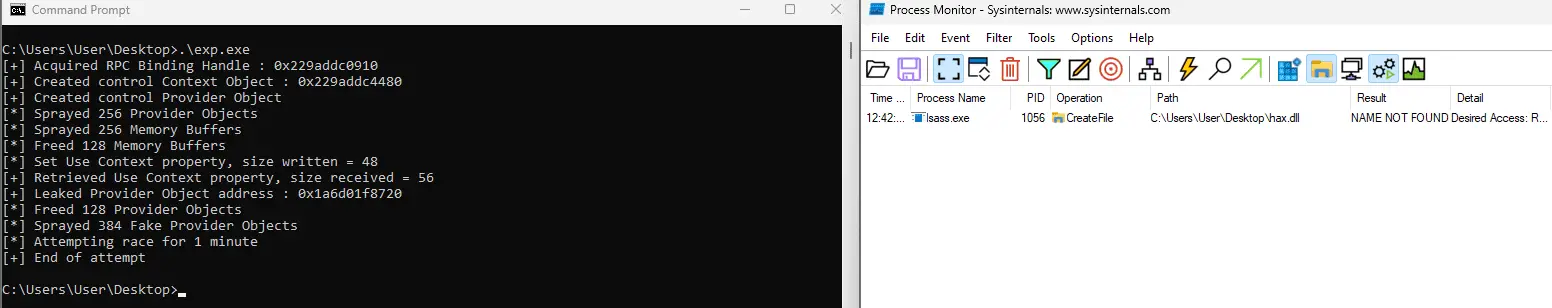
A cybersecurity researcher has released the details, and a proof-of-concept (PoC) exploit for a high-severity vulnerability (CVE-2023-28229) that exists in Windows CNG Key Isolation. The vulnerability, which has a CVSS score of 7.0, could allow an attacker to gain specific limited SYSTEM privileges.
At its core, the Windows CNG (Cryptography Next Generation) Key Isolation operates as a service beneath the lsass process. This intricate service is entrusted with providing a protective layer of isolation to private keys. Functioning as an RPC server, it is accessible via the Appcontainer Integrity process—used by applications like Adobe’s renderer or Firefox.
The vulnerability was discovered by white hat hacker k0shl of Kunlun Lab. It is a use-after-free vulnerability, which means that an attacker could free a memory object but continue to use it after it has been freed. This can lead to a variety of security problems, including denial of service attacks and privilege escalation.
k0shl, in his detailed write-up, unravels the mechanics of this flaw. He explains, “While researching the keyiso service, I discerned that each object possesses unique allocate and free interfaces. For the key object, the allocate RPC interface is titled s_SrvRpcCryptCreatePersistedKey and the free RPC interface is s_SrvRpcCryptFreeKey. A glaring discrepancy between object allocation and freeing quickly caught my attention.”
k0shl further elaborates on the sequence of events that triggers the vulnerability. The absence of a lock function during the initialization and addition stages of the key object’s reference count paves the way for the flaw. This means there exists a brief yet critical time window between the two stages, leading to premature object freeing. Such an action, coupled with subsequent checks, results in the dreaded use-after-free scenario when the function in vftable is invoked.
The proof-of-concept (PoC) exploit code for the CVE-2023-28229 vulnerability is available on GitHub. Microsoft has released a patch for this vulnerability in its April Patch Tuesday update.

To protect yourself from this vulnerability, you should install the latest security updates from Microsoft. You should also be aware of the signs of a use-after-free attack, such as unexpected system crashes or errors. If you suspect that you may have been attacked, you should contact your IT administrator immediately.