Salsa Tools – An AV-Safe Reverse Shell
Salsa Tools is a collection of three different tools that combined, allows you to get a reverse shell on steroids in any Windows environment without even needing PowerShell for its execution. In order to avoid the latest detection techniques (AMSI), most of the components were initially written in C#. Salsa Tools was publicly released by Luis Vacas during his Talk “Inmersión en la explotación Tiene rima” which took place during h-c0n on 9th February 2019.
Feature
* TCP/UDP/ICMP/DNS/BIND/SSL/Shellcode/SilentTrinity
* AV Safe (17th February)
* AMSI patchers
* PowerShell execution
* …
Salsa-Tools is made from three different ingredients: – EvilSalsa – EncrypterAssembly – SalseoLoader And his behavior is as it follows:
Cooking EvilSalsa
EvilSalsa is the key ingredient of this recipe. It contains the payload, which is executed on the system as follows: as soon as the payloads start, it runs System.Management.Automation.dll which creates a runspace. Within that runspace we have four types of shells (TCP / UDP / ICMP / DNS / BINDTCP / SHELLCODE / SILENTTRINITY). Once EvilSalsa is loaded, first thing first, the existence of c:\windows\system32\amsi.dll is checked. If it exists, it is patched using a home-cooked variant of CyberArk and Rastamouse bypasses.
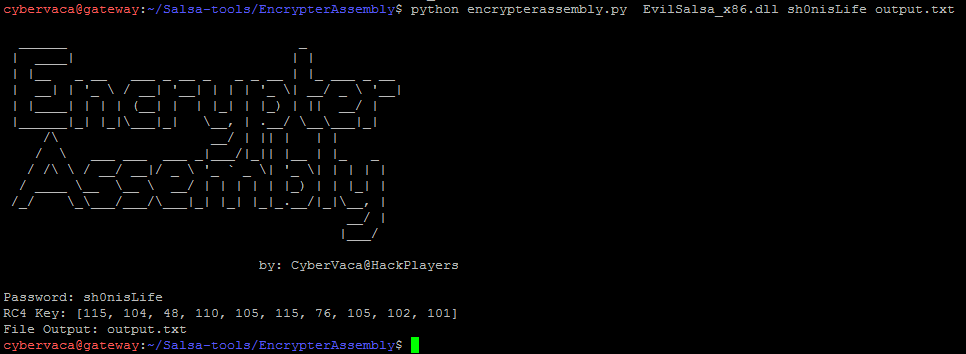
Mixing EncrypterAssembly and Evilsalsa
EncrypterAssembly can be used as a Python script or as an Exe binary. It encrypts the previously generated EvilSalsa.
Bringing the Encrypted EvilSalsa to the table with SalseoLoader
SalseoLoader is in charge of loading the encrypted payload. It can be both compiled as a library or as an executable. If it is run as an executable, the chosen arguments must be provided when the executable is run. If it is compiled as a library, the descriptor “main” must be exported. Arguments are added using environmental variables.