
Elastic Security Labs has revealed a significant evolution in malware development with the discovery of GOSAR, a Golang-based rewrite of the widely recognized QUASAR Remote Access Trojan (RAT). This newly developed variant surfaced during investigations into campaigns targeting Chinese-speaking regions, where attackers used SADBRIDGE, a custom malware loader, to deploy GOSAR backdoor.
GOSAR represents a strategic shift in malware development. Elastic reports: “This is our team’s first time observing a rewrite of QUASAR in the Golang programming language.” The transition to Golang, a modern programming language, offers cross-platform capabilities, reduced detection rates, and added functionality.
The campaigns, attributed to threat group REF3864, focus on Chinese-speaking users. Attackers use malicious installers disguised as legitimate software, such as Telegram or Opera GX. A sophisticated loader leveraging DLL side-loading and injection techniques, SADBRIDGE deploys GOSAR while evading detection. GOSAR extends QUASAR’s functionality with features such as information gathering, keylogging, clipboard logging, and even Hidden VNC (HVNC) operations.
Elastic emphasizes the significance of this evolution: “A rewrite in Golang might capitalize on institutional knowledge gained over [QUASAR’s] period of use, allowing for additional capabilities without extensive retraining of previously effective tactics, techniques, and procedures (TTPs).”
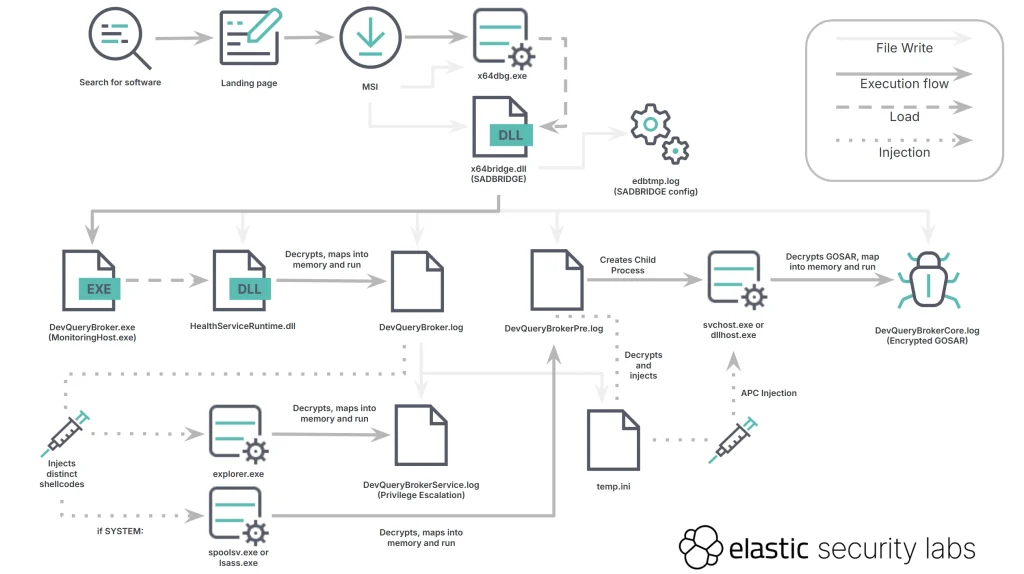
The Attack Chain
- Initial Access:
- Malicious MSI installers are distributed through fake landing pages mimicking legitimate platforms like Telegram.
- Once executed, these installers use DLL side-loading with SADBRIDGE to begin the infection.
- SADBRIDGE Execution:
- SADBRIDGE leverages legitimate applications like x64dbg.exe to load malicious DLLs, executing encrypted payloads in memory.
- Privilege escalation is achieved using techniques like UAC bypass and abuse of the Windows Task Scheduler.
- GOSAR Deployment:
- GOSAR is injected into system processes like svchost.exe or dllhost.exe.
- The malware communicates with command-and-control (C2) servers, collecting data and executing commands.
GOSAR backdoor builds on QUASAR’s core capabilities while introducing:
- Cross-Platform Support: GOSAR targets both Windows and Linux systems, reflecting the flexibility of Golang.
- Keylogging and Clipboard Monitoring: These services are initiated immediately upon connection to the C2.
- Networking Enhancements: The malware adds firewall rules and configures HTTP listeners, signaling ongoing development.
- Low Detection Rates: The use of Golang complicates signature-based detection. Elastic highlights: “This variant supports multiple platforms, including ELF binaries for Linux systems and traditional PE files for Windows. This cross-platform capability aligns with the adaptability of Go, making it more versatile than the original .NET-based QUASAR.”
SADBRIDGE and GOSAR employ several advanced evasion tactics:
- API Patching: Disables Windows security mechanisms like AMSI and Event Tracing for Windows (ETW).
- Sandbox Avoidance: Uses long Sleep API calls to thwart automated analysis.
- Encryption and Obfuscation: Configurations and payloads are encrypted, ensuring stealth.
Elastic notes: “The generic lure websites, and lack of additional targeting information, or actions on the objective, leave us with insufficient evidence to identify attacker motivation(s).” However, the transition to Golang and multi-platform targeting indicates a broader scope of potential victims and objectives.
Related Posts:
- Quasar RAT: Stealthy Data Extraction via DLL Sideloading
- Ducktail & Quasar RAT: Vietnamese Threat Actors Target Meta Ads Professionals
- C&C in the Clouds: OilRig Group Hijacks Microsoft Services for Espionage
- ViperSoftX Leverages Deep Learning with Tesseract to Exfiltrate Sensitive Information
- GoTitan Botnet Emerges Amidst Active Exploitation of Apache Vulnerability