Two security researchers Rahul Maini & Harsh Jaiswal from Project Discovery have shared technical details about a now-fixed, actively exploited critical security vulnerability affecting Atlassian’s Confluence Server and Data Center.
CVE-2023-22527, a flaw that packs a punch with a CVSS score of 10.0, signifies maximum severity. It affects a slew of versions from 8.0.x to 8.5.3, sparing the 7.19.x LTS versions. The vulnerability’s essence lies in a template injection on outdated Confluence Data Center and Server versions, potentially allowing an unauthenticated attacker to execute remote code (RCE) on the affected system.
The journey to uncovering this vulnerability was marked by meticulous analysis. Maini and Jaiswal embarked on a patch diffing expedition between versions 8.5.4 and 8.5.3, navigating through file changes and potential vulnerabilities. Their focus sharpened on files with OGNL-related changes and the OGNL Injection risk through functions like findValue and translateVariables.
The researchers’ tenacity paid off when they found that certain template files accepted parameters and passed them to potentially dangerous sinks. For example, in `confluence/template/xhtml/pagelist.vm`, the researchers successfully manipulated the $parameters object to trigger OGNL injection, a critical step toward exploitation.
In an intriguing turn of events, the researchers discovered that by escaping out of the getText function call and appending controlled OGNL syntax, they could trigger Blind OGNL expression evaluation. This was a crucial breakthrough, as it paved the way for remote code execution via OGNL Injection.
The exploit journey culminated in the researchers’ ability to bypass security restrictions set by Struts, the underlying framework used by Confluence. By exploiting the `.KEY_velocity.struts2.context` key within the `#request` map, they accessed and invoked critical OGNL functions, inching closer to executing arbitrary code.

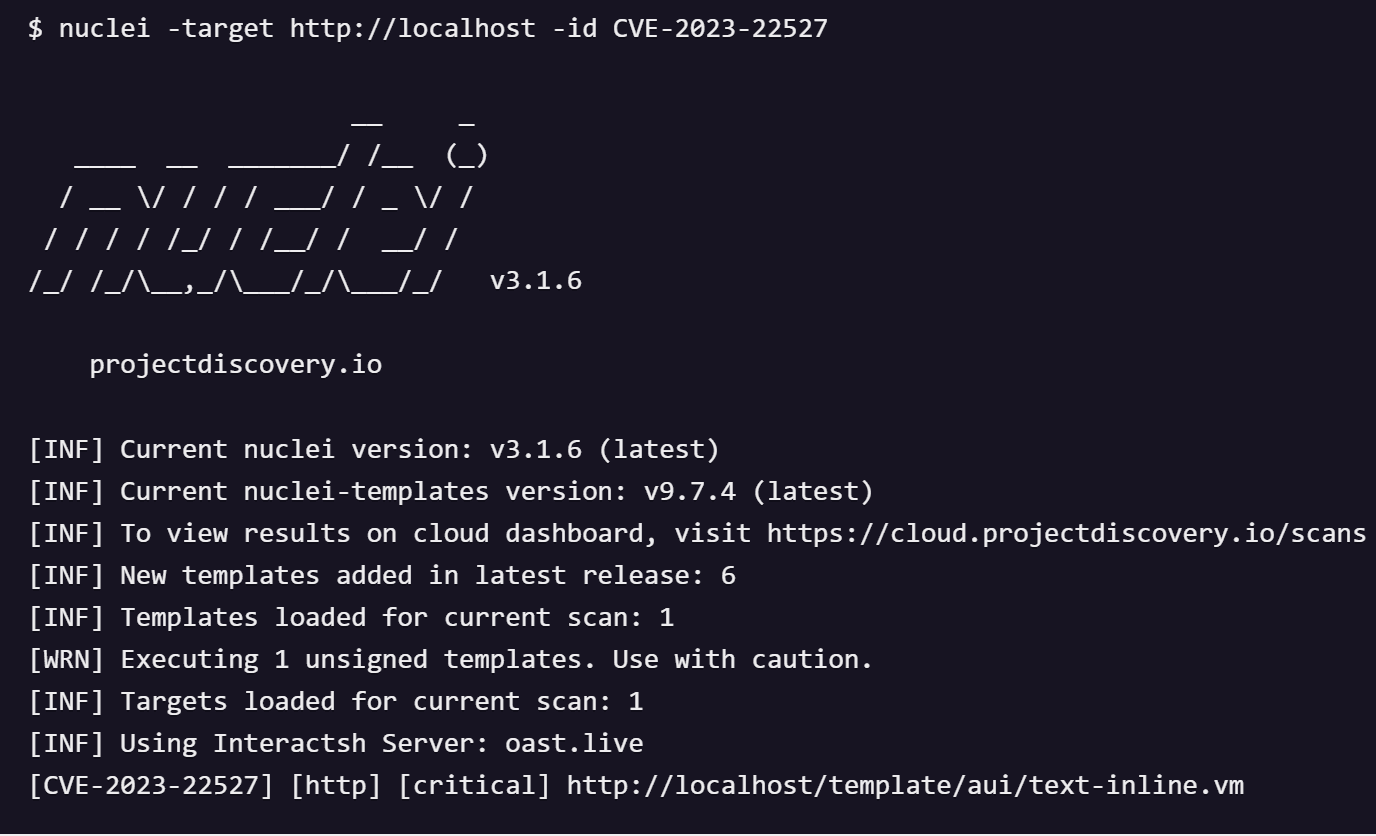
Due to the high risk of CVE-2023-22527, Atlassian has addressed the issue in recent versions. Users are urged to update their Confluence installations to the latest version to protect against this vulnerability. Furthermore, the researchers have created a nuclei template to detect CVE-2023-22527, contributing to the community’s collective defense against such cyber threats.