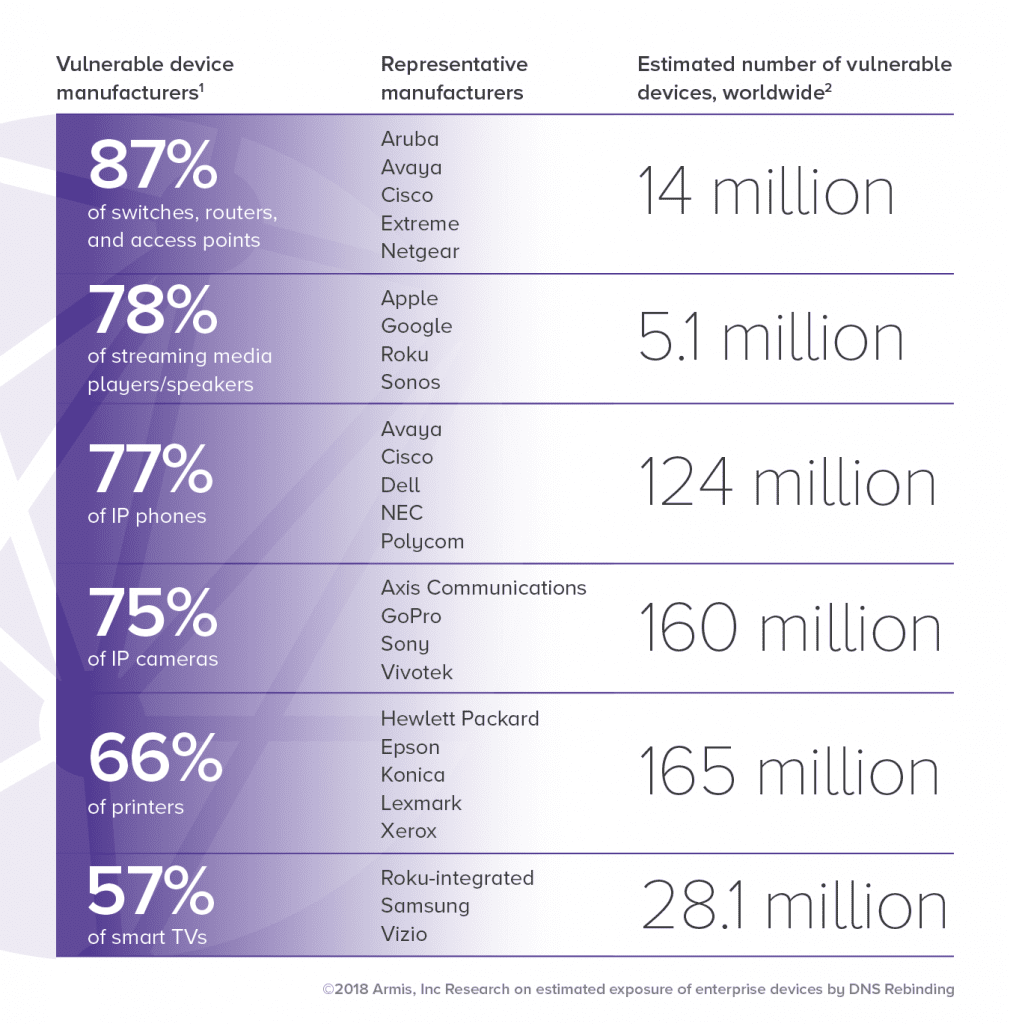
On July 20th, the Internet of Things (IoT) security provider Armis released a research report saying that about 496 million enterprise devices are facing the risk of DNS rebinding attacks.
A study released by Armis in June revealed that consumer devices are vulnerable to DNS rebinding attacks. In July, Armis launched an investigation into enterprise-class devices to explore whether the veteran attack method poses a threat to enterprise device security. DNS rebinding attacks allow an attacker to gain access to the LAN by manipulating the DNS (Domain Name Service) mechanism.

Image: armis
Because enterprise devices are mostly located on the internal network and protected by layers of firewalls, companies often consider their devices to be unaffected by vulnerable HTTP servers. But in fact, DNS rebinding can bypass the firewall and use a machine on the intranet as a proxy to invade internal devices.
Armis is a network security provider that launched its IoT security platform in June 2017 to provide IoT device visibility and security controls. The company’s research team has disclosed other IoT risks, including the BlueBorne Bluetooth vulnerability set that was exposed in September 2017.
Armis found that about 77% of corporate Internet telephony and 66% of departmental printers face the potential risk of DNS rebinding. Besides, 87% of switches, routers, and wireless access nodes face the same risks. Armis did not directly scan the entire network to determine how many devices were vulnerable to DNS rebinding attacks. Instead, it examined its customers and used industry statistics to figure out the total number of devices affected.
The principle of DNS rebinding attack
In DNS rebinding, the local private IP address is exposed by the attacker and connected to the public network address, allowing the attacker to access the undisclosed assets and resources of the enterprise.
The attacker doesn’t even have to have a broiler on the corporate intranet.
The attacker creates a local malicious DNS server and then tricks the victim into accessing the DNS server via phishing or other attack methods. An attacker can use the victim’s web browser as a proxy to connect to other devices on the network. Once the device that should not be exposed to the public network can be accessed, the attacker can further discover and invade other potentially vulnerable assets.
How to defend against DNS rebinding
There are several ways to limit the risk of DNS rebinding attacks.
First, device manufacturers should reinforce the security level of any accessible server. The server is located on the intranet and is not a reason to relax and be safe.
Second, companies should ensure that all equipment is fully and timely patched, even if the computer is only used on the internal network. Some companies may have a misconception that devices that are not on the public network do not need to be patched. This idea is quite dangerous.
Also, DNS security agents or third-party DNS services can be used to assist in defending against DNS rebinding attacks. However, this option does not always apply. For performance or management reasons, many companies prefer to use only their local DNS servers, although the risk of using their DNS servers is even higher than that of ordinary consumers who rely on third parties in DNS rebinding attacks.