reqrypt: HTTP request tunneling tool
REQRYPT
ReQrypt is a tool for tunneling and encrypting web browser requests to hide them from local (e.g. router-level, or ISP-level) snooping and the interception. ReQrypt is useful for bypassing ISP-level URL censorship/filtering/logging systems.
ReQrypt works very differently than other bypassing methods. ReQrypt is based on a technology known as “triangular routing”. In a nutshell, ReQrypt works like this:
Basically:
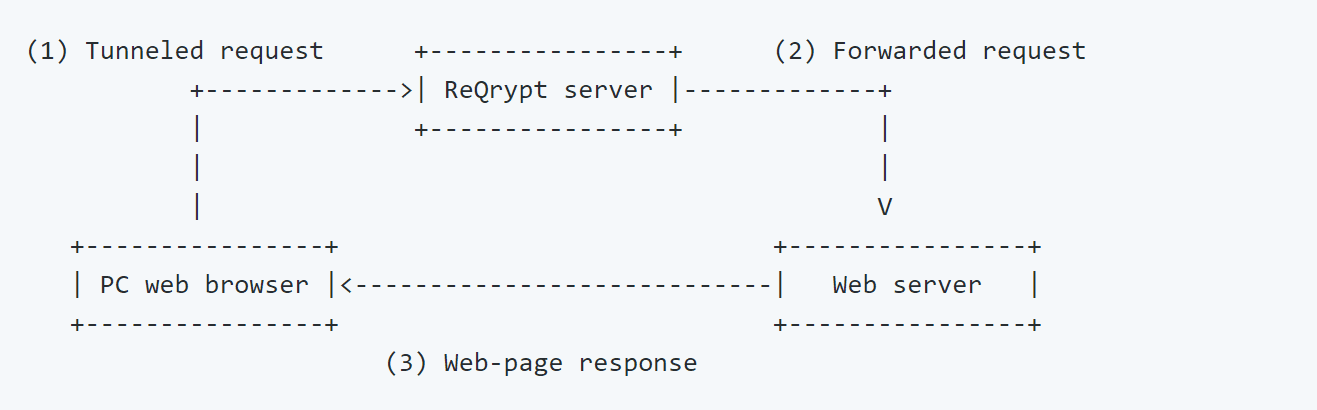
- Your web browser issues an HTTP request to the web-server, which is encrypted and tunneled to a ReQrypt server.
- The ReQrypt server decrypts the tunneled packet and forwards it to the web-server.
- The web-server responds the HTTP request as if it came directly from your computer, and the web page response is sent back via the normal route.
Ordinarily, the HTTP request is sent directly to the web server, unencrypted. This means it may be read and/or intercepted by a local eavesdropper, such as your ISP, workplace, or shared family router. However, with ReQrypt the outgoing HTTP requests are encrypted and tunneled, rendering them unreadable to any local eavesdropper.
ReQrypt is effective against systems that only attack outbound HTTP requests only, and ignore inbound HTTP responses. Such systems are very common is ISP-level censorship and logging systems, since processing URL traffic (HTTP requests) is significantly easier than processing web page responses.
Finally, unlike proxies, VPNs, Tor, etc., ReQrypt is not an anonymity tool. It does not change the IP address of the tunneled packet. This can be a good thing: it means the web responses are sent directly to your PC which means ReQrypt is typically faster than these other systems.
(C) 2018, basil00, all rights reserved.
Source: https://github.com/basil00/





