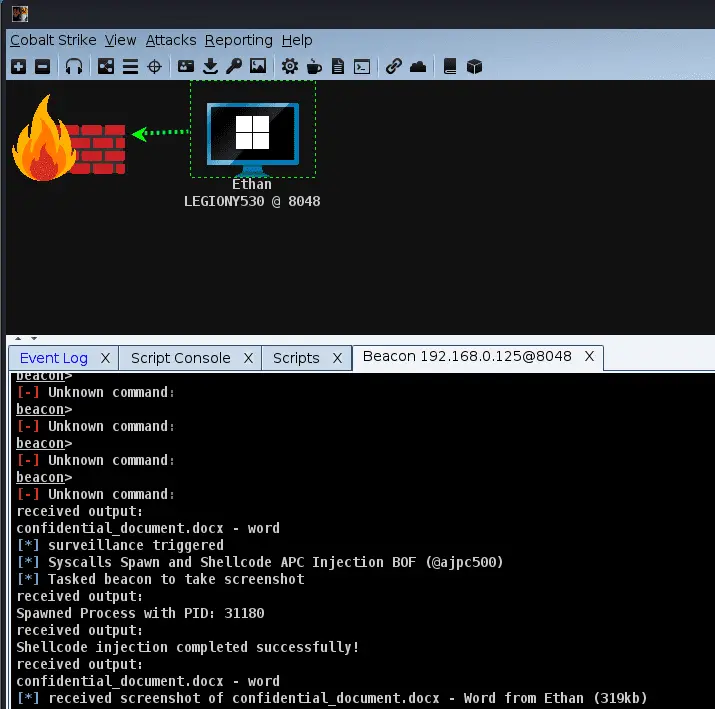
Hunt researchers have uncovered a cyber intrusion campaign targeting South Korean organizations, utilizing a sophisticated combination of tools and techniques. The campaign involves the deployment of a modified version of the Cobalt Strike penetration testing tool, delivered via a Rust-compiled loader.
The researchers identified a publicly exposed web server that contained tools linked to the intrusion campaign. The server, which was accessible for less than 24 hours, hosted a Rust-compiled Windows executable delivering Cobalt Strike Cat (CS Cat).
Alongside the modified version of Cobalt Strike, researchers found instances of open-source tools, including SQLMap, Web-SurvivalScan, and dirsearch. This suggests that the attackers leveraged these tools to identify and exploit vulnerable web applications.
-
dirsearch: A command-line tool used to brute-force directories and files on web servers, helping attackers identify hidden paths, admin panels, and exposed resources.
-
sqlmap: An automated SQL injection tool designed for detecting and exploiting SQL vulnerabilities, often used for dumping database contents and gaining unauthorized access.
-
Web-SurvivalScan: A subdomain enumeration tool that allows attackers to identify active domains within a target environment, supporting proxy integration to evade detection.
The threat actor compiled a file named “targ.txt,” listing over 1,000 Korean domains associated with government agencies, local municipalities, and private businesses. The list included domains belonging to the Ministry of Health and Welfare, regional government offices, and companies spanning multiple industries. This file was likely used as input for Web-SurvivalScan, allowing the operator to enumerate live subdomains for further analysis.
A Python script titled “urls.py,” containing Simplified Chinese comments, was also present in the directory. The script processes the output of Web-SurvivalScan queries, taking identified subdomains from “res.txt” and exporting them into a structured CSV file. This automates the organization of reconnaissance data, streamlining subdomain discovery and likely supporting follow-on exploitation efforts.
The “sqli” subfolder contained output from SQLMap, documenting SQL injection activity against multiple South Korean websites. Files “1.txt” through “4.txt” contain extracted database entries from four targeted domains. Another file, “bbs_admin.csv,” holds user credential data exfiltrated from an unnamed South Korean bulletin board system.
The threat actor used Cobalt Strike Cat, a modified variant of the post-exploitation tool based on version 4.5. Hunt.io analysts who reviewed the server’s contents explained, “Combining a Rust-compiled loader with a modified version of Cobalt Strike-first circulated on a predominantly Chinese-language hacking forum-provides a clear view of the actor’s approach to malware delivery and post-exploitation.”
Hunt researchers identified “ma.exe,” a Cobalt Strike beacon, and several .txt files, some as large as 1MB. Most of these files were Windows executables, likely staged to evade detection during download onto a victim system.
The remaining files, “88.txt,” “882.txt,” and “888.txt,” are Rust-compiled executables that serve as Cobalt Strike Cat beacon loaders. These binaries effectively act as an intermediate execution layer, decoding and running shellcode instead of dropping a standalone payload to disk.
The report indicates that some attacks may have been successful, with government and commercial entities appearing to be primary targets. To defend against similar intrusions, organizations should monitor for unusual network traffic, irregular HTTP requests, and repeated connections to external infrastructure. Given the attacker’s use of SQL injection for initial access, organizations should enforce input validation, apply security patches for web applications, and log database queries for signs of exploitation attempts.