RTI-Toolkit: open-source PowerShell toolkit for Remote Template Injection attacks
RTI-Toolkit
RTI-Toolkit is an open-source PowerShell toolkit for Remote Template Injection attacks. This toolkit includes a PowerShell script named PS-Templator.ps1 which can be used from both an attacking and defensive perspective.

The following tables present the main modules (cmdlets) of PS-Templator.ps1:
| Cmdlet | Description | Perspective |
|---|---|---|
| Invoke-Template | Implements remote template links within default Office Word templates | Attacking |
| Invoke-Regular | Implements remote template links within regular Office Word documents without a template | Attacking |
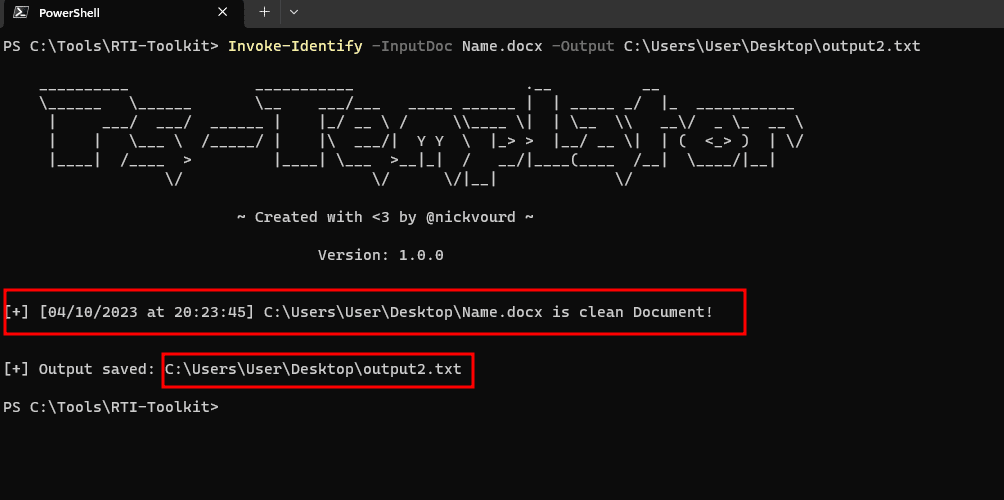
| Invoke-Identify | Identifies remote template links within Office Word docx documents with/without template | Defensive |
⚠️ PS-Templator.ps1 supports only DOCX files.
Remote Template Injection (RTI) in the context of Microsoft Office refers to a specific type of security vulnerability that can be exploited through malicious templates in Office documents (e.g., Word, Excel, PowerPoint).
For example, in a DOCX file, the content is stored in XML format within the archive, and some of these XML files may reference external resources or templates. Attackers can indeed manipulate these XML files to insert malicious links or content that can potentially exploit vulnerabilities or deceive users.
This is a Macro-Based attack.
Install & Use
Copyright (c) 2023 Nikos Vourdas





