mentioned above can easily lead to a privilege escalation or compromising the account, such as resetting the admin’s password, deactivating the root account MFA, and more.
Install & Use
Copyright (C) 2021 azarzar15