Redline Stealer Malware Evolves with Sneaky New Tricks, Spreads Globally
McAfee Labs researchers have uncovered a dangerous new variant of the Redline Stealer malware that uses clever obfuscation tactics and aggressive social engineering to trick victims and evade detection. This strain is rapidly spreading worldwide, already impacting North America, South America, Europe, Asia, and Australia.

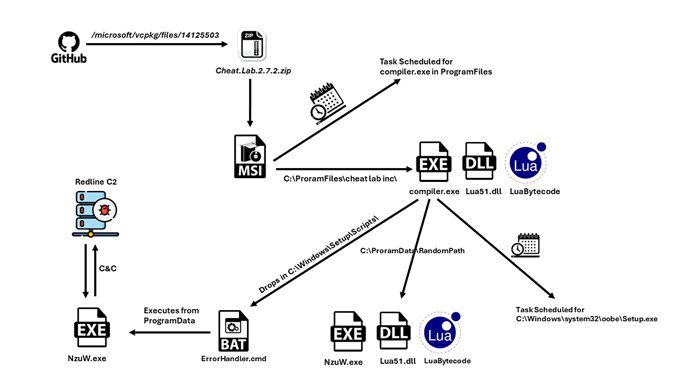
Infection Chain | Image: McAfee Labs
A Stealthy Infiltration Leveraging Lua
The new variant of Redline Stealer harnesses the power of Lua bytecode, a technique that significantly obfuscates its malicious intentions. Instead of relying on more recognizable scripting languages like PowerShell or JScript, the attackers have embedded the malicious code in a Lua script. This script is compiled and executed at runtime, making it particularly difficult for traditional antivirus solutions to detect malicious activities before it’s too late.
The Misuse of GitHub and Microsoft’s Reputation
Threat actors have abused GitHub’s platform, specifically using a repository under Microsoft’s official account to host the malware-laden file named Cheat.Lab.2.7.2.zip. This misuse of reputable services adds a layer of perceived legitimacy to the malicious file, potentially tricking more vigilant users into downloading the malware.
The Infection Mechanism Unpacked
Upon execution, the trojan employs a multi-stage attack:
- Supply Chain Compromise: The malware is initially hosted on a legitimate Microsoft GitHub repository, undermining standard security checks.
- Lua Bytecode for Stealth: The core malicious functionality is hidden within compiled Lua bytecode, making analysis and blocking by traditional antivirus solutions more challenging.
- Aggressive Persistence: Multiple techniques, including scheduled tasks and the abuse of legitimate Windows components, ensure the malware’s execution even after the system reboots.
- Data Theft Focus: The malware targets a range of sensitive information, including system identifiers, geolocation data, screenshots, and potentially even more as researchers continue to analyze the bytecode.
Advanced Persistence Techniques
The Redline Stealer malware showcases advanced persistence mechanisms:
- The malware creates a scheduled task to execute the primary malicious executable, misleadingly named
compiler.exe, which loads and executes the Lua bytecode. - In a fallback technique, it copies essential files to another directory with a long, random path, ensuring its operation even if the original files are detected and deleted.
- A custom script named
ErrorHandler.cmdis strategically placed in the Windows directory, set to execute when system errors occur, thus exploiting a lesser-known Windows feature to maintain persistence.
C2 Communication and Data Exfiltration
The communication with the command and control (C2) server occurs over HTTP. The malware is designed to perform tasks assigned by the C2 server, such as taking screenshots, which are then sent back to the attackers encoded in base64. This stealthy data exfiltration process illustrates the capability of the Redline Stealer to not only infiltrate systems but also to extract sensitive information without being noticed.
Decoding the Malicious Script
Further analysis of the Lua script revealed complex decoding mechanisms embedded within it. The script contains multiple encrypted data strings that are meticulously decoded during execution, illustrating the lengths to which attackers go to hide their tracks and avoid detection by static analysis tools.
Impact and Recommendations
The Redline Stealer is known for its ability to steal passwords, browser data, cryptocurrency wallets, and other valuable information. This data could be exploited for identity theft, financial fraud, or further compromise of corporate systems.
Ongoing Analysis
Security researchers are continuing to analyze the full capabilities of this Redline Stealer variant. Organizations and individuals must maintain a proactive security posture to safeguard against this evolving threat.
For detailed technical analysis, refer to the McAfee Labs report.





