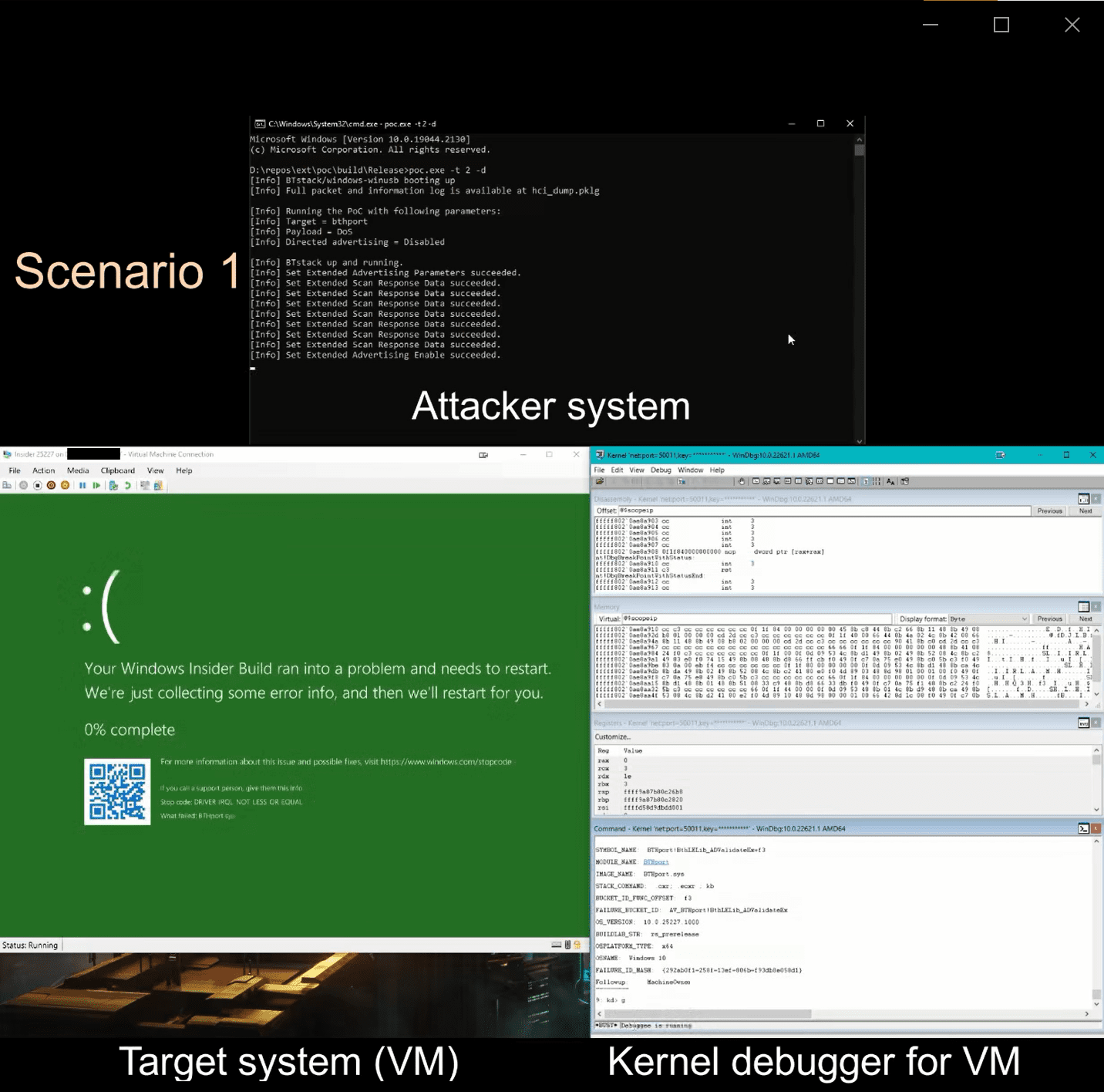
Recently, security researcher Miloš published the technical details and proof-of-concept (PoC) exploit code for a high severity vulnerability in the Bluetooth Low Energy library in Windows, designated as CVE-2023-24871. This integer overflow vulnerability, rated at a high CVSS score of 8.8, presents a significant security risk, allowing attackers to execute arbitrary code without requiring authentication.
At the heart of this vulnerability lies an integer overflow error within the code responsible for counting advertising sections in Bluetooth advertisement data packets. When a packet exceeds 255 sections, the counter overflows, leading to a miscalculation of the memory required for processing. This, in turn, triggers a heap-based out-of-bounds write, effectively handing attackers a powerful tool to manipulate a device’s memory.
The impact of this vulnerability is far-reaching due to the static linking of the vulnerable library into multiple modules within the Windows Bluetooth stack. This includes kernel drivers and usermode DLLs used by privileged services, amplifying the potential for both remote code execution (RCE) and local privilege escalation (LPE) attacks.
How It Works:
- Counting Sections: The function counts the sections in the advertisement data using an 8-bit integer.
- Integer Overflow: When the count exceeds 255, it overflows, leading to incorrect memory allocation for the sections.
- Memory Corruption: The insufficient memory allocation results in out-of-bounds writes as the function continues to parse the data, causing memory corruption.
Miloš’s detailed analysis sheds light on the exploitability of this vulnerability, demonstrating the attacker’s ability to control the amount of allocated data and manipulate out-of-bounds writes. A proof-of-concept (PoC) published on GitHub further reinforces the severity of the CVE-2023-24871 flaw, showcasing how attackers can leverage programmable Bluetooth devices to launch remote attacks.
Although Miloš did not fully weaponize the vulnerability into a working exploit, the PoC serves as a stark warning of the potential consequences if left unaddressed.
Microsoft acknowledged the vulnerability and released a patch in its March 2023 Patch Tuesday update. However, the patch only addressed the RCE aspect, leaving the LPE component unpatched. This oversight raises concerns about the thoroughness of Microsoft’s response and the potential for attackers to exploit the remaining vulnerability to gain elevated privileges on a compromised system.
Furthermore, the fix introduced a limitation on the number of advertising sections allowed in a Bluetooth packet, deviating from the Bluetooth standard. While this limitation is unlikely to affect most users, it does raise questions about Microsoft’s adherence to industry standards and potential compatibility issues.