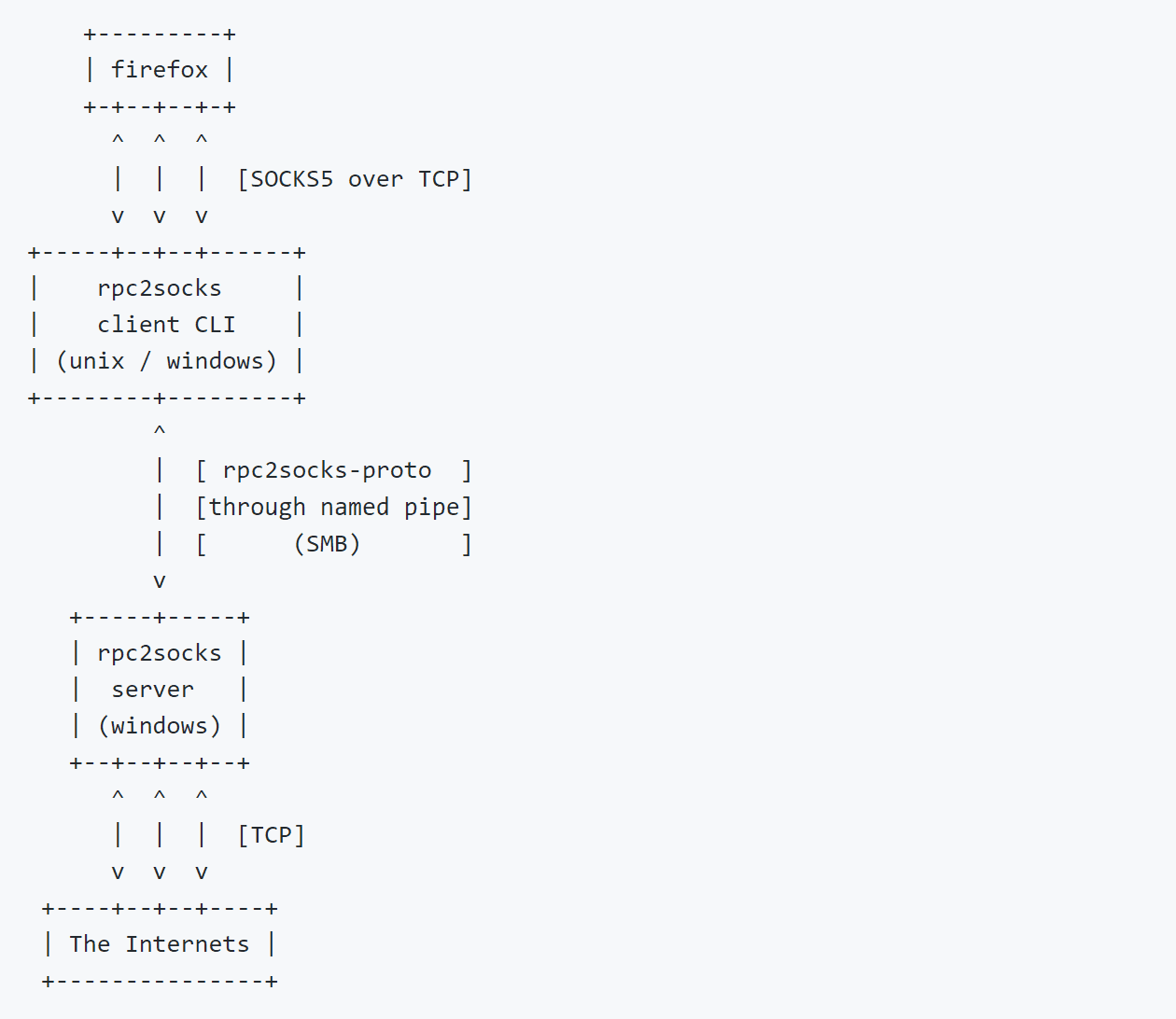
rpc2socks
rpc2socks is a client-server solution that allows us to drop and remotely run a custom RPC + SOCKS-through-SMB server application on a Windows target, from a Unix or Windows host.
The client-server pair can be used as a regular SOCKS5 tunnel (see dedicated section below).
The client and server communicate exclusively through a dedicated named pipe over SMB, using a custom and extensible protocol.
The protocol, as well as the client and server sides, can welcome additional so-called RPC commands.
rpc2socks-client is a Python3 package and an interactive script that uses an impacket to communicate with the server-side through SMB protocol (named pipe).
rpc2socks-server is implemented in C++ as a native, statically-linked, Windows console application (or a Service if enabled at compile-time), supporting both 32-bit and 64-bit architectures.
SOCKS tunnel
SOCKS-through-SMB tunnel is the main feature of rpc2socks.
Properties:
- SOCKS v5 only
- TCP only
- DNS resolution through SOCKS supported
- No authentication, however, user-password auth can be easily added in rpc2socks-server if needed
It is implemented in such a way that it allows to bounce via a Windows host except that the SOCKS proxy here takes its client-side packets from the named pipe connection established between rpc2socks-client and rpc2socks-server. With the SOCKS clients communicating directly with rpc2socks-client.
Thus, rpc2socks-server does not listen on a TCP socket.
Note that the rpc2socks-proto transport depicted here consists of a single logical link between rpc2socks-client and rpc2socks-server, regardless of the number of established SOCKS connections, and clients.
As a side note, the actual logic of the SOCKS proxy is implemented in rpc2socks-server. rpc2socks-client only acts as a bridge between the SOCKS client(s) and rpc2socks-server.
Install & Use
Copyright (c) 2020 Lexfo. All rights reserved.