Russia-Linked TAG-110 Launches Cyberespionage Campaign Across Asia and Europe
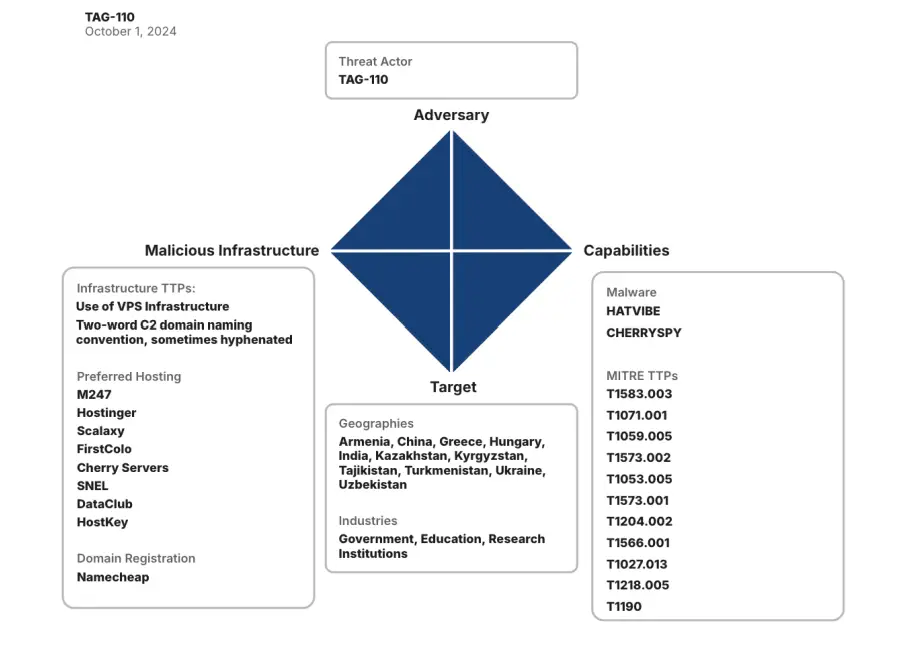
Insikt Group, the threat research division of Recorded Future, has uncovered a cyberespionage campaign attributed to TAG-110, a Russia-aligned threat activity group. This campaign, active since at least July 2024, has targeted organizations across eleven countries in Asia and Europe, with a primary focus on Central Asia.
TAG-110, which overlaps with UAC-0063 and has been linked with moderate confidence to the Russian state-sponsored group BlueDelta (APT28), has continued its operations aligned with Russia’s geopolitical interests. According to the report, “Similar to other recent Russian APT campaigns, the group likely aims to gather intelligence to support Russia’s war in Ukraine and monitor geopolitical events along Russia’s periphery.”
Since July 2024, the group has successfully targeted 62 organizations in 11 countries, primarily in Central Asia. Notable victims include the National Center for Human Rights of the Republic of Uzbekistan and a subsidiary of Kazakhstan’s state-owned oil and gas enterprise, KazMunayGas.
TAG-110’s operations are defined by its use of sophisticated custom malware.
- HATVIBE: A loader leveraging HTML Applications (HTA) to deliver additional payloads such as CHERRYSPY. Delivered via malicious email attachments or vulnerabilities in web-facing services, HATVIBE is designed for stealth. The malware employs obfuscation techniques, such as VBScript encoding and XOR encryption, to evade detection. Insikt Group highlights that “HATVIBE communicates with its hard-coded command-and-control (C2) server using an HTTP PUT request,” a tactic designed to blend in with normal web traffic.
- CHERRYSPY: This Python-based backdoor facilitates long-term espionage. Using advanced encryption methods like RSA and AES, CHERRYSPY establishes a secure communication channel with its C2 servers. Once active, it enables the exfiltration of sensitive data and allows for continuous monitoring of compromised systems.
Initial access is primarily achieved through spear-phishing and exploitation of vulnerabilities like CVE-2024-23692 in the Rejetto HTTP File Server. Post-compromise, the malware establishes persistence using scheduled tasks or system binaries, such as mshta.exe.
The campaign reflects Russia’s increasing reliance on cyber capabilities to bolster its geopolitical and military objectives. The report underscores that “the Central Asian states may be particularly important to Moscow, as its relations with many post-Soviet states in the region have deteriorated considerably following its invasion of Ukraine.”
TAG-110’s activities extend beyond espionage, with its malware infrastructure revealing a high degree of operational complexity. For instance, CHERRYSPY leverages VPS-based C2 servers registered with providers like Namecheap, masking its activities behind seemingly benign infrastructure.
The report also provides actionable intelligence, such as IoCs and YARA rules, to aid defenders in detecting and neutralizing TAG-110’s activities.





