Image: ClearSky Research Team
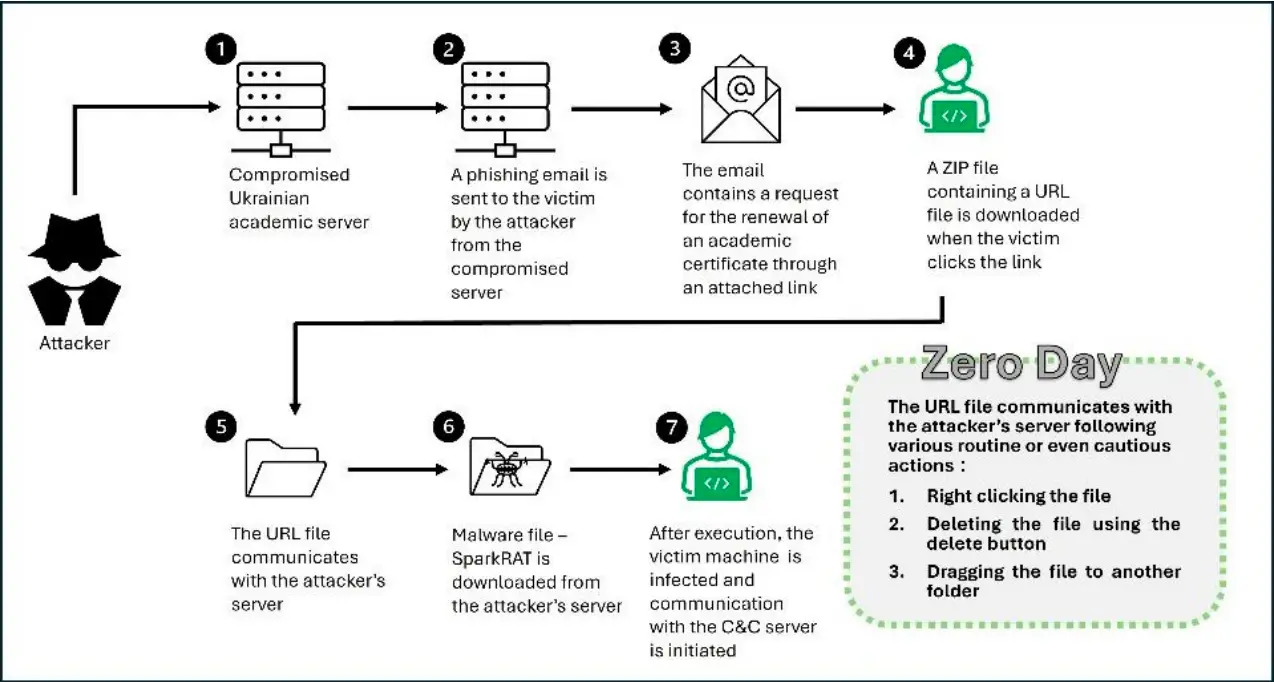
ClearSky Cyber Security has uncovered a new zero-day vulnerability, CVE-2024-43451, actively exploited in the wild, targeting Windows systems primarily in Ukraine. This flaw enables attackers to exploit URL files for malicious activity by performing actions as simple as a single right-click.
The vulnerability is activated by a specific manipulation of URL files downloaded from a Ukrainian government site, initially intended for users to obtain academic certificates. ClearSky researchers discovered that “the malicious files were downloaded from an official Ukrainian government site,” and that the files could execute commands that connect to a remote server with just one right-click, dragging, or deletion. Such simplicity in activation amplifies the risk, making it incredibly easy for users to unknowingly initiate the exploit.
ClearSky’s report reveals that the threat actors involved are likely linked to UAC-0194, a group suspected of having Russian affiliations. According to ClearSky, “CERT-UA shared technical information,” which indicated that the exploit is used as part of a larger campaign aimed at Ukrainian entities.
This exploit utilizes the SMB (Server Message Block) protocol to establish unauthorized communication with an external server upon interaction with the infected URL file. The ClearSky team explains, “Right clicking the file establishes a connection to an external server.” Upon this interaction, attackers can obtain NTLM hashes through the SMB protocol, allowing them to impersonate the user in a method known as a “Pass-the-Hash” attack. This powerful exploit not only compromises user data but also provides attackers access to sensitive Windows resources without needing the user’s password.
The initial infection vector starts with a ZIP file containing a diploma PDF and a URL file, the latter of which is the actual malicious component. Once the file is right-clicked or dragged, it communicates with the attacker’s server. Further analysis of the network infrastructure associated with the exploit found connections to IP addresses tied to a Russian VPS provider that allows cryptocurrency payments—a possible indication of the threat actors’ attempts to obfuscate their operations.
ClearSky researchers observed that this vulnerability has been used to distribute various malware, including Redline Stealer and SparkRAT. The initial analysis showed that the ZIP files downloaded were installing SparkRAT on some systems, while later variations utilized Redline Stealer. ClearSky notes, “The similarity has two possible explanations: one attacker using different types of malware or two different threat actors exploiting the same vulnerability.”
Microsoft responded promptly to ClearSky’s findings by issuing a patch on November 12, 2024, addressing CVE-2024-43451.
The CERT-UA team, which collaborated closely with ClearSky, provided additional insights into the phishing campaign associated with this exploit. They revealed that the attackers sent phishing emails urging recipients to renew academic certificates, a tactic that lured victims into downloading and activating the compromised files.
ClearSky has released a list of Indicators of Compromise (IoCs) including SHA-256 hashes and IP addresses associated with this campaign, such as the IP 92.42.96[.]30, which researchers linked to Saltu[.]Cloud, a Russian VPS provider. Network administrators and cybersecurity professionals are encouraged to monitor for these indicators to detect potential compromises and enhance defense measures against this exploit.
Related Posts:
- Microsoft Addresses Critical Zero-Day Vulnerabilities in November Patch Tuesday
- Iranian APT hacker organisation falsifies Israeli security companies official website to implement phishing activities
- Iranian “Dream Job” Campaign Targets Aerospace Industry with SnailResin Malware